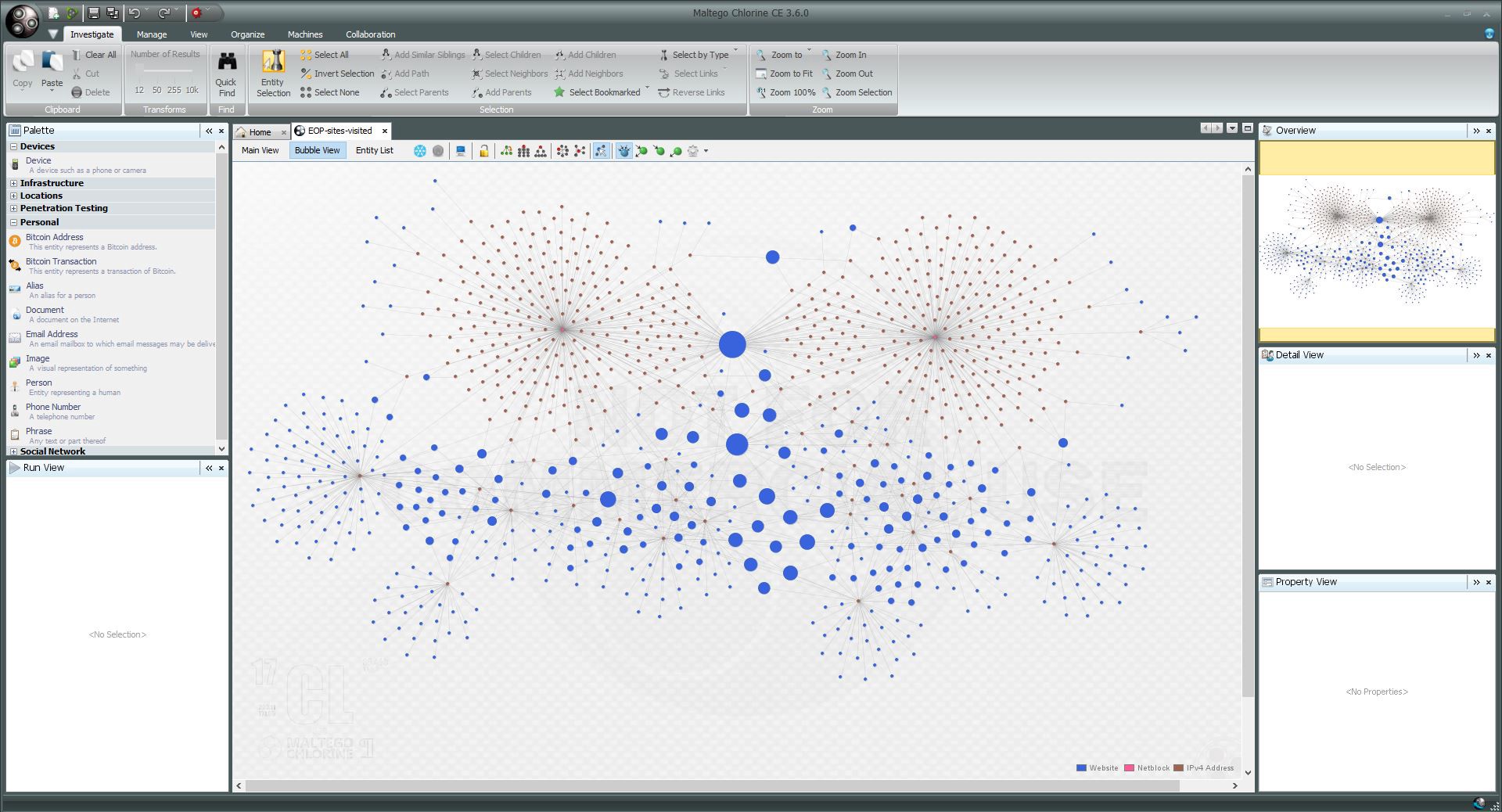
 Attribution graph between a domain and its owners from https://www.paterva.com
Attribution graph between a domain and its owners from https://www.paterva.com
Maltego Disclaimer: The company clarifies that their software may not be used for unlawful actions: ?You are not limited in how you can use the software but you can?t use it for unlawful actions (including collecting email addresses for sending spam). Same goes for the data or graphs you generate using it.? They also add: ?You cannot blame us in any way if something goes wrong with this software. If you use this software and you get into trouble in any way then it?s your problem.?
What is Maltego and why use it for OSINT?
