Bandit Level 0 ? Level 1
Level GoalThe goal of this level is for you to log into the game using SSH. The host to which you need to connect is bandit.labs.overthewire.org, on port 2220. The username is bandit0 and the password is bandit0. Once logged in, go to the Level 1 page to find out how to beat Level 1.
? ~ ssh [email protected] -p 2220bandit0@melinda:~$ lsreadmebandit0@melinda:~$ cat readmeboJ9jbbUNNfktd78OOpsqOltutMc3MY1bandit0@melinda:~$
Bandit Level 1? Level 2
Level GoalThe password for the next level is stored in a file called ? located in the home directory
? ~ ssh [email protected] -p 2220bandit1@melinda:~$ ls-bandit1@melinda:~$ cat ./-CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9bandit1@melinda:~$
Referenceshttps://www.google.com/search?q=dashed+filenamehttp://tldp.org/LDP/abs/html/special-chars.html
Bandit Level 2 ? Level 3
Level GoalThe password for the next level is stored in a file called spaces in this filename located in the home directory
? ~ ssh [email protected] -p 2220bandit2@melinda:~$ lsspaces in this filenamebandit2@melinda:~$ cat spaces in this filenameUmHadQclWmgdLOKQ3YNgjWxGoRMb5luKbandit2@melinda:~$
Referenceshttps://www.google.com/search?q=spaces+in+filename
Bandit Level 3 ? Level 4
Level GoalThe password for the next level is stored in a hidden file in the inhere directory.
? ~ ssh [email protected] -p 2220bandit3@melinda:~$ lsinherebandit3@melinda:~$ cd inhere/bandit3@melinda:~/inhere$ ls -latotal 12drwxr-xr-x 2 root root 4096 Nov 14 2014 .drwxr-xr-x 3 root root 4096 Nov 14 2014 ..-rw-r—– 1 bandit4 bandit3 33 Nov 14 2014 .hiddenbandit3@melinda:~/inhere$ cat .hiddenpIwrPrtPN36QITSp3EQaw936yaFoFgABbandit3@melinda:~/inhere$
Bandit Level 4 ? Level 5
Level GoalThe password for the next level is stored in the only human-readable file in the inhere directory. Tip: if your terminal is messed up, try the ?reset? command.
? ~ ssh [email protected] -p 2220bandit4@melinda:~$ lsinherebandit4@melinda:~$ cd inhere/bandit4@melinda:~/inhere$ ls -latotal 48-rw-r—– 1 bandit5 bandit4 33 Nov 14 2014 -file00-rw-r—– 1 bandit5 bandit4 33 Nov 14 2014 -file01-rw-r—– 1 bandit5 bandit4 33 Nov 14 2014 -file02-rw-r—– 1 bandit5 bandit4 33 Nov 14 2014 -file03-rw-r—– 1 bandit5 bandit4 33 Nov 14 2014 -file04-rw-r—– 1 bandit5 bandit4 33 Nov 14 2014 -file05-rw-r—– 1 bandit5 bandit4 33 Nov 14 2014 -file06-rw-r—– 1 bandit5 bandit4 33 Nov 14 2014 -file07-rw-r—– 1 bandit5 bandit4 33 Nov 14 2014 -file08-rw-r—– 1 bandit5 bandit4 33 Nov 14 2014 -file09drwxr-xr-x 2 root root 4096 Oct 19 2016 .drwxr-xr-x 3 root root 4096 Nov 14 2014 ..bandit4@melinda:~/inhere$bandit4@melinda:~/inhere$ cat ./-file07koReBOKuIDDepwhWk7jZC0RTdopnAYKhbandit4@melinda:~/inhere$
Bandit Level 5 ? Level 6
Level GoalThe password for the next level is stored in a file somewhere under the inhere directory and has all of the following properties:human-readable1033 bytes in sizenot executable
? ~ ssh [email protected] -p 2220bandit5@melinda:~$ lsinherebandit5@melinda:~$ cd inhere/bandit5@melinda:~/inhere$ ls -latotal 88drwxr-x— 22 root bandit5 4096 Nov 14 2014 .drwxr-xr-x 3 root root 4096 Nov 14 2014 ..drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere00drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere01drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere02drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere03drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere04drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere05drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere06drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere07drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere08drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere09drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere10drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere11drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere12drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere13drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere14drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere15drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere16drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere17drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere18drwxr-x— 2 root bandit5 4096 Nov 14 2014 maybehere19bandit5@melinda:~/inhere$ find . -type f -readable ! -executable -size 1033c./maybehere07/.file2bandit5@melinda:~/inhere$ cat ./maybehere07/.file2DXjZPULLxYr17uwoI01bNLQbtFemEgo7bandit5@melinda:~/inhere$
Bandit Level 6 ? Level 7
Level GoalThe password for the next level is stored somewhere on the server and has all of the following properties:owned by user bandit7owned by group bandit633 bytes in size
? ~ ssh [email protected] -p 2220bandit6@melinda:~$ find / -user bandit7 -group bandit6 -size 33c 2>/dev/null/var/lib/dpkg/info/bandit7.passwordbandit6@melinda:~$ cat /var/lib/dpkg/info/bandit7.passwordHKBPTKQnIay4Fw76bEy8PVxKEDQRKTzsbandit6@melinda:~$
Bandit Level 7 ? Level 8
Level GoalThe password for the next level is stored in the file data.txt next to the word millionth
? ~ ssh [email protected] -p 2220bandit7@melinda:~$ lsdata.txtbandit7@melinda:~$ cat data.txt | grep “millionth”millionth cvX2JJa4CFALtqS87jk27qwqGhBM9plVbandit7@melinda:~$
Bandit Level 8 ? Level 9
Level GoalThe password for the next level is stored in the file data.txt and is the only line of text that occurs only once
? ~ ssh [email protected] -p 2220bandit8@melinda:~$ lsdata.txtbandit8@melinda:~$ cat data.txt | sort | uniq -uUsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhRbandit8@melinda:~$
Referenceshttp://www.westwind.com/reference/os-x/commandline/pipes.html
Bandit Level 9 ? Level 10
Level GoalThe password for the next level is stored in the file data.txt in one of the few human-readable strings, beginning with several ?=? characters.
