 Protecting all your digital life with a strong lock. (picture by Broesis)
Protecting all your digital life with a strong lock. (picture by Broesis)
This short post exposes the fundamental differences between these three kinds of secret management solutions. After comparing them, I will explain the one I decided to use based on my requirements.
This article is part of my decentralization process so that Google does not own my entire digital life. As such, it can be seen as a continuation of my previous post: Going Paperless with Privacy in Mind.
Secret Management
If you are here I expect you to already be aware of the necessity of password managers. If it is not the case, convince yourself with this quick search on password management.
Edward Snowden telling John Oliver to use passphrases instead of weak passwords.
Using a single strong password will take a load off your mind, freeing up brain power for more productive things than remembering a long list of passwords.
Since you are going to protect all your passwords with a unique memorable secret, it is important to choose it wisely. You can either come up with a personal passphrase yourself or use a technique such as Diceware.
I am using the term secret management instead of password management because once you found a trusted way to secure your passwords behind a master passphrase, there is no reason not to also store non web-based secrets such as your credit card number and PIN or your SSH/cryptocurrency key pairs if you have some. Basically, your password manager solution should let you store securely any plain text secret.
Google Smart Lock
As always with Google this is a well-thought and convenient product. In fact most of Chrome and Android users probably use it, like I did, without necessary having made the choice conscientiously or even without noticing it. It syncs your passwords between all your devices and automatically fills in web forms and signs you in to mobile apps.
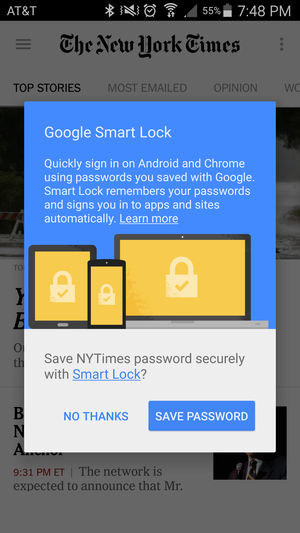 Smart Lock integrates well with Google ecosystem.
Smart Lock integrates well with Google ecosystem.
The drawbacks are:
- Giving all your passwords to Google.
- Storing your most sensitive data in closed-source software.
- Smart Lock has no integrated UI to generate a random password when signing up for a new website. I guess most of its users thus still rely on the bad practice of having the same ? or just slightly different? password on all their apps, compromising all their accounts if only one of their app is hacked. By the way, you can check if all your accounts are safe at: Have I been pwned?
- It cannot be used for long multi-line plain text secrets such as cryptographic key pairs.
- Being yet another Google product, it has a strong vendor-locking effect. It is indeed optimized for Google?s Android and Chrome and becomes less convenient if you are willing to switch to iOS or Firefox. This is what bothers me the most as, like I said, I am trying to decentralize my digital life.
LastPass
LastPass is one of the most popular password manager with Dashlane and 1Password.
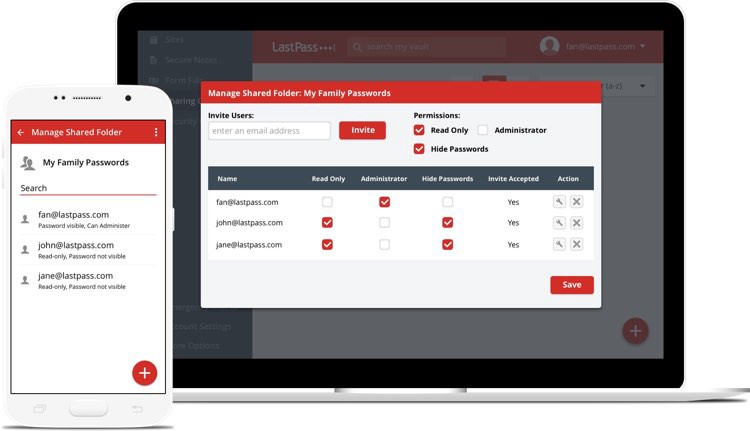 LastPass lets you share securely passwords with your family, friends and coworkers.
LastPass lets you share securely passwords with your family, friends and coworkers.
I decided to try LastPass because of its generous free plan including:
- sync secrets on all your devices
- sharing secrets with another person
- auto-fill forms on web pages
- integrated strong password generator
- secure notes that can be used for any plain text secret
- multi-factor authentication
Besides, with 2$/month, you can share secrets with more than one person and rely on stronger multi-factor authentication such as a YubiKey.
With all these features, LastPass is really a solid contestant! Besides, LastPass and its alternatives should in theory never have access to your secrets. Indeed, they use end-to-end encryption in order to never store your plain secrets on their servers.
Compared to Google Smart Lock, I can only see one remaining drawback: we are still trusting a closed-source software with our sensitive data. Since LastPass has built-in support for handling bank account credentials, social security number, etc. its users are certainly putting all their secrets in their digital vault. It means that someone with access to LastPass codebase could tweak the front-end application or browser extensions to send all the user secrets, decrypted after the master password submission, to some malicious server. This could happen if the people behind LastPass go rogue or, more realistically, if they get hacked without noticing it. In any case, the consequences would be tragic!
Whether you believe these scenarios plausible or not and their outcome acceptable is entirely up to you. I have not made a final decision yet myself!
Note: bitwarden is a promising open-source alternative to LastPass. It currently lacks the ability to handle secure notes, credit cards, etc. but it should be coming soon.
KeeWeb
KeeWeb is a free cross-platform open-source password manager compatible with KeePass vault file format.