Maltego is a data mining tool that mines a variety of open-source data resources and uses that data to create graphs for analyzing connections. The graphs allow you to easily make connections between information such as name, email organizational structure, domains, documents, etc. Maltego uses Java so it can run on Windows, Mac, and Linux and is available in many OSINT Linux distros like Buscador or Kali. Basically, it will parse a large amount of information and search various open-source websites for you and then toss out a pretty looking graph that will help you put the pieces together. Maltego can be used as a resource at any point during the investigation however if your target is a domain it makes sense to start mapping the network with Maltego from the start.
 This image will make sense in due time (Decider.com)
This image will make sense in due time (Decider.com)
Which Maltego version should I download?
There are several versions of Maltego available:? Maltego XL- Premium version for large data? Maltego Classic- Pay version which includes all APIs (transforms)? Maltego CE- Free Version with limited APIs (transforms)? Casefile- For examining links in offline data
The main difference between Maltego Classic, Maltego XL and Maltego CE are the number of entities that can be returned from a single transform and the maximum number of entities that can be on a single graph.
For our purposes here I will be using Maltego CE which is a free version with limited Transforms. Maltego comes pre-installed in the Buscador Linux distribution which is typically a favorite of Open-Source Intelligence investigators.
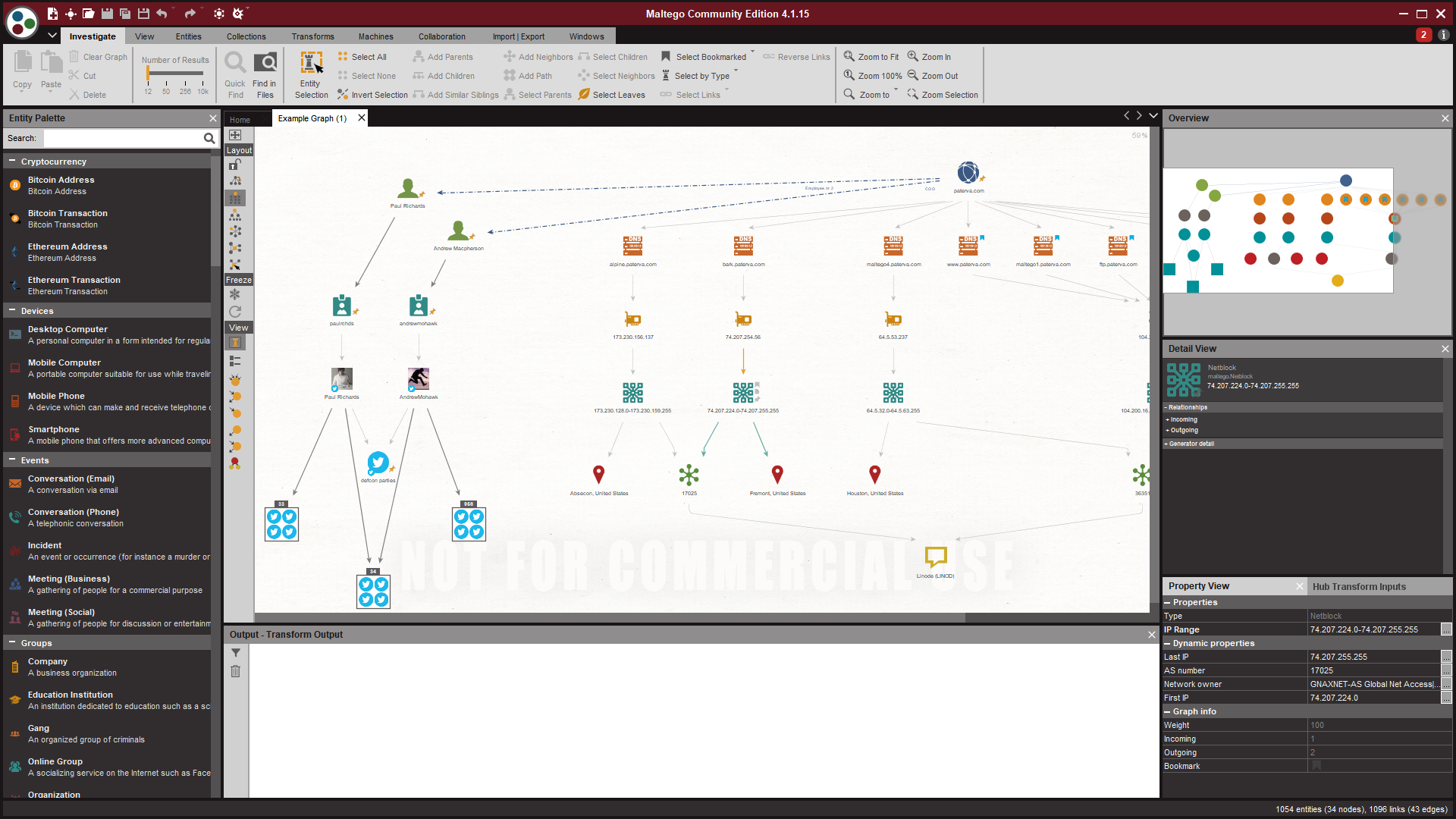 https://docs.maltego.com
https://docs.maltego.com
Installing Maltego
Buscador: If you have Maltego via Buscador it will initially present as the Casefile version. You will need to go to the Maltego site and create an account. Once your account is created you will receive a key which will turn your Casefile into CE.