? ~ ssh [email protected] -p 2220bandit9@melinda:~$ lsdata.txtbandit9@melinda:~$ strings data.txt | grep “=”epr~F=K7?YD=?M=HqAH/(Ne=C=_”I========== the6z5Y=`h(8=`nH=;========== password========== ismN$=&l/a=L)f=C(========== truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLkie)=5ebandit9@melinda:~$
Bandit Level 10 ? Level 11
Level GoalThe password for the next level is stored in the file data.txt, which contains base64 encoded data
? ~ ssh [email protected] -p 2220bandit10@melinda:~$ lsdata.txtbandit10@melinda:~$ cat data.txtVGhlIHBhc3N3b3JkIGlzIElGdWt3S0dzRlc4TU9xM0lSRnFyeEUxaHhUTkViVVBSCg==bandit10@melinda:~$ cat data.txt | base64 –decodeThe password is IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPRbandit10@melinda:~$
Referenceshttps://en.wikipedia.org/wiki/Base64
Bandit Level 11 ? Level 12
Level GoalThe password for the next level is stored in the file data.txt, where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions
? ~ ssh [email protected] -p 2220bandit11@melinda:~$ lsdata.txtbandit11@melinda:~$ cat data.txtGur cnffjbeq vf 5Gr8L4qetPEsPk8htqjhRK8XSP6x2RHhbandit11@melinda:~$ cat data.txt | tr ‘[A-Za-z]’ ‘[N-ZA-Mn-za-m]’The password is 5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUubandit11@melinda:~$
Referenceshttps://en.wikipedia.org/wiki/ROT13
Bandit Level 12 ? Level 13
Level GoalThe password for the next level is stored in the file data.txt, which is a hexdump of a file that has been repeatedly compressed. For this level it may be useful to create a directory under /tmp in which you can work using mkdir. For example: mkdir /tmp/myname123. Then copy the datafile using cp, and rename it using mv (read the manpages!)
? ~ ssh [email protected] -p 2220bandit12@melinda:~$ lsdata.txtbandit12@melinda:~$ mkdir /tmp/kan1shka9bandit12@melinda:~$ cp data.txt /tmp/kan1shka9bandit12@melinda:~$ cd /tmp/kan1shka9bandit12@melinda:/tmp/kan1shka9$ lsdata.txtbandit12@melinda:/tmp/kan1shka9$ file data.txtdata.txt: ASCII textbandit12@melinda:/tmp/kan1shka9$ xxd -r data.txt > data_xxd_reversebandit12@melinda:/tmp/kan1shka9$ file data_xxd_reversedata_xxd_reverse: gzip compressed data, was “data2.bin”, from Unix, last modified: Fri Nov 14 10:32:20 2014, max compressionbandit12@melinda:/tmp/kan1shka9$ zcat data_xxd_reverse > data_zcatbandit12@melinda:/tmp/kan1shka9$ file data_zcatdata_zcat: bzip2 compressed data, block size = 900kbandit12@melinda:/tmp/kan1shka9$ bzip2 -d data_zcatbzip2: Can’t guess original name for data_zcat — using data_zcat.outbandit12@melinda:/tmp/kan1shka9$ file data_zcat.outdata_zcat.out: gzip compressed data, was “data4.bin”, from Unix, last modified: Fri Nov 14 10:32:20 2014, max compressionbandit12@melinda:/tmp/kan1shka9$ lsdata.txt data_xxd_reverse data_zcat.outbandit12@melinda:/tmp/kan1shka9$ zcat data_zcat.out > data_zcat_2bandit12@melinda:/tmp/kan1shka9$ file data_zcat_2data_zcat_2: POSIX tar archive (GNU)bandit12@melinda:/tmp/kan1shka9$ tar xvf data_zcat_2data5.binbandit12@melinda:/tmp/kan1shka9$ file data5.bindata5.bin: POSIX tar archive (GNU)bandit12@melinda:/tmp/kan1shka9$ tar xvf data5.bindata6.binbandit12@melinda:/tmp/kan1shka9$ file data6.bindata6.bin: bzip2 compressed data, block size = 900kbandit12@melinda:/tmp/kan1shka9$ bzip2 -d data6.binbzip2: Can’t guess original name for data6.bin — using data6.bin.outbandit12@melinda:/tmp/kan1shka9$ file data6.bin.outdata6.bin.out: POSIX tar archive (GNU)bandit12@melinda:/tmp/kan1shka9$ tar xvf data6.bin.outdata8.binbandit12@melinda:/tmp/kan1shka9$ file data8.bindata8.bin: gzip compressed data, was “data9.bin”, from Unix, last modified: Fri Nov 14 10:32:20 2014, max compressionbandit12@melinda:/tmp/kan1shka9$ zcat data8.bin > data8_zcatbandit12@melinda:/tmp/kan1shka9$ file data8_zcatdata8_zcat: ASCII textbandit12@melinda:/tmp/kan1shka9$ cat data8_zcatThe password is 8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYLbandit12@melinda:/tmp/kan1shka9$
Key Takeaways
gzip decompress
$ zcat in_file > out_file
bzip2 decompress
$ bzip2 -d file
tar decompress
$ tar xvf file
Referenceshttps://en.wikipedia.org/wiki/Hex_dump
Bandit Level 13 ? Level 14
Level GoalThe password for the next level is stored in /etc/bandit_pass/bandit14 and can only be read by user bandit14. For this level, you don?t get the next password, but you get a private SSH key that can be used to log into the next level. Note: localhost is a hostname that refers to the machine you are working on
