Are you still robbing ATMs using cars, hammers and crowbars? Are you trying to open ATM safes in under 2 minutes before the police arrive? This is unhealthy, man. Equally for people and ATMs alike.
Uncool and dangerous
The tech-savvy ATM robbers are hacking dozens of ATMs at once and are doing it in a safe distance without harming the ATMs. Just like these guys in Japan who stole almost 13 million dollars in several hours.
 Stop harming ATMs!
Stop harming ATMs!
If you want to want know how to steal cash, and in the same time have a soft spot for ATM?s this article highlights 7 ways to steal cash from an ATM using your PC without harming anyone or anything.
But before we start, let?s have a look at how an ATM works.
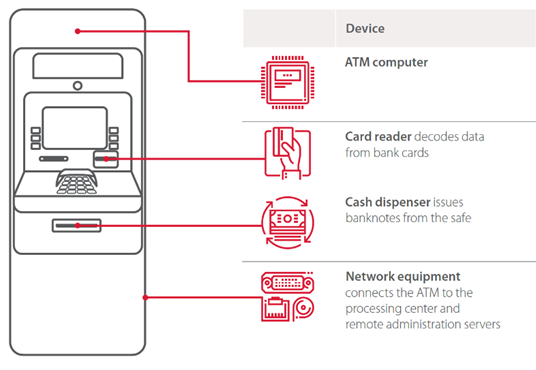
What?s inside an ATM (besides cash)?
Almost every ATM consists of two main parts 1) The cabinet which contains the computer, network equipment, card reader, keyboard, and other devices. 2) The safe which has the cash and cash dispenser inside.
The cabinet is usually protected only with a thin door and a cheap lock. The safe is protected by steel and concrete and is not easy to lock pick or break.
So its much easier for hackers to get inside the cabinet which has a PC inside. It usually has an outdated Windows onboard (not sure about now but several years ago, 95% of ATMs were operated by Windows XP). The PC is using XFS protocol (a protocol developed in the ?90s) to communicate with all the peripheral devices such as the card reader, PIN PAD and cash dispenser. All this is controlled by a banking application that connects through encrypted (not always) communications to the bank network.
This sounds like a lot of fun for hackers to be creative! They often participate in playful competitions focused on hacking ATMs. And It?s really tempting to hack an ATM when you see stuff like this in the wild:
 Please hack me! See more fun examples in this presentation by Kaspersky Lab ATM hacking experts
Please hack me! See more fun examples in this presentation by Kaspersky Lab ATM hacking experts
But I am getting ahead of myself. Let?s keep in mind those three main components in the cabinet which could be attacked by a hacker to get cash:
- ATM main computer
- Cash dispenser and other peripheral devices
- Network equipment
So with this in mind let us have a look at 7 ways to trick the ATM to give us cash in a peaceful way.
7 ways to hack an ATM and get cash
So depending on ATM model, configuration and other factors (for example ready-to-use ATM hacking kits purchased in the darknet), you can hack an ATM using one of the following ways:
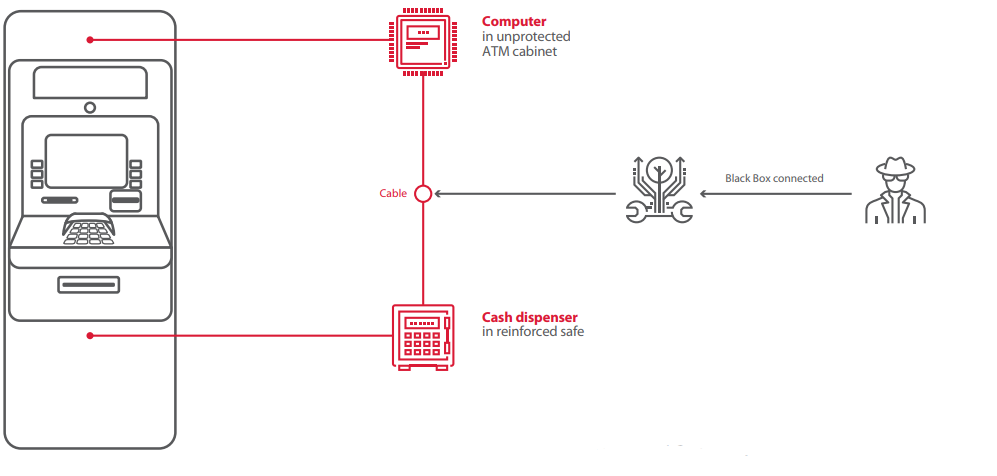
1) Use a Blackbox
A Blackbox attack is when you use a device with a computer inside which takes the place of the ATM main computer and intercepts control of all peripheral devices, such as cash dispenser.