Kali: Maltego comes pre-installed on Kali. You will need to go to the Maltego site and create an account. Once your account is created you will receive a key that will allow you to use the Community Edition.
Fresh Install: If you are doing a fresh install on Win, Mac, or Linux here is a step-by-step guide provided by Paterva.
What is all this API/Transform nonsense?
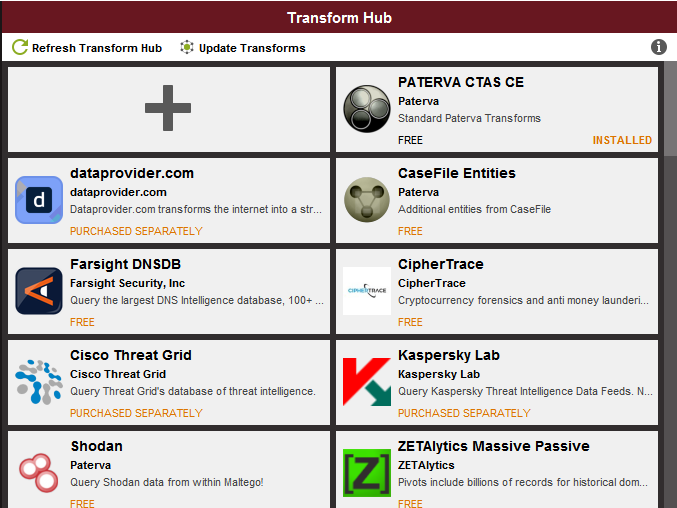 Screenshot of Transforms in the Windows version
Screenshot of Transforms in the Windows version
An API is an Application Programming Interface and in very simple terms it is what connects other software like Shodan and Threatminer with Maltego. Maltego calls these connections ?Transforms? and if you are running Maltego CE you will find that some transforms are free while others are pay. The downside of running the free version of Maltego is that not all of the transforms come pre-installed, therefore, to use them you will need to sign up on each website to get the API code to activate the corresponding transform. Depending on your needs, you can focus on specific transforms made for OSINT, Threat Intel, Organization mapping, etc. which will limit the amount of legwork you need to do for activation.
How to perform simple network recon
Starting with a domain name we can begin to map out the structure of an organization including other sites they own. It is surprising how much information can be found by using nothing more than a domain name.
Click the new graph button in the upper left corner and a blank new graph pane will open.
 new graph
new graph
From the Entity Palette on the left, scroll until you find Domain and then drag it into your blank graph pane.
 Find Domain in the Entity Palette
Find Domain in the Entity Palette
Double click on the domain icon and change the name to the domain you want to investigate, I chose hbo.com.

Right-click on the domain icon, this opens the Run Transforms box. Here you could be very specific about what you want to search for by scrolling through the palette and selecting but we are going to go crazy and just choose Run All Transforms by selecting the little fast forward arrows beside it.
 Run All Transforms on the domain
Run All Transforms on the domain
As soon as Run Transform is selected, Maltego begins its work by graphing out the structure of the network. Note: on the left side of the graph pane there are several options for viewing the graph in different layouts.