? ~ ssh [email protected] -p 2220bandit13@melinda:~$ lssshkey.privatebandit13@melinda:~$ file sshkey.privatesshkey.private: PEM RSA private keybandit13@melinda:~$ cat sshkey.private—–BEGIN RSA PRIVATE KEY—–MIIEpAIBAAKCAQEAxkkOE83W2cOT7IWhFc9aPaaQmQDdgzuXCv+ppZHa++buSkN+gg0tcr7Fw8NLGa5+Uzec2rEg0WmeevB13AIoYp0MZyETq46t+jk9puNwZwIt9XgBZufGtZEwWbFWw/vVLNwOXBe4UWStGRWzgPpEeSv5Tb1VjLZIBdGphTIK22Amz6ZbThMsiMnyJafEwJ/T8PQO3myS91vUHEuoOMAzoUID4kN0MEZ3+XahyK0HJVq68KsVObefXG1vvA3GAJ29kxJaqvRfgYnqZryWN7w3CHjNU4c/2Jkp+n8L0SnxaNA+WYA7jiPyTF0is8uzMlYQ4l1Lzh/8/MpvhCQF8r22dwIDAQABAoIBAQC6dWBjhyEOzjeAJ3j/RWmap9M5zfJ/wb2bfidNpwbB8rsJ4sZIDZQ7XuIh4LfygoAQSS+bBw3RXvzEpvJt3SmU8hIDuLsCjL1VnBY5pY7Bju8g8aR/3FyjyNAqx/TLfzlLYfOu7i9Jet67xAh0tONG/u8FB5I3LAI2Vp6OviwvdWeC4nOxCthldpuPKNLA8rmMMVRTKQ+7T2VSnXmwYckKUcUgzoVSpiNZaS0zUDypdpy2+tRH3MQa5kqN1YKjvF8RC47woOYCktsDo3FFpGNFec9Taa3Msy+DfQQhHKZFKIL3bJDONtmrVvtYK40/yeU4aZ/HA2DQzwheol1AfiEhAoGBAOnVjosBkm7sblK+n4IEwPxs8sOmhPnTDUy5WGrpSCrXOmsVIBUflaL3ZGLx3xCIwtCnEucB9DvN2HZkupc/h6hTKUYLqXuyLD8njTrbRhLgbC9QrKrSM1F2fSTxVqPtZDlDMwjNR04xHA/fKh8bXXyTMqOHNJTHHNhbh3McdURjAoGBANkU1hqfnw7+aXncJ9bjysr1ZWbqOE5Nd8AFgfwaKuGTTVX2NsUQnCMWdOp+wFak40JHPKWkJNdBG+ex0H9JNQsTK3X5PBMAS8AfX0GrKeuwKWA6erytVTqjOfLYcdp5+z9s8DtVCxDuVsM+i4X8UqIGOlvGbtKEVokHPFXP1q/dAoGAcHg5YX7WEehCgCYTzpO+xysX8ScM2qS6xuZ3MqUWAxUWkh7NGZvhe0sGy9iOdANzwKw7mUUFViaCMR/t54W1GC83sOs3D7n5Mj8x3NdO8xFit7dT9a245TvaoYQ7KgmqpSg/ScKCw4c3eiLava+J3btnJeSIU+8ZXq9XjPRpKwUCgYA7z6LiOQKxNeXH3qHXcnHok855maUj5fJNpPbYiDkyZ8ySF8GlcFsky8Yw6fWCqfG3zDrohJ5l9JmEsBh7SadkwsZhvecQcS9t4vby9/8X4jS0P8ibfcKS4nBP+dT81kkkg5Z5MohXBORA7VWx+ACohcDEkprsQ+w32xeDqT1EvQKBgQDKm8ws2ByvSUVs9GjTilCajFqLJ0eVYzRPaY6f++Gv/UVfAPV4c+S0kAWpXbv5tbkkzbS0eaLPTKgLzavXtQoTtKwrjpolHKIHUz6Wu+n4abfAIRFubOdN/+aLoRQ0yBDRbdXMsZN/jvY44eM+xRLdRVyMmdPtP8belRi2E2aEzA==—–END RSA PRIVATE KEY—–bandit13@melinda:~$ ssh bandit14@localhost -i sshkey.private -p 2220bandit14@melinda:~$ cat /etc/bandit_pass/bandit144wcYUJFw0k0XLShlDzztnTBHiqxU3b3ebandit14@melinda:~$
Referencehttps://help.ubuntu.com/community/SSH/OpenSSH/Keys
Bandit Level 14 ? Level 15
Level GoalThe password for the next level can be retrieved by submitting the password of the current level to port 30000 on localhost.
bandit14@melinda:~$ nc localhost 300004wcYUJFw0k0XLShlDzztnTBHiqxU3b3eCorrect!BfMYroe26WYalil77FoDi9qh59eK5xNrbandit14@melinda:~$
Referencehttps://www.youtube.com/watch?v=7_LPdttKXPchttp://computer.howstuffworks.com/web-server5.htmhttps://en.wikipedia.org/wiki/IP_addresshttps://en.wikipedia.org/wiki/Localhosthttp://computer.howstuffworks.com/web-server8.htmhttps://en.wikipedia.org/wiki/Port_(computer_networking)
Bandit Level 15 ? Level 16
Level GoalThe password for the next level can be retrieved by submitting the password of the current level to port 30001 on localhost using SSL encryption.Helpful note: Getting ?HEARTBEATING? and ?Read R BLOCK?? Use -ign_eof and read the ?CONNECTED COMMANDS? section in the manpage. Next to ?R? and ?Q?, the ?B? command also works in this version of that command?
bandit14@melinda:~$ openssl s_client -connect localhost:30001 -ign_eofCONNECTED(00000003)depth=0 CN = li190-250.members.linode.comverify error:num=18:self signed certificateverify return:1depth=0 CN = li190-250.members.linode.comverify return:1—Certificate chain 0 s:/CN=li190-250.members.linode.com i:/CN=li190-250.members.linode.com—Server certificate—–BEGIN CERTIFICATE—–MIIC3jCCAcagAwIBAgIJAI5QiWZw4YHbMA0GCSqGSIb3DQEBCwUAMCcxJTAjBgNVBAMTHGxpMTkwLTI1MC5tZW1iZXJzLmxpbm9kZS5jb20wHhcNMTQxMTE0MTAyODA0WhcNMjQxMTExMTAyODA0WjAnMSUwIwYDVQQDExxsaTE5MC0yNTAubWVtYmVycy5saW5vZGUuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAsKmy9o5zWU+1EH7Z3bB5TGQA+16zXDcEJy6tZWZ8CDrRyQXiahendp45BWUc/ZuLDo0+B3WtZXjofmLw/F4fmR+8X1s1fQZX2dFt920qEm7LxqzWd0c7FdHiBwwRrwhkk+3cQpOBTTGdLWEgpdmwwNZDTUdsDLzjDczPnju6T6p6ArTECztPbmTjfY4QIRtC6capL1Z+yPJSQVAuAMEX1wTDWTGdm0VV7oW4F5cGZutf6QAP51jdhSyZuGilIPHbnj0l6Qc7a7+OtEsEGi31aJ8KpRf7LNZ7DXCuoB3Hf75Pd6VjDgoOIagcH0NYqa75gEjBkGzsktLWykT7ag7fKwIDAQABow0wCzAJBgNVHRMEAjAAMA0GCSqGSIb3DQEBCwUAA4IBAQCaZdUNAj8WDEKWdoU3LNXUBJlTJwiWBrh550PbHSQORcCz2K0kiMei1A4ojK2NdMHFGAqAeUEaxtz92p2BoFpZasAtdSa3u63tBckFhfUolIS1TC7Cj51y19ysTeepfGPFpuPCVqVPsruei8Z/iqn3bFIhQQdmumeePZQdPMwZSWHNVYC5XODd7PvNDrDu5MZJjkz4+6LbwwAvyew62meFN2QEsYbK2Brtbhze+IjE27FGWlSw4K3jlwa409MDMTf4JU41ELaYY8G/LSNDJsBVhhkHzvXR9iCbXxNz3IL0dQDNj7h4LKhBy0q7hvqgkDzwlmBO4WKSmCAuky44cXmd—–END CERTIFICATE—–subject=/CN=li190-250.members.linode.comissuer=/CN=li190-250.members.linode.com—No client certificate CA names sent—SSL handshake has read 1714 bytes and written 637 bytes—New, TLSv1/SSLv3, Cipher is DHE-RSA-AES256-SHAServer public key is 2048 bitSecure Renegotiation IS supportedCompression: NONEExpansion: NONESSL-Session: Protocol : SSLv3 Cipher : DHE-RSA-AES256-SHA Session-ID: 3D3C8090F26497A5D8EC930C9D4B09A577BE6E4872070FE6FB59CB073B6F9EDA Session-ID-ctx: Master-Key: E73F17121DE4869A375F9683213BD9C6F742B74819AD2A2AD69A37931DA57499C45CFFDAAEB1AE708EE83C6082EB67A2 Key-Arg : None PSK identity: None PSK identity hint: None SRP username: None Start Time: 1495332494 Timeout : 300 (sec) Verify return code: 18 (self signed certificate)—BfMYroe26WYalil77FoDi9qh59eK5xNrCorrect!cluFn7wTiGryunymYOu4RcffSxQluehdread:errno=0bandit14@melinda:~$
- -ign_eof
Inhibit shutting down the connection when end of file is reached in the input.