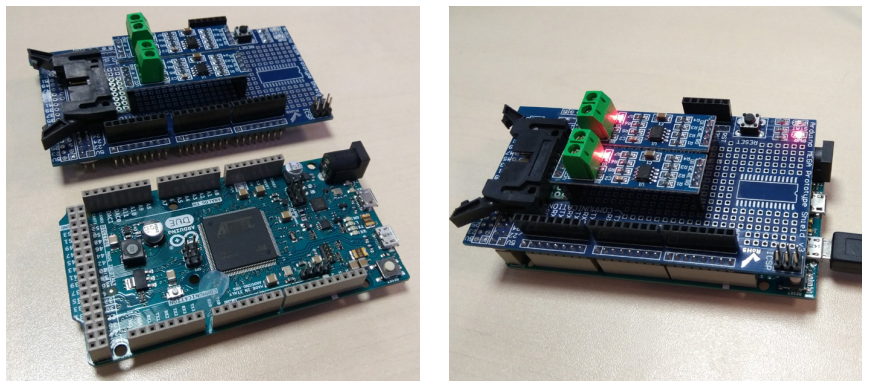 A Blackbox device based on a Raspberry Pi platform
A Blackbox device based on a Raspberry Pi platform
The cash dispenser is located in the safe and not accessible, but it is connected to the ATM computer in the cabinet. So you need to find a way to connect directly to the cash dispenser and control it using anything from a laptop to a tiny Raspberry Pi. In some cases, you don?t even need to get access to the cabinet. For example, the criminals here just drilled a hole in a specific place to get access to the cash dispenser cable, because they knew where it is located.
You don?t even need to know how to build a custom black box, you can just buy it in the darknets.
If you are interested to know more about Blackbox attacks, here is a recent presentation on the last trends from the last Blackhat by security researchers Alexey Stennikov and Vladimir Kononovich.
2) Control the ATM computer
Or in other words, Exit the Kiosk mode. ATM usually runs one application which we see on the screen when we use it. It runs on Windows in full-screen mode and processes inputs from the user not allowing to interact with anything else in the operating system. This is called the Kiosk mode and there are several ways to bypass this mode and get access to the operating system gaining control over the ATM. If you have an urgent need to play Angry Birds, for example:
How can you achieve this? One scenario for example:
- First, dress like an ATM service engineer, obtain an ATM lock key or drill a hole where a USB drive is located.
- Use a small computer (like Rasberry Pi, Teensy or an old laptop) to emulate keyboard user input and connect it to a USB pr PS/2 interface of the ATM computer. Chances are that there is no control of connected external devices. And if you are using a computer with a 3G-module, you can now leave the hardware inside the ATM and do the rest from a safe distance.
- Use hotkeys or menu to get access to other applications. There are usually no restrictions on input.
4. You need to bypass application control to control the ATM after that. Which sounds like not an easy task, but it is not impossible.
Recently PT experts found vulnerabilities in such security software as McAfee Solid Core, Kaspersky Embedded Systems Security, and other security software
But don?t worry if you are not a skilled hacker or security researcher, potentially, there are ways to bypass security exploiting misconfiguration or security policy flaws. Meaning even if the security software is installed properly and not vulnerable, there is still a big chance that some helpful software was white-listed by the security software and you would be free to use it. For example, FAR file manager or power shell in ATMs operated on Windows 7, they are usually white-listed because this software is also used by ATM service engineers.