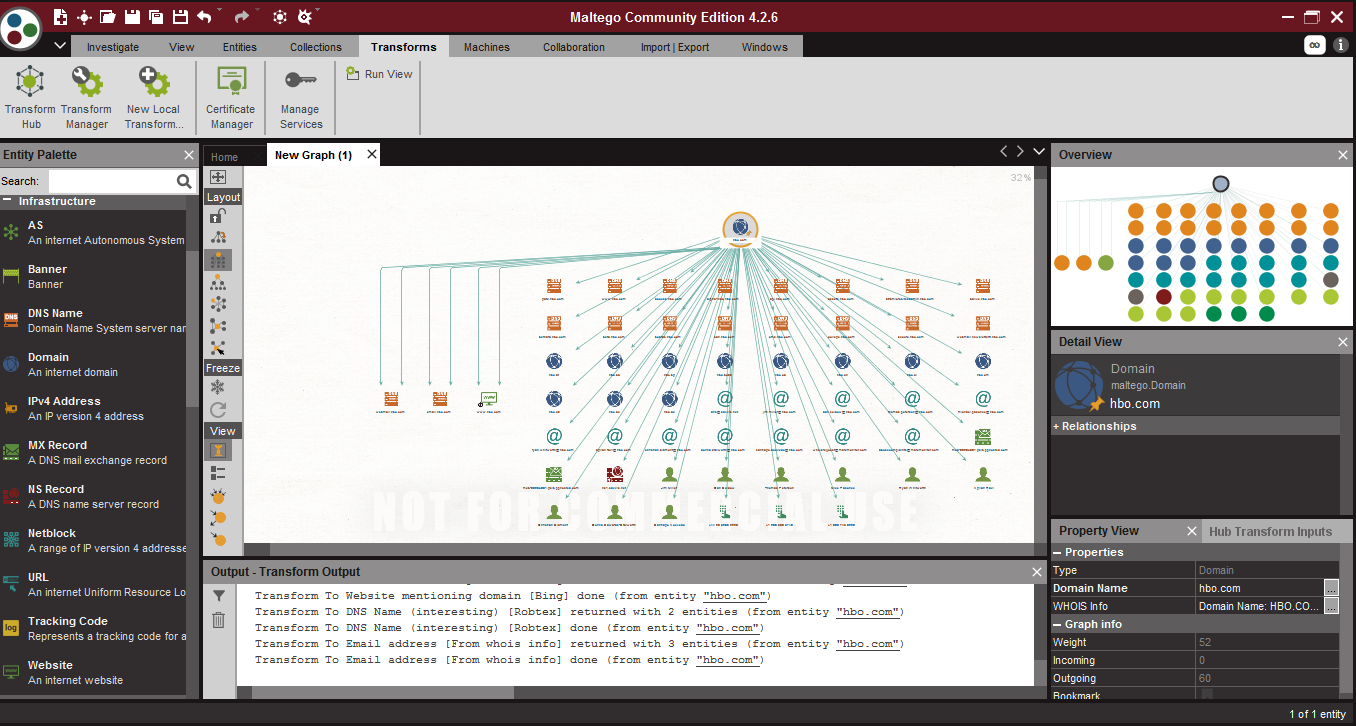 Screenshot of hbo.com domain
Screenshot of hbo.com domain
You can see in the image below that all sorts of information pops up including DNS servers, related sites, related emails, email servers?
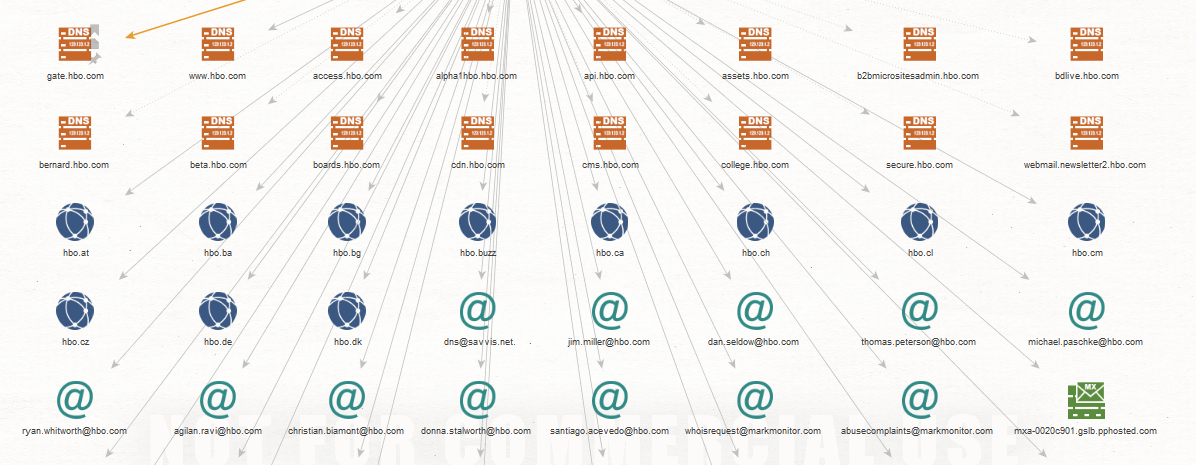 Image showing network
Image showing network
You can use these connections to make even more detailed connections like names associated with emails and phone numbers.