Referenceshttps://en.wikipedia.org/wiki/Transport_Layer_Securityhttps://www.feistyduck.com/library/openssl-cookbook/online/ch-testing-with-openssl.html
Bandit Level 16 ? Level 17
Level GoalThe credentials for the next level can be retrieved by submitting the password of the current level to a port on localhost in the range 31000 to 32000. First find out which of these ports have a server listening on them. Then find out which of those speak SSL and which don?t. There is only 1 server that will give the next credentials, the others will simply send back to you whatever you send to it.
bandit14@melinda:~$ nmap -sT -A -p 31000-32000 localhostStarting Nmap 6.40 ( http://nmap.org ) at 2017-05-21 02:18 UTCNmap scan report for localhost (127.0.0.1)Host is up (0.00037s latency).Not shown: 996 closed portsPORT STATE SERVICE VERSION31046/tcp open echo31518/tcp open msdtc Microsoft Distributed Transaction Coordinator (error)31691/tcp open echo31790/tcp open msdtc Microsoft Distributed Transaction Coordinator (error)31960/tcp open echoService Info: OS: Windows; CPE: cpe:/o:microsoft:windowsService detection performed. Please report any incorrect results at http://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 41.29 secondsbandit14@melinda:~$ openssl s_client -connect localhost:31790CONNECTED(00000003)depth=0 CN = li190-250.members.linode.comverify error:num=18:self signed certificateverify return:1depth=0 CN = li190-250.members.linode.comverify return:1—Certificate chain 0 s:/CN=li190-250.members.linode.com i:/CN=li190-250.members.linode.com—Server certificate—–BEGIN CERTIFICATE—–MIIC3jCCAcagAwIBAgIJAI5QiWZw4YHbMA0GCSqGSIb3DQEBCwUAMCcxJTAjBgNVBAMTHGxpMTkwLTI1MC5tZW1iZXJzLmxpbm9kZS5jb20wHhcNMTQxMTE0MTAyODA0WhcNMjQxMTExMTAyODA0WjAnMSUwIwYDVQQDExxsaTE5MC0yNTAubWVtYmVycy5saW5vZGUuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAsKmy9o5zWU+1EH7Z3bB5TGQA+16zXDcEJy6tZWZ8CDrRyQXiahendp45BWUc/ZuLDo0+B3WtZXjofmLw/F4fmR+8X1s1fQZX2dFt920qEm7LxqzWd0c7FdHiBwwRrwhkk+3cQpOBTTGdLWEgpdmwwNZDTUdsDLzjDczPnju6T6p6ArTECztPbmTjfY4QIRtC6capL1Z+yPJSQVAuAMEX1wTDWTGdm0VV7oW4F5cGZutf6QAP51jdhSyZuGilIPHbnj0l6Qc7a7+OtEsEGi31aJ8KpRf7LNZ7DXCuoB3Hf75Pd6VjDgoOIagcH0NYqa75gEjBkGzsktLWykT7ag7fKwIDAQABow0wCzAJBgNVHRMEAjAAMA0GCSqGSIb3DQEBCwUAA4IBAQCaZdUNAj8WDEKWdoU3LNXUBJlTJwiWBrh550PbHSQORcCz2K0kiMei1A4ojK2NdMHFGAqAeUEaxtz92p2BoFpZasAtdSa3u63tBckFhfUolIS1TC7Cj51y19ysTeepfGPFpuPCVqVPsruei8Z/iqn3bFIhQQdmumeePZQdPMwZSWHNVYC5XODd7PvNDrDu5MZJjkz4+6LbwwAvyew62meFN2QEsYbK2Brtbhze+IjE27FGWlSw4K3jlwa409MDMTf4JU41ELaYY8G/LSNDJsBVhhkHzvXR9iCbXxNz3IL0dQDNj7h4LKhBy0q7hvqgkDzwlmBO4WKSmCAuky44cXmd—–END CERTIFICATE—–subject=/CN=li190-250.members.linode.comissuer=/CN=li190-250.members.linode.com—No client certificate CA names sent—SSL handshake has read 1714 bytes and written 637 bytes—New, TLSv1/SSLv3, Cipher is DHE-RSA-AES256-SHAServer public key is 2048 bitSecure Renegotiation IS supportedCompression: NONEExpansion: NONESSL-Session: Protocol : SSLv3 Cipher : DHE-RSA-AES256-SHA Session-ID: 20CA4FD2722C9FC893DECEE1CA87C16F698563B7116265F39D48D3D8F6853EAF Session-ID-ctx: Master-Key: FE0F0C093E12801D5CF052F1734410396EF1D35B1C85BA0DA685ED8A990E62A96221321469CA02D4C7374A628EDEECE8 Key-Arg : None PSK identity: None PSK identity hint: None SRP username: None Start Time: 1495333239 Timeout : 300 (sec) Verify return code: 18 (self signed certificate)—cluFn7wTiGryunymYOu4RcffSxQluehdCorrect!