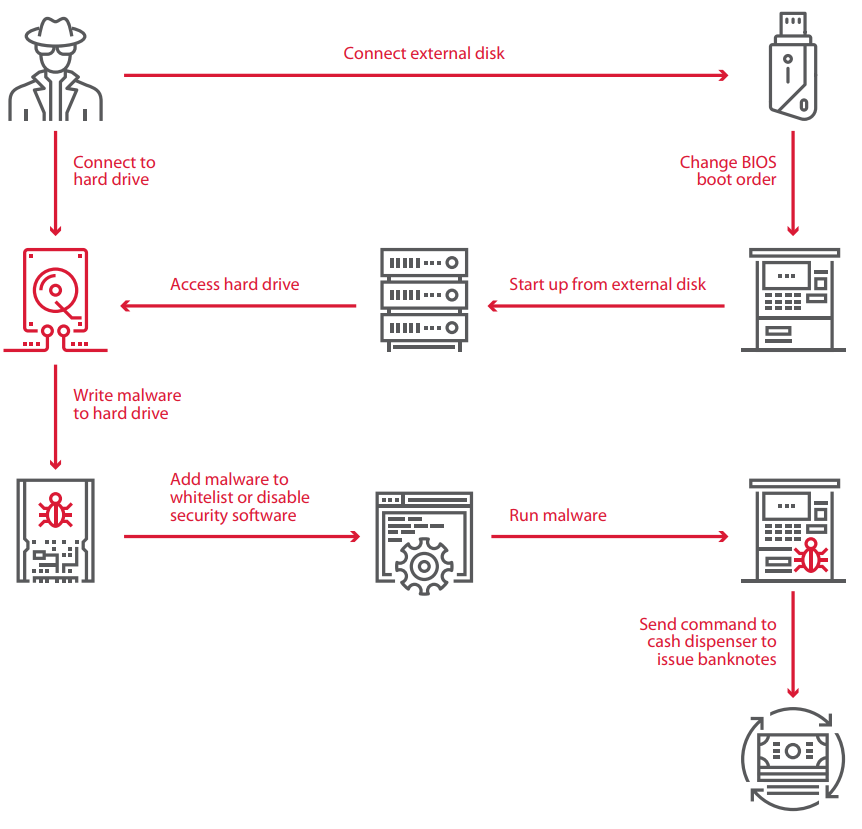
3) Connect to the hard drive directly
If the hard drive in your victim ATM is not encrypted, this is the simplest way to gain control. You can just infect the ATM with a malware and control the whole ATM network or disable the security software. Here is an example of such malware with a big list of multi-million profits.
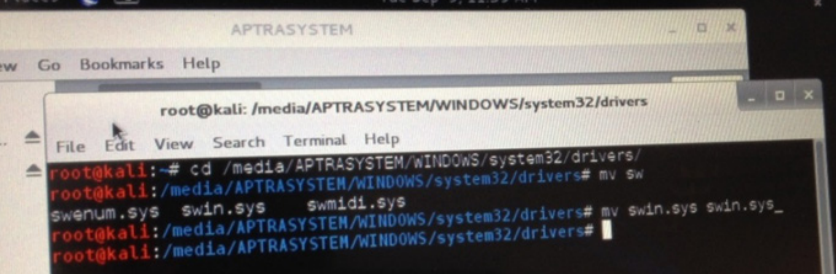 Disable security system simply by renaming the driver
Disable security system simply by renaming the driver
4) Boot from your own hard drive
It is even more fun if the BIOS settings are protected by an easy to guess password (Almost in 30% of the times they are, or they were easy to guess) you just make an external bootable flash drive as the primary boot device and use it to control the cash dispenser.
 Connecting to a hard drive to copy a malware
Connecting to a hard drive to copy a malware
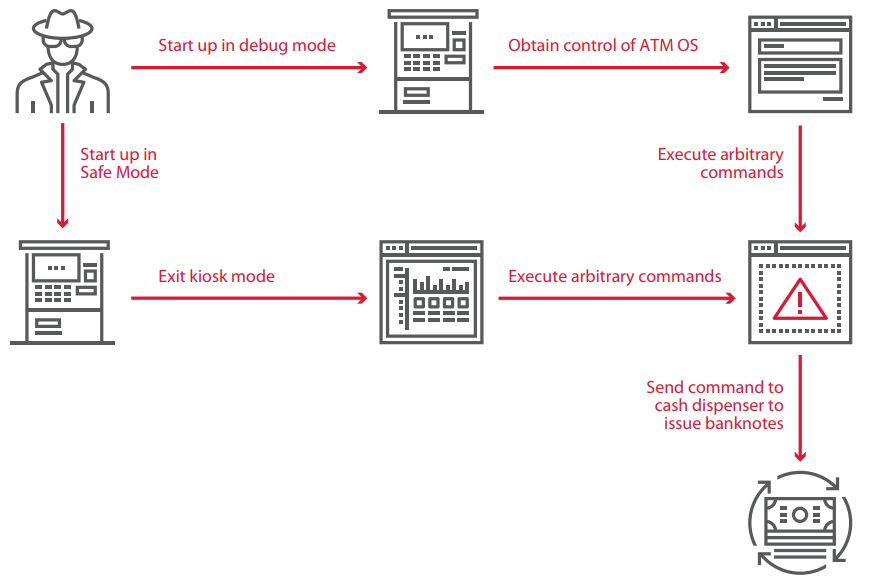
5) Change Boot mode
You can also bypass ATM security systems by loading the operating system in the ?safe mode?. Usually, a lot of security features are disabled in this mode.