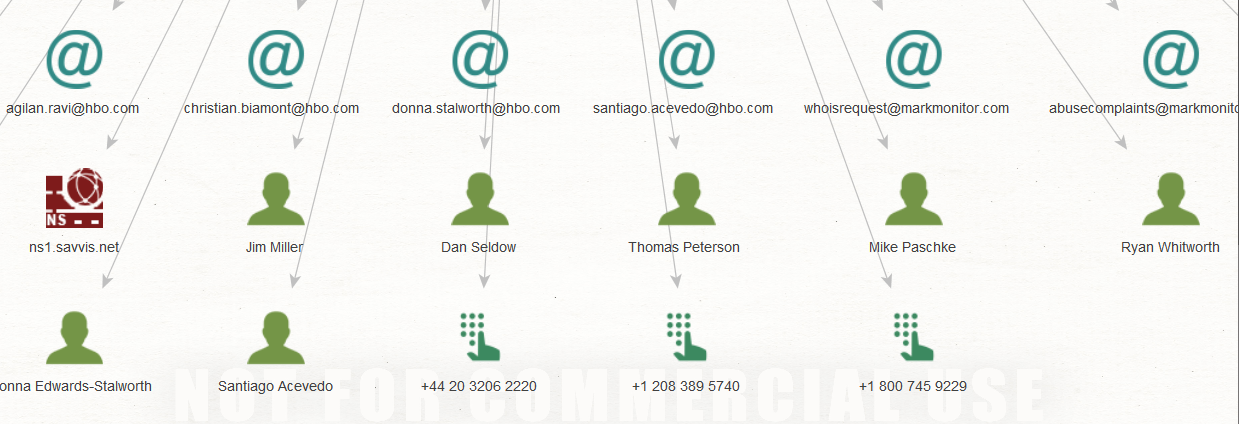
Let?s take a closer look at one of the people that showed up connected to hbo.com ?Thomas Peterson.? Right-click on Thomas?s icon and run All Transforms.
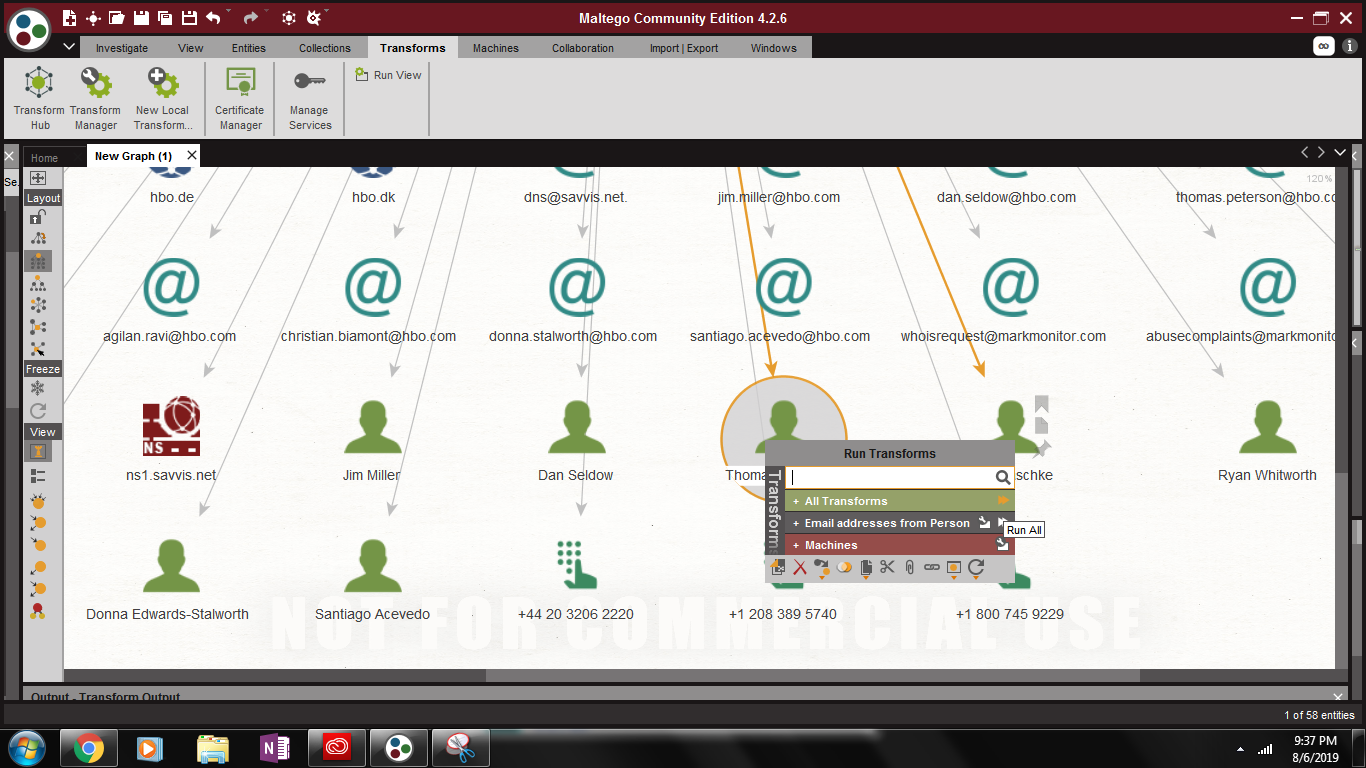
When the transforms finish running, we will have an added graph of all of Thomas Peterson?s associated emails.