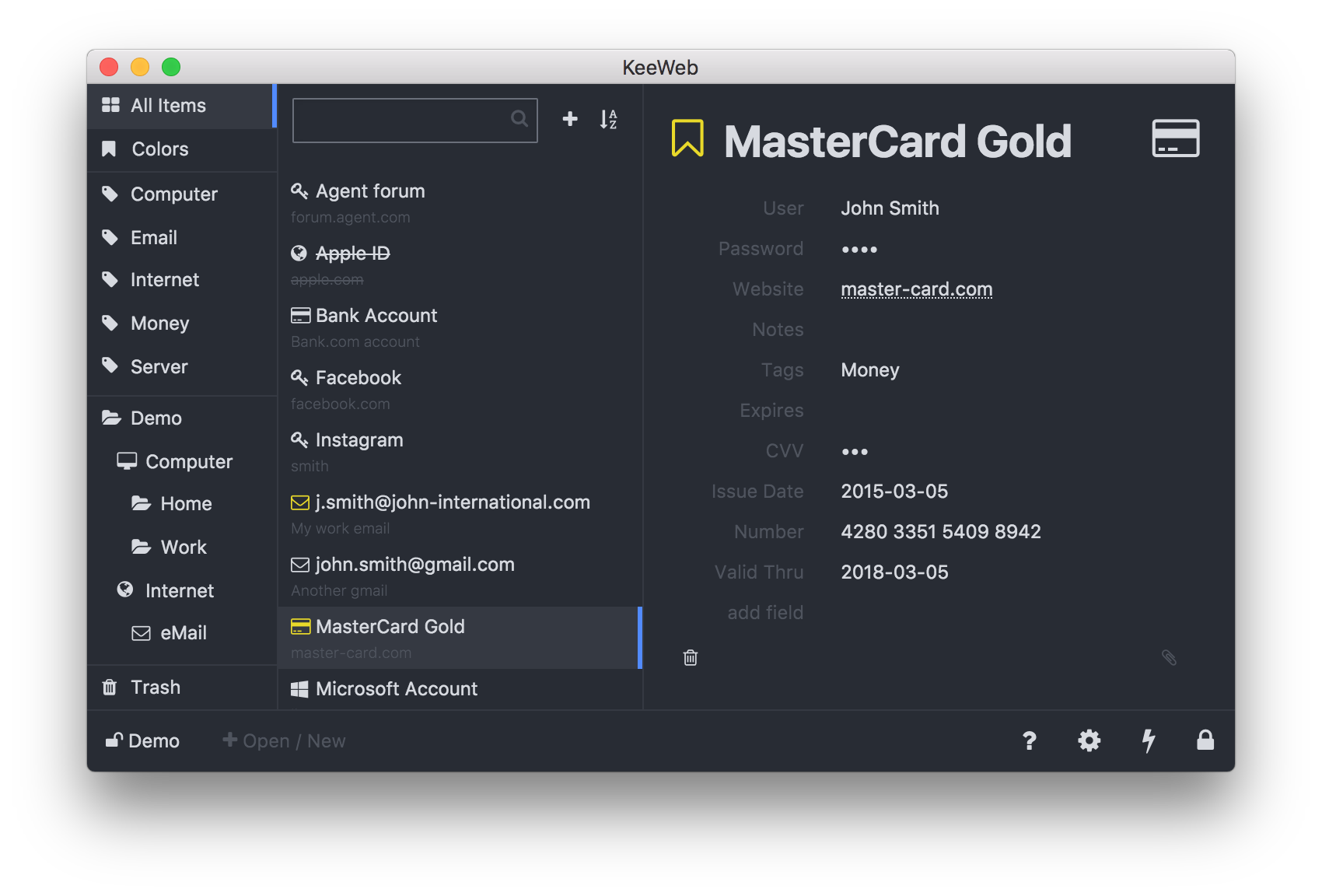 KeeWeb UX is lean and flexible. It handles nicely any kind of secrets.
KeeWeb UX is lean and flexible. It handles nicely any kind of secrets.
It has mostly the same features than LastPass except from integrated secret sharing and form auto-fill. I use the web version ? served from GitHub Pages through CloudFlare CDN ? with Dropbox sync. It means that the encrypted secrets are directly stored on my Dropbox account. Dropbox cannot read them but I benefit from their dependable and cheap storage. Since the encrypted vault is stored on Dropbox, I can also rely on their multi-factor authentication to prevent intruders from getting access to my data.
If you already have LastPass and want to try KeeWeb, you can use my vault converter or the KeePassXC desktop app.
Notes:
- The secret-sharing feature of LastPass can somehow be replicated in KeeWeb by having several vaults. You can indeed imagine having a second vault and sharing its encrypted file with your family members through Dropbox, just like you do with regular files such as pictures or documents.
- The lack of auto-fill feature in KeeWeb is actually good because it can be exploited as an attack vector.
- KeeWeb vaults have a setting called key encryption rounds that defaults to 6,000. I would advise you to increase it to 999,999 or even 9,999,999 as suggested in this article. It will prevent brute force attacks if someone gains access to your vault while slowing down your typical encryption/decryption process of just about one second.
Conclusion
For me, KeeWeb is the most secure solution and the only one I feel comfortable using to handle my bank account credentials. I agree though that it can be a little less convenient than something like LastPass. This is the usual privacy trade-off: you need to choose between security and convenience.
For my most sensitive data, I choose security, I choose KeeWeb.