—–BEGIN RSA PRIVATE KEY—–MIIEogIBAAKCAQEAvmOkuifmMg6HL2YPIOjon6iWfbp7c3jx34YkYWqUH57SUdyJimZzeyGC0gtZPGujUSxiJSWI/oTqexh+cAMTSMlOJf7+BrJObArnxd9Y7YT2bRPQJa6Lzb558YW3FZl87ORiO+rW4LCDCNd2lUvLE/GL2GWyuKN0K5iCd5TbtJzEkQTuDSt2mcNn4rhAL+JFr56o4T6z8WWAW18BR6yGrMq7Q/kALHYW3OekePQAzL0VUYbWJGTi65CxbCnzc/w4+mqQyvmzpWtMAzJTzAzQxNbkR2MBGySxDLrjg0LWN6sK7wNXx0YVztz/zbIkPjfkU1jHS+9EbVNj+D1XFOJuaQIDAQABAoIBABagpxpM1aoLWfvDKHcj10nqcoBc4oE11aFYQwik7xfW+24pRNuDE6SFthOar69jp5RlLwD1NhPx3iBlJ9nOM8OJ0VToum43UOS8YxF8WwhXriYGnc1sskbwpXOUDc9uX4+UESzH22P29ovdd8WErY0gPxun8pbJLmxkAtWNhpMvfe0050vk9TL5wqbu9AlbssgTcCXkMQnPw9nCYNN6DDP2lbcBrvgT9YCNL6C+ZKufD52yOQ9qOkwFTEQpjtF4uNtJom+asvlpmS8AvLY9r60wYSvmZhNqBUrj7lyCtXMIu1kkd4w7F77k+DjHoAXyxcUp1DGL51sOmama+TOWWgECgYEA8JtPxP0GRJ+IQkX262jM3dEIkza8ky5moIwUqYdsx0NxHgRRhORT8c8hAuRBb2G82so8vUHk/fur85OEfc9TncnCY2crpoqsghifKLxrLgtT+qDpfZnxSatLdt8GfQ85yA7hnWWJ2MxF3NaeSDm75Lsm+tBbAiyc9P2jGRNtMSkCgYEAypHdHCctNi/FwjulhttFx/rHYKhLidZDFYeiE/v45bN4yFm8x7R/b0iE7KaszX+ExdvtSghaTdcG0Knyw1bpJVyusavPzpaJMjdJ6tcFhVAbAjm7enCIvGCSx+X3l5SiWg0AR57hJglezIiVjv3aGwHwvlZvtszK6zV6oXFAu0ECgYAbjo46T4hyP5tJi93V5HDiTtiek7xRVxUl+iU7rWkGAXFpMLFteQEsRr7PJ/lemmEY5eTDAFMLy9FL2m9oQWCgR8VdwSk8r9FGLS+9aKcV5PI/WEKlwgXinB3OhYimtiG2Cg5JCqIZFHxD6MjEGOiuL8ktHMPvodBwNsSBULpG0QKBgBAplTfC1HOnWiMGOU3KPwYWt0O6CdTkmJOmL8Niblh9elyZ9FsGxsgtRBXRsqXuz7wtsQAgLHxbdLq/ZJQ7YfzOKU4ZxEnabvXnvWkUYOdjHdSOoKvDQNWu6ucyLRAWFuISeXw9a/9p7ftpxm0TSgyvmfLF2MIAEwyzRqaM77pBAoGAMmjmIJdjp+Ez8duyn3ieo36yrttF5NSsJLAbxFpdlc1gvtGCWW+9Cq0bdxviW8+TFVEBl1O4f7HVm6EpTscdDxU+bCXWkfjuRb7Dy9GOtt9JPsX8MBTakzh3vBgsyi/sN3RqRBcGU40fOoZyfAMT8s1m/uYv52O6IgeuZ/ujbjY=—–END RSA PRIVATE KEY—–read:errno=0bandit14@melinda:~$
Referenceshttps://en.wikipedia.org/wiki/Port_scanner
Bandit Level 17 ? Level 18
Level GoalThere are 2 files in the home directory: passwords.old and passwords.new. The password for the next level is in passwords.new and is the only line that has been changed between passwords.old and passwords.newNOTE: if you have solved this level and see ?Byebye!? when trying to log into bandit18, this is related to the next level, bandit19
? ~ touch sshkey.private? ~ nano sshkey.private? ~ cat sshkey.private—–BEGIN RSA PRIVATE KEY—–MIIEogIBAAKCAQEAvmOkuifmMg6HL2YPIOjon6iWfbp7c3jx34YkYWqUH57SUdyJimZzeyGC0gtZPGujUSxiJSWI/oTqexh+cAMTSMlOJf7+BrJObArnxd9Y7YT2bRPQJa6Lzb558YW3FZl87ORiO+rW4LCDCNd2lUvLE/GL2GWyuKN0K5iCd5TbtJzEkQTuDSt2mcNn4rhAL+JFr56o4T6z8WWAW18BR6yGrMq7Q/kALHYW3OekePQAzL0VUYbWJGTi65CxbCnzc/w4+mqQyvmzpWtMAzJTzAzQxNbkR2MBGySxDLrjg0LWN6sK7wNXx0YVztz/zbIkPjfkU1jHS+9EbVNj+D1XFOJuaQIDAQABAoIBABagpxpM1aoLWfvDKHcj10nqcoBc4oE11aFYQwik7xfW+24pRNuDE6SFthOar69jp5RlLwD1NhPx3iBlJ9nOM8OJ0VToum43UOS8YxF8WwhXriYGnc1sskbwpXOUDc9uX4+UESzH22P29ovdd8WErY0gPxun8pbJLmxkAtWNhpMvfe0050vk9TL5wqbu9AlbssgTcCXkMQnPw9nCYNN6DDP2lbcBrvgT9YCNL6C+ZKufD52yOQ9qOkwFTEQpjtF4uNtJom+asvlpmS8AvLY9r60wYSvmZhNqBUrj7lyCtXMIu1kkd4w7F77k+DjHoAXyxcUp1DGL51sOmama+TOWWgECgYEA8JtPxP0GRJ+IQkX262jM3dEIkza8ky5moIwUqYdsx0NxHgRRhORT8c8hAuRBb2G82so8vUHk/fur85OEfc9TncnCY2crpoqsghifKLxrLgtT+qDpfZnxSatLdt8GfQ85yA7hnWWJ2MxF3NaeSDm75Lsm+tBbAiyc9P2jGRNtMSkCgYEAypHdHCctNi/FwjulhttFx/rHYKhLidZDFYeiE/v45bN4yFm8x7R/b0iE7KaszX+ExdvtSghaTdcG0Knyw1bpJVyusavPzpaJMjdJ6tcFhVAbAjm7enCIvGCSx+X3l5SiWg0AR57hJglezIiVjv3aGwHwvlZvtszK6zV6oXFAu0ECgYAbjo46T4hyP5tJi93V5HDiTtiek7xRVxUl+iU7rWkGAXFpMLFteQEsRr7PJ/lemmEY5eTDAFMLy9FL2m9oQWCgR8VdwSk8r9FGLS+9aKcV5PI/WEKlwgXinB3OhYimtiG2Cg5JCqIZFHxD6MjEGOiuL8ktHMPvodBwNsSBULpG0QKBgBAplTfC1HOnWiMGOU3KPwYWt0O6CdTkmJOmL8Niblh9elyZ9FsGxsgtRBXRsqXuz7wtsQAgLHxbdLq/ZJQ7YfzOKU4ZxEnabvXnvWkUYOdjHdSOoKvDQNWu6ucyLRAWFuISeXw9a/9p7ftpxm0TSgyvmfLF2MIAEwyzRqaM77pBAoGAMmjmIJdjp+Ez8duyn3ieo36yrttF5NSsJLAbxFpdlc1gvtGCWW+9Cq0bdxviW8+TFVEBl1O4f7HVm6EpTscdDxU+bCXWkfjuRb7Dy9GOtt9JPsX8MBTakzh3vBgsyi/sN3RqRBcGU40fOoZyfAMT8s1m/uYv52O6IgeuZ/ujbjY=—–END RSA PRIVATE KEY—–? ~ chmod 600 sshkey.private? ~ ssh [email protected] -p 2220 -i sshkey.privatebandit17@melinda:~$ lspasswords.new passwords.oldbandit17@melinda:~$ file *passwords.new: ASCII textpasswords.old: ASCII textbandit17@melinda:~$ diff passwords.new passwords.old42c42< kfBf3eYk5BPBRzwjqutbbfE887SVc5Yd—> BS8bqB1kqkinKJjuxL6k072Qq9NRwQpRbandit17@melinda:~$
Bandit Level 18 ? Level 19
Level GoalThe password for the next level is stored in a file readme in the home directory. Unfortunately, someone has modified .bashrc to log you out when you log in with SSH.