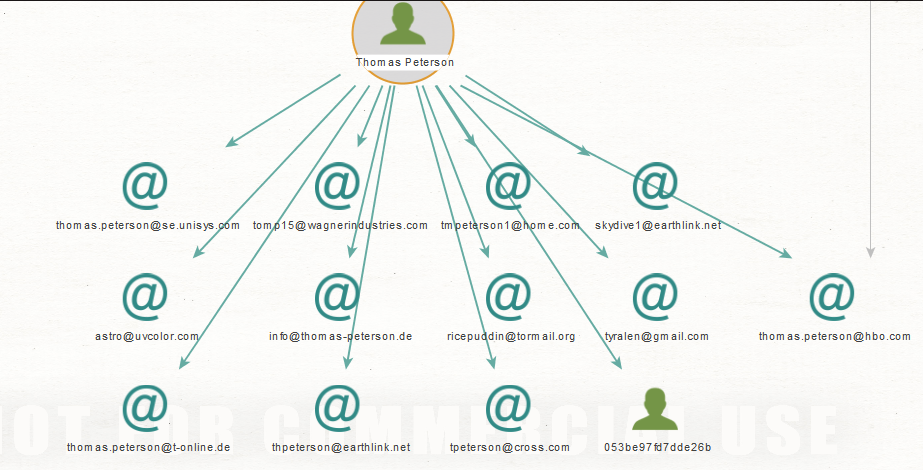 Thomas Peterson?s emails
Thomas Peterson?s emails
Sometimes this can lead to some strange findings. I have stumbled upon a lot of funny/hidden emails while doing similar searches.
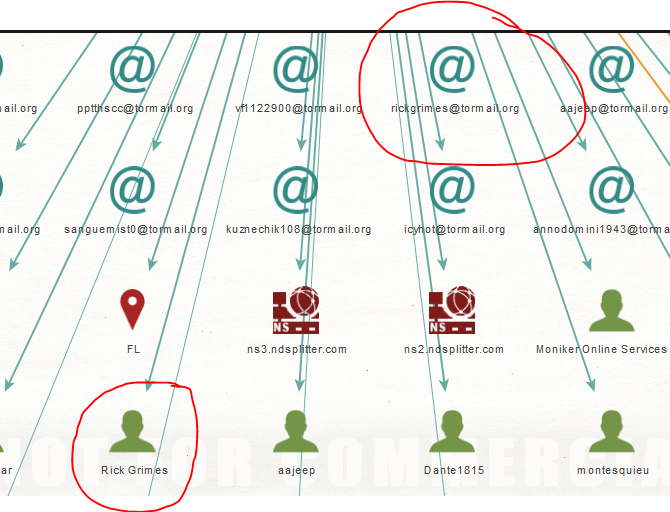 Image of Thomas Peterson?s email associations
Image of Thomas Peterson?s email associations
How to run an email address in Maltego
I was curious about Thomas?s Rick Grimes Tormail address so I decided to take a closer look.
Create a new graph the same way we did in the previous step. This time, select Email Address in the Entity Palette and drag it over to the empty graph.
Double-click on the email address icon and change the text to the email address you want to search. In this case, I used [email protected]?

Right-click on the email address icon and run All Transforms by selecting the fast forward arrows.
