Slack Group
Before we get started I have started a new slack group dedicated to hacking. We welcome everyone from beginner to advanced to join. I will be on everyday answer questions, doing CTFs, and talking about cool hacks. If you enjoy hacking and are looking for like minded people join below:
NEW Hacking Group Slack Channel
Introduction
Its January 2nd, 2019 and like I always do I was checking my news feed and noticed an article about how some malicious hacker attacking chromcast which resulted in their TV being forced to render unwanted content (News Article).

This peaked my interest so I set out discover how the hacker accomplished this.
Technical Details
Recon
According to the internet the definition of chromecast is a streaming media adapter from Google that allows users to play online content such as videos and music on a digital television.
At the time of writing this post this is a hot topic so I figured I could find some more details on social media sites(twitter). After 5min of digging I discovered the following twitter post which pointed me in the right direction.
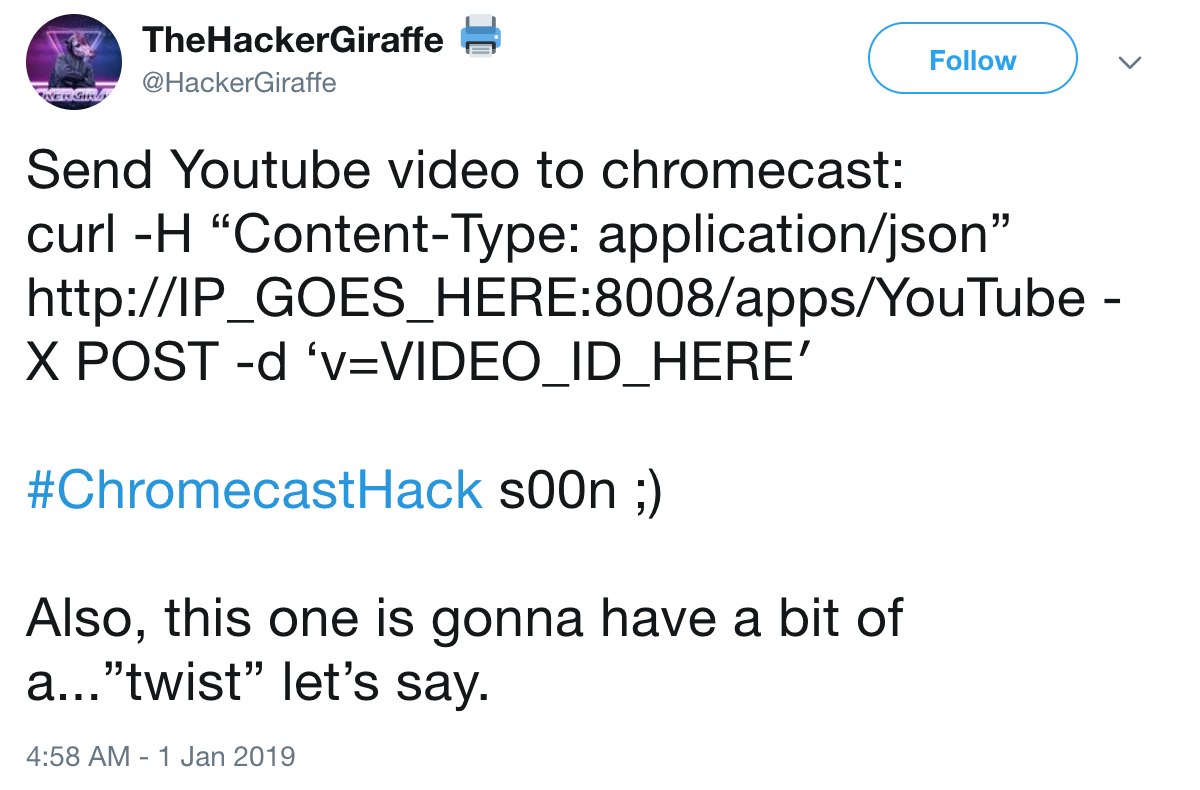
Neat so I can send a POST request to VulnWebSite.com:8008/apps/Youtube with a JSON body containing the data {?v?:?VIDEO_ID_HERE?}. So basically the vulnerability here is that any one who sends a post request to your chromcast device can make your TV play a youtube video. This is all unauthenticated.
Next I attempted to look for the API documentation but couldn?t what I wanted. I then came across the unofficial API documentation posted by someone else (API documentation). I also found other documentation listed below.
- chromecast python script
- chromecast urls list
After reading the documentation I had a much better idea of how the device worked and I pretty much knew how the hacker had pulled off the attack.
The Attack
So first we must create some sort of fingerprint to identify chromecast devices that have this API endpoint exposed. This can easily be done by sending a GET request to the /setup/eureka_info endpoint which is documented here(device-info API documentation). This will return a json object containing the build version, device info, public key, and more. This is the same api endpoint shodan.io uses to fingerprint chromcast devices.
Now that we can identify chromcast devices all we have to do is send the youtube payload to the ?/apps/YouTube? endpoint we discovered earlier. After that the users TV will be forced to play what ever video you want it to play. You can also do other things like list the surrounding access points and bluetooth devices or anything listed in the API documentation. This can all be done unauthenticated of course.
Universal Plug and Play
This attack is simple and almost anyone can pull this off armed with this knowledge. What makes things worse is that chromecast makes use of Universal Plug and Play (UPnP). If you dont know what UPnP does it basically punches a whole right through your firewall. This means that the chromecast device makes use of UPnP to open port 8008 on your router and forwards all the traffic to the chromecast device. If your router has UPnP enabled, all most all do by default, your chromecast device will be opening it self to the internet. This means anyone will be able to control your chromecast device and the TV it is connected to from the internet unauthenticated.
Conclusion
I strongly believe that google is truly a great company. They do a lot to protect us everyday and they also protect other companies and devices thanks to project zero. No matter how good you are somethings just slip through the cracks. It happens all the time. Google has already mentioned that they will be pushing a update within the coming weeks. Its probably best to block UPnP completely as there are many other IOT devices that could be vulnerable. Think about it if a google device is vulnerable to an unauthenticated API exploit how many other devices are?