? ~ ssh [email protected] -p 2220Byebye !? ~ ssh [email protected] -p 2220 lsThis is the OverTheWire game server. More information on http://www.overthewire.org/wargamesPlease note that wargame usernames are no longer level<X>, but wargamename<X>e.g. vortex4, semtex2, …Note: at this moment, blacksun is not [email protected]’s password:readme? ~ ssh [email protected] -p 2220 cat readmeThis is the OverTheWire game server. More information on http://www.overthewire.org/wargamesPlease note that wargame usernames are no longer level<X>, but wargamename<X>e.g. vortex4, semtex2, …Note: at this moment, blacksun is not [email protected]’s password:IueksS7Ubh8G3DCwVzrTd8rAVOwq3M5x? ~
Bandit Level 19 ? Level 20
Level GoalTo gain access to the next level, you should use the setuid binary in the home directory. Execute it without arguments to find out how to use it. The password for this level can be found in the usual place (/etc/bandit_pass), after you have used the setuid binary.
? ~ ssh [email protected] -p 2220bandit19@melinda:~$ lsbandit20-dobandit19@melinda:~$ file bandit20-dobandit20-do: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 2.6.24, BuildID[sha1]=08e74b8e092a91103efaab7916d75f08b887ab4d, not strippedbandit19@melinda:~$ ls -la bandit20-do-rwsr-x— 1 bandit20 bandit19 7370 Nov 14 2014 bandit20-dobandit19@melinda:~$ ./bandit20-doRun a command as another user. Example: ./bandit20-do idbandit19@melinda:~$ ./bandit20-do iduid=11019(bandit19) gid=11019(bandit19) euid=11020(bandit20) groups=11020(bandit20),11019(bandit19)bandit19@melinda:~$ ./bandit20-do whoamibandit20bandit19@melinda:~$ ./bandit20-do cat /etc/bandit_pass/bandit20GbKksEFF4yrVs6il55v6gwY5aVje5f0jbandit19@melinda:~$
Referenceshttps://en.wikipedia.org/wiki/Setuid
Bandit Level 20 ? Level 21
Level GoalThere is a setuid binary in the home directory that does the following: it makes a connection to localhost on the port you specify as a command line argument. It then reads a line of text from the connection and compares it to the password in the previous level (bandit20). If the password is correct, it will transmit the password for the next level (bandit21).NOTE: To beat this level, you need to login twice: once to run the setuid command, and once to start a network daemon to which the setuid will connect.NOTE 2: Try connecting to your own network daemon to see if it works as you think
? ~ ssh [email protected] -p 2220bandit20@melinda:~$ ls -la suconnect-rwsr-x— 1 bandit21 bandit20 8006 Nov 14 2014 suconnectbandit20@melinda:~$ ./suconnectUsage: ./suconnect <portnumber>This program will connect to the given port on localhost using TCP. If it receives the correct password from the other side, the next password is transmitted back.bandit20@melinda:~$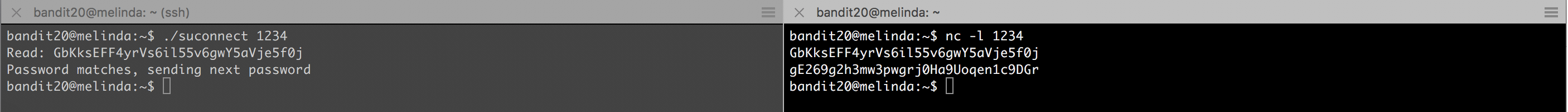 Password : gE269g2h3mw3pwgrj0Ha9Uoqen1c9DGr
Password : gE269g2h3mw3pwgrj0Ha9Uoqen1c9DGr
Bandit Level 21 ? Level 22
Level GoalA program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
? ~ ssh [email protected] -p 2220bandit21@melinda:~$ lsbandit21@melinda:~$ cd /etc/cron.d/bandit21@melinda:/etc/cron.d$ ls -ltotal 92-r–r—– 1 root root 46 Nov 14 2014 behemoth4_cleanup-rw-r–r– 1 root root 355 May 25 2013 cron-apt-rw-r–r– 1 root root 61 Nov 14 2014 cronjob_bandit22-rw-r–r– 1 root root 62 Nov 14 2014 cronjob_bandit23-rw-r–r– 1 root root 61 May 3 2015 cronjob_bandit24-rw-r–r– 1 root root 62 May 3 2015 cronjob_bandit24_root-r–r—– 1 root root 47 Nov 14 2014 leviathan5_cleanup-rw——- 1 root root 233 Nov 14 2014 manpage3_resetpw_job-rw-r–r– 1 root root 51 Nov 14 2014 melinda-stats-rw-r–r– 1 root root 54 Jun 25 2016 natas-session-toucher-rw-r–r– 1 root root 49 Jun 25 2016 natas-stats-r–r—– 1 root root 44 Jun 25 2016 natas25_cleanup-r–r—– 1 root root 47 Aug 3 2015 natas25_cleanup~-r–r—– 1 root root 47 Jun 25 2016 natas26_cleanup-r–r—– 1 root root 43 Jun 25 2016 natas27_cleanup-rw-r–r– 1 root root 510 Oct 29 2014 php5-rw-r–r– 1 root root 63 Jul 8 2015 semtex0-32-rw-r–r– 1 root root 63 Jul 8 2015 semtex0-64-rw-r–r– 1 root root 64 Jul 8 2015 semtex0-ppc-rw-r–r– 1 root root 35 Nov 14 2014 semtex5-rw-r–r– 1 root root 396 Nov 10 2013 sysstat-rw-r–r– 1 root root 29 Nov 14 2014 vortex0-rw-r–r– 1 root root 30 Nov 14 2014 vortex20bandit21@melinda:/etc/cron.d$ cat cronjob_bandit22* * * * * bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/nullbandit21@melinda:/etc/cron.d$ cat /usr/bin/cronjob_bandit22.sh#!/bin/bashchmod 644 /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgvcat /etc/bandit_pass/bandit22 > /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgvbandit21@melinda:/etc/cron.d$ file /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv/tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv: ASCII textbandit21@melinda:/etc/cron.d$ cat /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgvYk7owGAcWjwMVRwrTesJEwB7WVOiILLIbandit21@melinda:/etc/cron.d$
Bandit Level 22 ? Level 23
Level GoalA program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.NOTE: Looking at shell scripts written by other people is a very useful skill. The script for this level is intentionally made easy to read. If you are having problems understanding what it does, try executing it to see the debug information it prints.