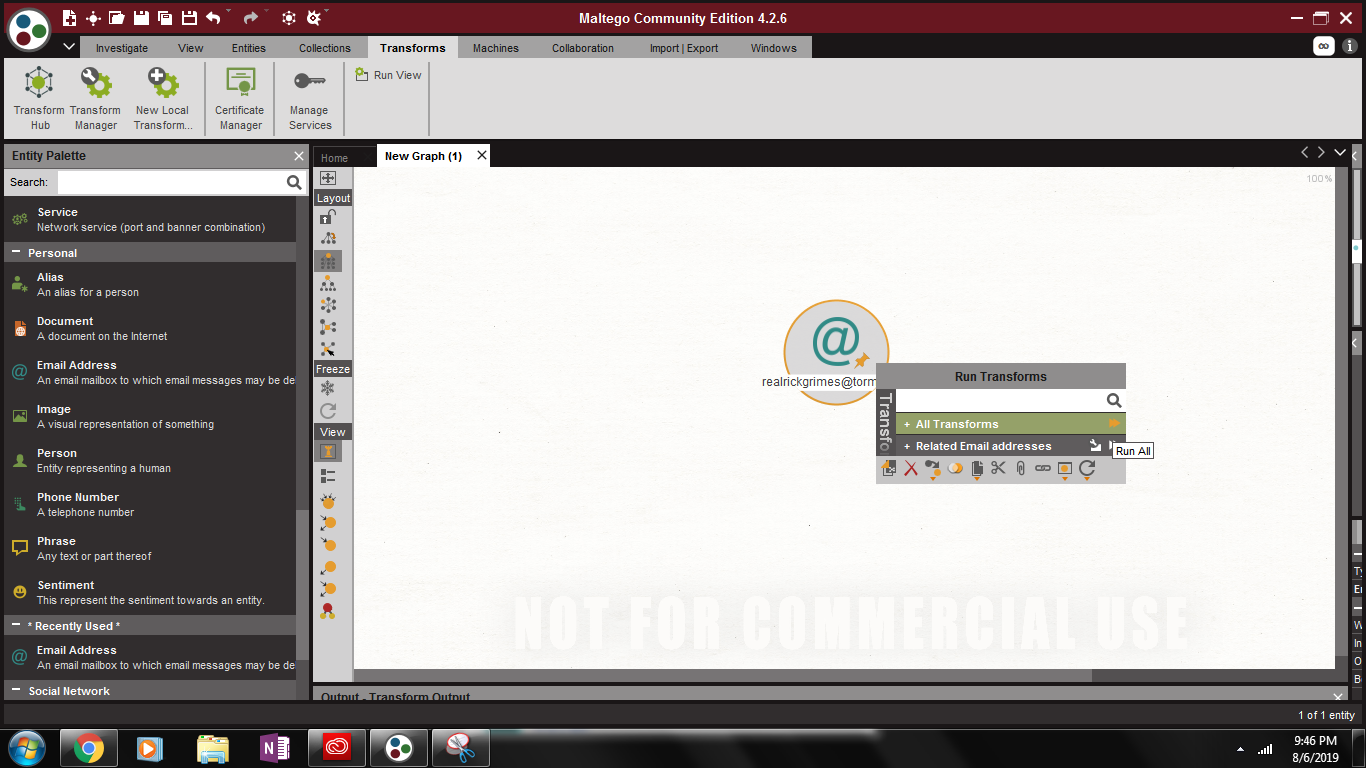 Screenshot of running transforms on an email address
Screenshot of running transforms on an email address
After the transforms run, a graph will pop up displaying all the connections to the address. You can see here that [email protected] connects to a person ?Rick Grimes? who then connects to several other emails. I was intrigued by Rick?s connection with [email protected] so I decided to run another all transforms on that email.
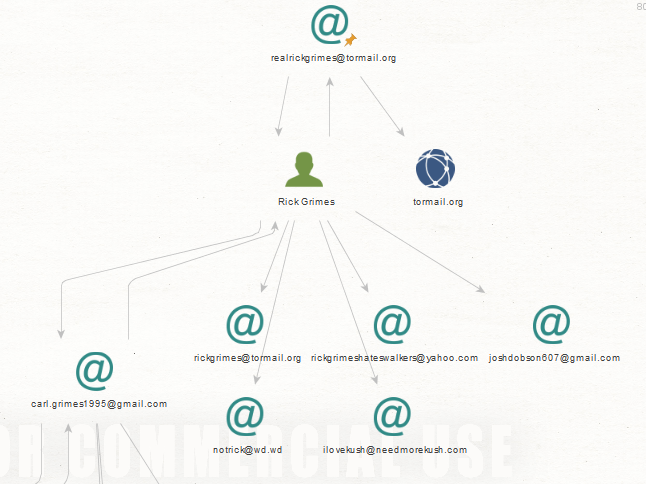 Running all transforms on the email address
Running all transforms on the email address
[email protected] led me to several more interesting people like Carl Grimes and Steve Brule. I feel a bit like I am getting sucked into a black hole of Walking Dead references so I run a Transform on Steve Brule.