6) Pretend to be the processing center (spoofing)
If the communication between the ATM and processing center is not secured or you are able to bypass the security then you can emulate processing and send commands to dispense cash to the ATM.
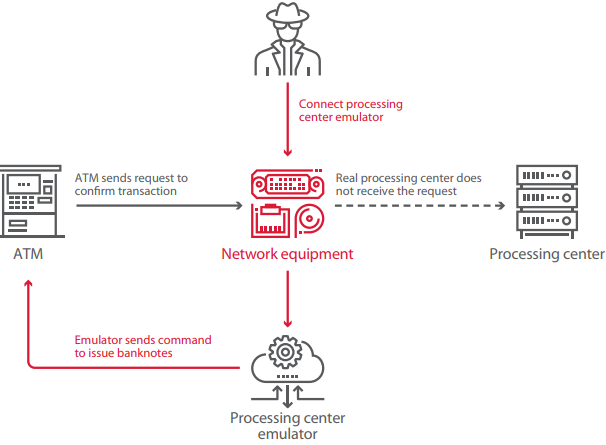 Spoofing processing center
Spoofing processing center
This can be achieved if the following conditions are met:
- Data between the processing center an ATM is not encrypted
- VPN protection is poorly implemented (especially if it?s an external hardware)
- Message authentication Codes are not used in transaction requests and responses (meaning you can alter the data without being detected).
This attack was possible 27% of ATMs tested by PT.
7) Exploit vulnerable network devices
There is a high chance that the ATM is using some network device with vulnerabilities unaccounted for. In some cases, the network devices are even accessible from outside the ATM cabinet.
In one case, which was described by Positive Technologies, an ATM was using a GSM modem to connect to the bank processing. they were using a secure protocol to communicate in an encrypted way. The encryption was based on a host key which was encrypted, in turn, by another key stored in the modem firmware. Guess what happened after the security researchers had their hands on this modem and found the encryption key?
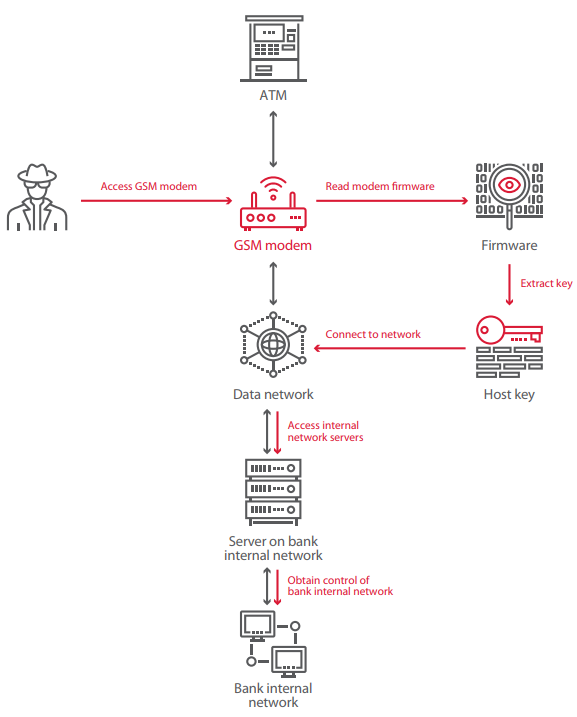
Exactly, they were able to get access to any host in the internal network of the bank. Sometimes, you can find GSM modems or other network devices with default credentials used in them.
Even if you don?t have access to the modem itself, you can try creating a fake GSM base station and trick the modem connect to you. In some cases, there might be Telnet or web interfaces welcoming you.
Ok got it. What?s next?
If you use any of those methods described, be aware that most probably you will end like this:
 https://krebsonsecurity.com/2014/05/thieves-planted-malware-to-hack-atms/
https://krebsonsecurity.com/2014/05/thieves-planted-malware-to-hack-atms/
I was joking, don?t steal money. Especially, if you are curious enough to find vulnerabilities in ATM systems. Instead join Positive Technologies and other security firms in our quest to make the world a safer place.
This article is a summary of a report done by Positive Technologies. It was based on real projects completed in banks who care about their security. All attacks are performed on real ATMs (sometimes in the streets) within 10 to 20 minutes for every attack. Check the report if you are interested in more details and follow Tim Yunusov & Leigh-Anne Galloway if you want to know more about cash & security.