? ~ ssh [email protected] -p 2220bandit22@melinda:~$ lsbandit22@melinda:~$ cd /etc/cron.dbandit22@melinda:/etc/cron.d$ ls -ltotal 92-r–r—– 1 root root 46 Nov 14 2014 behemoth4_cleanup-rw-r–r– 1 root root 355 May 25 2013 cron-apt-rw-r–r– 1 root root 61 Nov 14 2014 cronjob_bandit22-rw-r–r– 1 root root 62 Nov 14 2014 cronjob_bandit23-rw-r–r– 1 root root 61 May 3 2015 cronjob_bandit24-rw-r–r– 1 root root 62 May 3 2015 cronjob_bandit24_root-r–r—– 1 root root 47 Nov 14 2014 leviathan5_cleanup-rw——- 1 root root 233 Nov 14 2014 manpage3_resetpw_job-rw-r–r– 1 root root 51 Nov 14 2014 melinda-stats-rw-r–r– 1 root root 54 Jun 25 2016 natas-session-toucher-rw-r–r– 1 root root 49 Jun 25 2016 natas-stats-r–r—– 1 root root 44 Jun 25 2016 natas25_cleanup-r–r—– 1 root root 47 Aug 3 2015 natas25_cleanup~-r–r—– 1 root root 47 Jun 25 2016 natas26_cleanup-r–r—– 1 root root 43 Jun 25 2016 natas27_cleanup-rw-r–r– 1 root root 510 Oct 29 2014 php5-rw-r–r– 1 root root 63 Jul 8 2015 semtex0-32-rw-r–r– 1 root root 63 Jul 8 2015 semtex0-64-rw-r–r– 1 root root 64 Jul 8 2015 semtex0-ppc-rw-r–r– 1 root root 35 Nov 14 2014 semtex5-rw-r–r– 1 root root 396 Nov 10 2013 sysstat-rw-r–r– 1 root root 29 Nov 14 2014 vortex0-rw-r–r– 1 root root 30 Nov 14 2014 vortex20bandit22@melinda:/etc/cron.d$ cat cronjob_bandit23* * * * * bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/nullbandit22@melinda:/etc/cron.d$ cat /usr/bin/cronjob_bandit23.sh#!/bin/bashmyname=$(whoami)mytarget=$(echo I am user $myname | md5sum | cut -d ‘ ‘ -f 1)echo “Copying password file /etc/bandit_pass/$myname to /tmp/$mytarget”cat /etc/bandit_pass/$myname > /tmp/$mytargetbandit22@melinda:/etc/cron.d$ whoamibandit22bandit22@melinda:/etc/cron.d$ echo I am user bandit23 | md5sum | cut -d ‘ ‘ -f 18ca319486bfbbc3663ea0fbe81326349bandit22@melinda:/etc/cron.d$ cat /tmp/8ca319486bfbbc3663ea0fbe81326349jc1udXuA1tiHqjIsL8yaapX5XIAI6i0nbandit22@melinda:/etc/cron.d$
The script is run as bandit23 and not bandit22. I missed that ?
Bandit Level 23 ? Level 24
Level GoalA program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.NOTE: This level requires you to create your own first shell-script. This is a very big step and you should be proud of yourself when you beat this level!NOTE 2: Keep in mind that your shell script is removed once executed, so you may want to keep a copy around?
? ~ ssh [email protected] -p 2220bandit23@melinda:~$ cd /etc/cron.dbandit23@melinda:/etc/cron.d$ ls -ltotal 92-r–r—– 1 root root 46 Nov 14 2014 behemoth4_cleanup-rw-r–r– 1 root root 355 May 25 2013 cron-apt-rw-r–r– 1 root root 61 Nov 14 2014 cronjob_bandit22-rw-r–r– 1 root root 62 Nov 14 2014 cronjob_bandit23-rw-r–r– 1 root root 61 May 3 2015 cronjob_bandit24-rw-r–r– 1 root root 62 May 3 2015 cronjob_bandit24_root-r–r—– 1 root root 47 Nov 14 2014 leviathan5_cleanup-rw——- 1 root root 233 Nov 14 2014 manpage3_resetpw_job-rw-r–r– 1 root root 51 Nov 14 2014 melinda-stats-rw-r–r– 1 root root 54 Jun 25 2016 natas-session-toucher-rw-r–r– 1 root root 49 Jun 25 2016 natas-stats-r–r—– 1 root root 44 Jun 25 2016 natas25_cleanup-r–r—– 1 root root 47 Aug 3 2015 natas25_cleanup~-r–r—– 1 root root 47 Jun 25 2016 natas26_cleanup-r–r—– 1 root root 43 Jun 25 2016 natas27_cleanup-rw-r–r– 1 root root 510 Oct 29 2014 php5-rw-r–r– 1 root root 63 Jul 8 2015 semtex0-32-rw-r–r– 1 root root 63 Jul 8 2015 semtex0-64-rw-r–r– 1 root root 64 Jul 8 2015 semtex0-ppc-rw-r–r– 1 root root 35 Nov 14 2014 semtex5-rw-r–r– 1 root root 396 Nov 10 2013 sysstat-rw-r–r– 1 root root 29 Nov 14 2014 vortex0-rw-r–r– 1 root root 30 Nov 14 2014 vortex20bandit23@melinda:/etc/cron.d$ cat cronjob_bandit24* * * * * bandit24 /usr/bin/cronjob_bandit24.sh &> /dev/nullbandit23@melinda:/etc/cron.d$ cat cronjob_bandit24_root* * * * * root /usr/bin/cronjob_bandit24_root.sh &> /dev/nullbandit23@melinda:/etc/cron.d$ cat /usr/bin/cronjob_bandit24.sh#!/bin/bashmyname=$(whoami)cd /var/spool/$mynameecho “Executing and deleting all scripts in /var/spool/$myname:”for i in * .*;do if [ “$i” != “.” -a “$i” != “..” ]; then echo “Handling $i” timeout -s 9 60 “./$i” rm -f “./$i” fidonebandit23@melinda:/etc/cron.d$
SolutionCreate a directory in the /tmp/ folder. Create a shell script to copy the /etc/bandit_pass/bandit24 to our /tmp/folder. Copy the shell script to /var/spool/bandit24/. Give the shell script and the /tmp/ folder appropriate permissions.