 me.me
me.me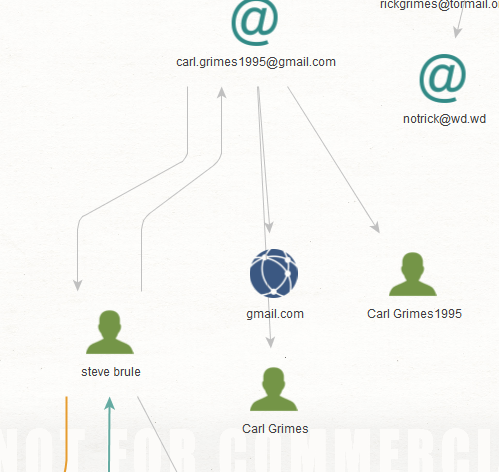
Steve Brule leads me to [email protected] and [email protected] as well as the site checkitout.com.
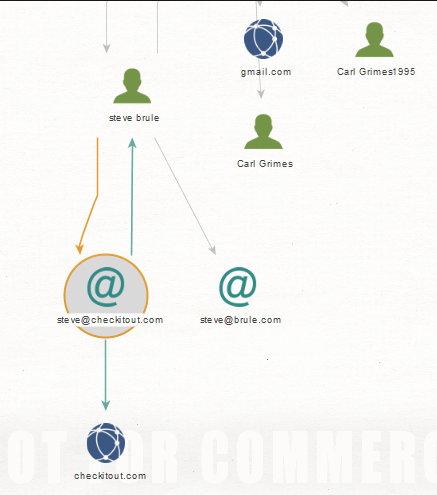
I tried visiting the site but it wasn?t active so I did a quick WhoIs search. The WhoIs search came back registered to CSC Global which runs a digital brand services and domain management company.
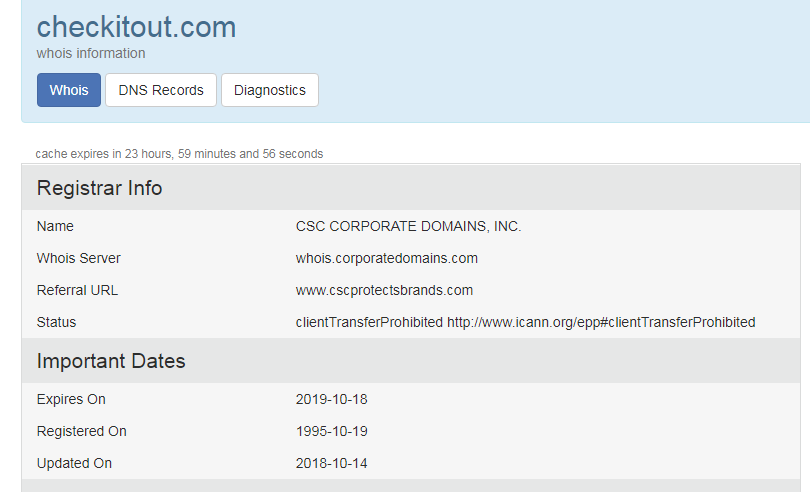
The previous registrant was the Hearst Corporation
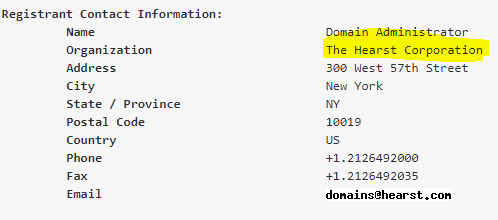
At this point, instead of continuing down the Steve Brule rabbit hole, I am going to assume the Hearst organization and now CSC is holding the domain either to protect it from misuse or to resell it at some point.
As you can see, there are a million fun things you can do with just a simple domain and email search within Maltego! Test drive Maltego yourself by searching your own email address or web address and see what connections you can make. Take it one step further and try searching for your phone number to see how it can be linked to you.
Check out my tutorial for Lampyre if you are looking for another Windows-based solution for email address recon and graphing.