 Image source: https://www.varonis.com/blog/kerberos-authentication-explained
Image source: https://www.varonis.com/blog/kerberos-authentication-explained
What is Kerberos?
According to Greek mythology Kerberos (Cerberus) was the gigantic, three-headed dog that guards the gates of the underworld to prevent the dead from leaving.
So when it comes to Computer Science, Kerberos is a network authentication protocol, and is currently the default authentication technology used by Microsoft to authenticate users to services within a local area network.

Kerberos was originally developed for Project Athena at the MIT. Kerberos uses symmetric key cryptography and requires trusted third-party authentication service to verify user identities. So they used the name of Kerberos for their computer network authentication protocol as the three heads of the Kerberos represent a client, a server and a Key Distribution Center (KDC), which acts as the trusted third-party authentication service.
How Kerberos works?
So let?s see how this works. As I mentioned this includes following three entities,
- Client: a user, a service of any software.
- Server: where the kerberos protected resource/service is hosted
- Key Distribution Center (KDC): The trusted third-party authentication service
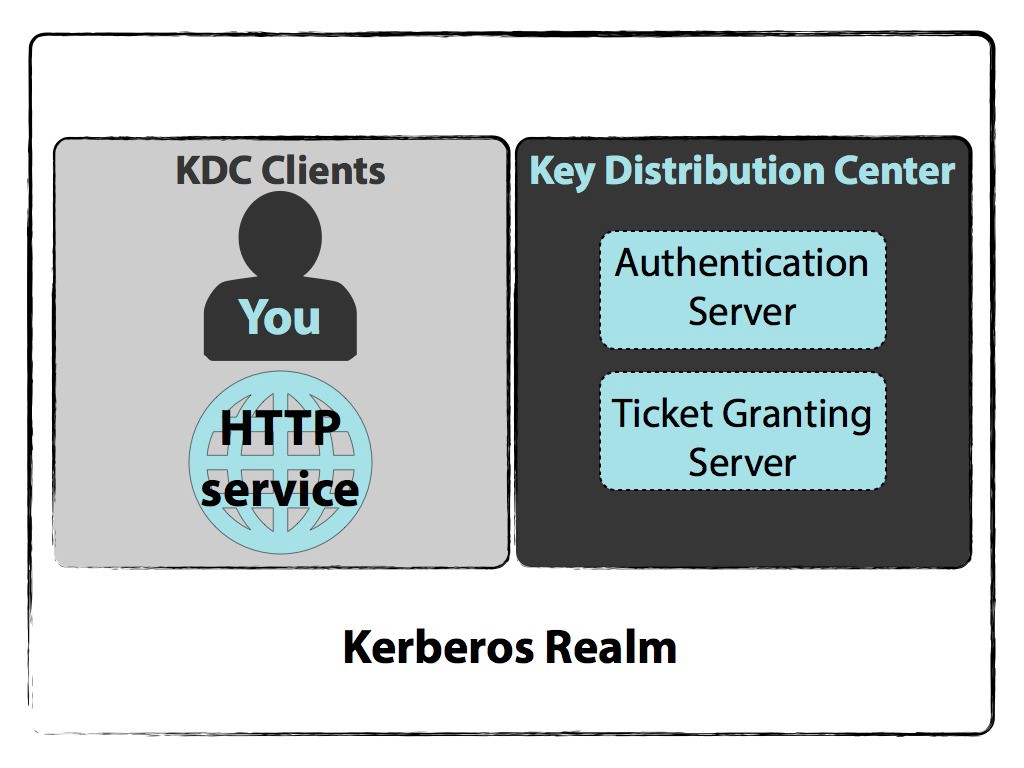 Image source: https://www.roguelynn.com/words/explain-like-im-5-kerberos
Image source: https://www.roguelynn.com/words/explain-like-im-5-kerberos
The KDC includes following two servers:
- Authentication Server (AS) that performs the initial authentication and issues ticket-granting tickets (TGT) for users.
- Ticket-Granting Server (TGS) that issues service tickets that are based on the initial ticket-granting tickets (TGT).
So let?s see how the Kerberos flow works,
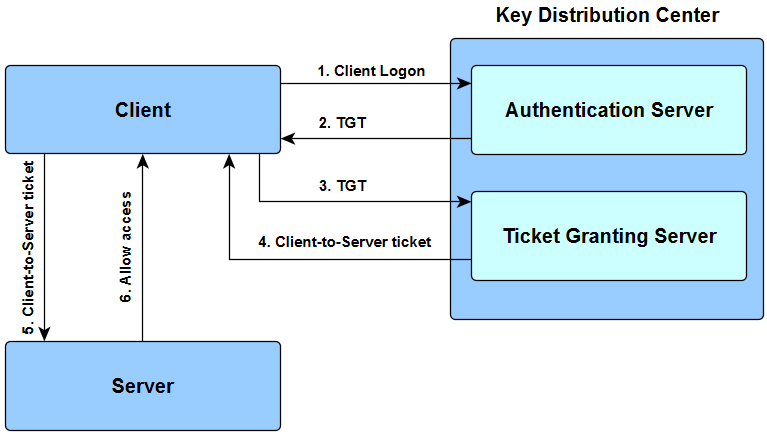 Image source: https://www.datasunrise.com/blog/professional-info/configuring-firewall-to-work-with-kerberos
Image source: https://www.datasunrise.com/blog/professional-info/configuring-firewall-to-work-with-kerberos
- Client sends a request to Authentication Server (AS) with plaintext user ID and asking for a server access on behalf of the user. This request is partially encrypted with a secret key which is the password of the client user.
- Authentication Server (AS) retrive the secret key (user?s password) from the user DB based on the user ID and use his password as a key to decrypt the request. That is how the user is verified. Then the AS sends a Ticket-Granting Ticket (TGT) encrypted with another secret key which is shared between AS and Ticket-Granting Server (TGS).
- Client send the encrypted TGT to the Ticket-Granting Server (TGS) requesting the access for the server.
- Ticket-Granting Server (TGS) decrypt the TGT with shared secret key with AS and issue a kerberos token to the client which is encrypted with another shared secret key with TGS and server.
- Client sends a request to server with the encrypted kerberos token.
- Then the server allow the access to the requested resources to the client for a certain period of time specified in the token.
That?s how the basic kerberos flow works and it?s pretty straightforward. So all the communication steps involve shared secret keys which makes kerberos is a very good example of symmetric key encryption!
Kerberos advanced use cases?
So in the next articles I?m going to talk about following advanced use cases of Kerberos and how you can implement them with WSO2 products,
- Obtain an OAuth 2.0 access token via kerberos (IWA /OAuth 2.0 Kerberos grant)
- Protect the API with kerberos in WSO2 API gateway (Kerberos will be used as the authentication method instead of OAuth 2.0)
- Protect the API backend with kerberos (This need to implemented with kerberos delegation)
References:
- http://web.mit.edu/kerberos/www/
- https://www.roguelynn.com/words/explain-like-im-5-kerberos/
- https://www.datasunrise.com/blog/professional-info/configuring-firewall-to-work-with-kerberos/