bandit23@melinda:~$ mkdir /tmp/ooobandit23@melinda:~$ nano bandit24.shbandit23@melinda:~$ cat bandit24.sh#!/bin/bashcat /etc/bandit_pass/bandit24 >> /tmp/ooo/level24bandit23@melinda:/tmp/ooo$ chmod 777 bandit24.shbandit23@melinda:/tmp/ooo$ cp bandit24.sh /var/spool/bandit24/bandit23@melinda:/tmp/ooo$ chmod 777 /tmp/ooobandit23@melinda:/tmp/ooo$ ls /var/spool/bandit24/bandit24.sh<—-After a couple of minutes—->bandit23@melinda:/tmp/ooo$ ls /var/spool/bandit24/bandit23@melinda:/tmp/ooo$ lsbandit24.sh level24bandit23@melinda:/tmp/ooo$ cat level24UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZbandit23@melinda:/tmp/ooo$
Bandit Level 24 ? Level 25
Level GoalA daemon is listening on port 30002 and will give you the password for bandit25 if given the password for bandit24 and a secret numeric 4-digit pincode. There is no way to retrieve the pincode except by going through all of the 10000 combinations, called brute-forcing.
? ~ ssh [email protected] -p 2220bandit24@melinda:/tmp/24$ nc localhost 30002I am the pincode checker for user bandit25. Please enter the password for user bandit24 and the secret pincode on a single line, separated by a space.UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 1234Wrong! Please enter the correct pincode. Try again.
Shell script that generated the combination of password and pin
bandit24@melinda:/tmp/24$ cat brute_force.sh#!/bin/bashfor i in {1..10000}do echo “UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ $i” >> ./outdonebandit24@melinda:/tmp/24$ more outUoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 1UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 2UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 3UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 4UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 5<—-snip—->bandit24@melinda:/tmp/24$ cat out | nc localhost 30002I am the pincode checker for user bandit25. Please enter the password for user bandit24 and the secret pincode on a single line, separated by a space.Wrong! Please enter the correct pincode. Try again.Wrong! Please enter the correct pincode. Try again.Wrong! Please enter the correct pincode. Try again.Wrong! Please enter the correct pincode. Try again.Wrong! Please enter the correct pincode. Try again.Wrong! Please enter the correct pincode. Try again.<—-snip—->Wrong! Please enter the correct pincode. Try again.Wrong! Please enter the correct pincode. Try again.Wrong! Please enter the correct pincode. Try again.Correct!The password of user bandit25 is uNG9O58gUE7snukf3bvZ0rxhtnjzSGzGExiting.bandit24@melinda:/tmp/24$
Bandit Level 25 ? Level 26
Level GoalLogging in to bandit26 from bandit25 should be fairly easy? The shell for user bandit26 is not /bin/bash, but something else. Find out what it is, how it works and how to break out of it.
? ~ ssh [email protected] -p 2220bandit25@melinda:~$ lsbandit26.sshkeybandit25@melinda:~$ file bandit26.sshkeybandit26.sshkey: PEM RSA private keybandit25@melinda:~$ ssh bandit26@localhost -p 2220 -i bandit26.sshkey<—-snip—> _ _ _ _ ___ __ | | | (_) | |__ / / | |__ __ _ _ __ __| |_| |_ ) / /_ | ‘_ / _` | ‘_ / _` | | __| / / ‘_ | |_) | (_| | | | | (_| | | |_ / /| (_) | |_.__/ __,_|_| |_|__,_|_|__|_______/Connection to localhost closed.bandit25@melinda:~$
The moment we login in we are kicked out. So lets inspect the shell this user has.
bandit25@melinda:~$ cat /etc/passwd | grep bandit26bandit26:x:11026:11026:bandit level 26:/home/bandit26:/usr/bin/showtextbandit25@melinda:~$
It uses a custom shell called showtext
bandit25@melinda:~$ cat /usr/bin/showtext#!/bin/shmore ~/text.txtexit 0bandit25@melinda:~$
We can safely assume that the shell uses more to read banner and later exit the shell with an exit status 0. So the trick lies in the way we use more to access the next level. Going through the man page of more we discover that there is a built in editor.
v -> Start up an editor at current line. The editor is taken from the environment variable VISUAL if defined, or EDITOR if VISUAL is not defined, or defaults to “vi” if neither VISUAL nor EDITOR is defined.
If VISUAL is defines in the environment variable it will take that editor or it will use vi by default. So we need to use this to escape the shell and spawn /bin/bash.
- Trigger more
- Escape shell
- Read flag
bandit25@melinda:~$ ssh bandit26@localhost -p 2220 -i bandit26.sshkey
Make the terminal small enough to activate more. Press v to enter visual mode
:set shell=/bin/bash:shell
You will drop into a bash shell after this.
bandit26@melinda:~$ lsREADME.txt text.txtbandit26@melinda:~$ cat README.txtCongratulations on solving the last level of this game!At this moment, there are no more levels to play in this game. However, we are constantly workingon new levels and will most likely expand this game with more levels soon.Keep an eye out for an announcement on our usual communication channels!In the meantime, you could play some of our other wargames.If you have an idea for an awesome new level, please let us know!bandit26@melinda:~$
Happy Hacking !!!