Mimblewimble is a ridiculously-named technology that stops blockchains from blabbing personal information. It?s named after a Harry Potter spell that stops people from spilling secrets.
 Harry Potter ? Warners Bros ? Mimblewimble
Harry Potter ? Warners Bros ? Mimblewimble
Satoshi Nakamoto?s Bitcoin paper has a section titled ?Privacy,? in which Nakamoto is very realistic about Bitcoin?s privacy limitations. These limitations have gotten worse as adversaries have gotten better at using the data Bitcoin spills to dox/deanonymise Bitcoin users. This surprised some people who thought Bitcoin was private because it doesn?t disclose names. Let?s look at what data it does disclose, and why ?
Bitcoin blabs three secrets to fulfill two requirements

Bitcoin blabs three secrets about every transaction:
- Sender?s address
- Amount of coins sent
- Receiver?s address
Bitcoin doesn?t reveal these because it hates privacy. It reveals them because any money system ? gold, cash, barter? has to fulfill two requirements:
- It has to verify that the amount received is equal to the amount sent. A cryptocurrency would be hopelessly broken if I could make a transaction sending 1 coin from one address, and receiving 2 at another address. If I put 5 euros in your hand, 5 euros leave my hand, and 5 enter your hand. I lose five, you gain five, no money is created from thin air during the transaction, and none vanishes.
- I cannot initiate a wire transfer from your bank account, but rather only from my own. We have to verify that the transaction is sent by the holder of the debit card and PIN, or the online banking password, or the private key in the case of cryptocurrencies.
Bitcoin fulfills the two requirements by spilling the three secrets above.
Bitcoin transactions contain the amount and the receiver?s address in plaintext. That is enough to meet the first requirement; we see that 5 bitcoins went into the transaction, and 5 came out.
To verify that the second requirement is fulfilled, Bitcoin uses public addresses with corresponding private keys. The public address owns the bitcoins. The sender generates a signature using the corresponding private key, and signs his transaction (which, I repeat, contains the amount and the receiver?s address in plaintext). Everyone can check that the signature comes from the private key behind the address that holds the coins; this way we know the signature comes from the guy with authority to initiate the transaction.
The claim I am going to make of Mimblewimble is that it fulfills the two requirements while spilling zero of the three secrets.
I am going to demonstrate this with some simple maths, comprehensible to an educated 10-year-old, and also some more advanced maths, comprehensible to an educated 12-year-old.
Multiplying is easy, but factorising is hard

A lot of people are scared of maths and skip over it when they see it in an essay. Well, are you scared of this maths?
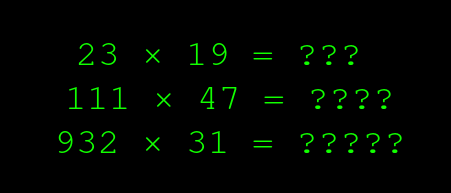
If I gave you a pen and paper and two minutes, you could solve any of these, right? It?s pretty easy for people to multiply numbers. As for computers, even a tiny pocket-computer can multiply millions by millions just as quickly as you can press the buttons.
But let?s make one little change. Let?s just move the question marks to the other side:
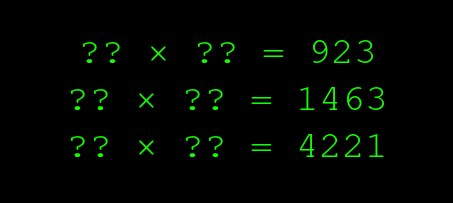
Now if I gave you a pen and paper and two minutes, could you solve these? Probably not. All we did was switch the direction of the operation, and it became much harder.
(By the way, throughout this piece, I?m going to talk about multiplying numbers like 8 and 23, because I like those numbers, and they?re familiar and easy to understand. Computers don?t use numbers like that; they use wonderfully big numbers, in the squillions. A computer could, in fact, figure out what two numbers I multiplied together to make 4221, but it?s hard even for a powerful modern computer to find what you multiplied together to get an answer in the squillions.)
For simplicity, I?m not getting into a discussion of elliptic curves. In practice, encryption systems don?t use just any numbers, but a particular category called elliptic curve points. But the same simple mathematical property is at work: that multiplying is easy, that factorising is the opposite of multiplying, and factorising is hard.
Exploiting the properties of multiplication to hide information and verify ownership
So if I ask you the missing numbers here?.
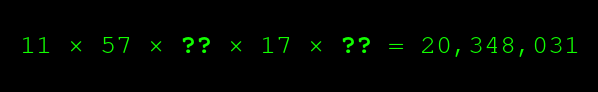
?you can?t easily tell me, because the question marks are on the left. It?s hard to figure out missing factors.
Ok, I?ll tell you. It?s 23 and 83. Now you want to check I am telling the truth. Is it really 23 and 83? To verify my claim, you have a multiplication problem on your hands, and multiplication is easy.
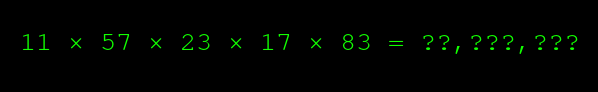
You can quickly solve that, and see that, yes, those are indeed the factors that make it equal 20,348,031:
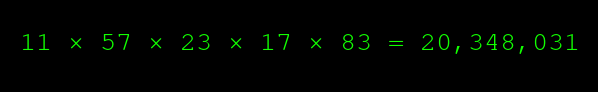
If I had lied, you would easily find out, because my factors wouldn?t give you the big number on the right. I can?t lie about the missing factors, and I can?t guess them or calculate them. I have to know them in advance.
(Note, by the way, that the big number on the right is divisible by all the numbers on the left that were used to construct it; it?s divisible by 83, and by 11, and all the others. We?ll exploit that property later.)
This is just multiplication. Educated 10-year-olds know this. But we accomplished two very important things for cryptocurrency?
We wanted to hide information. Well, now we know how to do that: we can hide information by multiplying by unknowns. That makes it difficult to unscramble.
And we also wanted to prove we hold private keys. Well, now we know how to do that too: by disclosing the factors of big numbers. We did all that just by exploiting the basic properties of multiplication.
Hiding transaction amounts
Let?s use our trick of hiding information by multiplying it by big, secret numbers. One of the three pieces of information Bitcoin blabbed is the amount of coins sent. When I send five bitcoins through the Bitcoin blockchain, that number is represented in plaintext, as ?5?. So let?s conceal that by multiplying it by some other numbers. You can?t easily tell me the amount here:

The equation above is a bit like how amounts are represented in Mimblewimble, but not exactly. In Mimblewimble, the sender and the receiver each come up with a number like this:
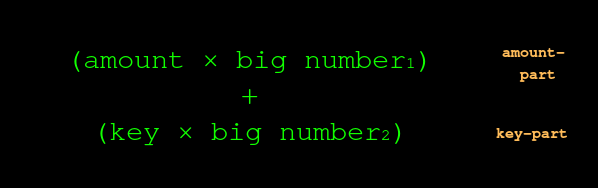
This is called a Pedersen commitment; I don?t know why. The important thing to realise is that it contains an amount-part (but hides the amount by multiplying it by a big number) and a private-key-part.
Note that the sender and the receiver both participate in creating the transaction. This is pretty different from Bitcoin. This gets around the need to blab the recipient?s address, but makes it necessary for some other way for the sender to reach the recipient. Beam includes a secure BBS system (separate from the Beam blockchain) to allow sender and the recipient to exchange their Pedersen commitments.
(For simplicity, I?m leaving out fees. In practice, when I send money to a friend or a vendor, I always also send a little bit to the miners as fees. The principle is the same. I?m also leaving out something called rangeproofs, that prove that the hidden amount is not a negative number, because sending -5 would be like zapping five free coins into my wallet. Maybe there?s a different Harry Potter spell for that.)
You can multiply two numbers by a third either separately or together
This next bit is the most advanced maths we?re going to do. Here in Ireland, you don?t learn it in school until you?re 12, when you?re practically a big boy ?
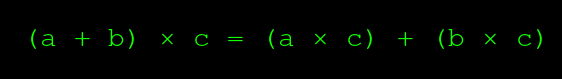
If I want to multiply 2 and 4 by 3, I can smoosh the 2 and 4 together, making 6, and then multiply that 6 by 3, making 18, or else I can first multiply 2 by 3 (giving me 6), then multiply 4 by 3 (giving me 12 more, for a total of 18).
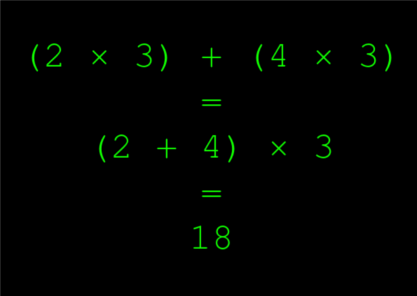
The point I want to drive into your mind is: when we to multiply two numbers by a third, we can either add them together and multiply them by the third, or we can first multiply one by the third, then the other. The two processes are equivalent.
Proving that money in equals money out
Remember that one of the requirements of a money-system is that amount received minus the amount sent must equal zero. I put five euros in your hand, you get five euros. Five minus five equals zero. We can prove that using the tricks above.
A Mimblewimble transaction consists of two Pedersen commitments: one for the money that goes in to the transaction, and one for the money that comes out:
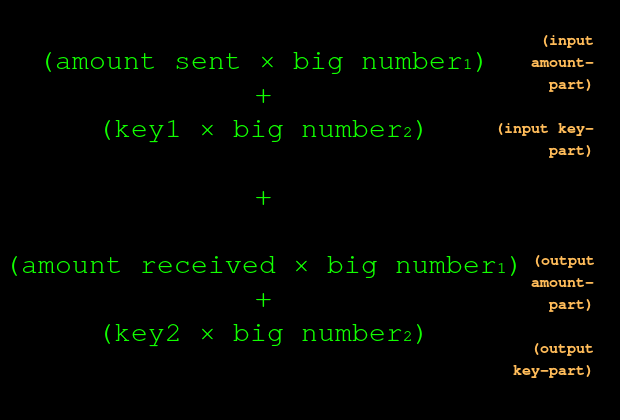
For example, if the sender loses 5, and the recipient gains 5:
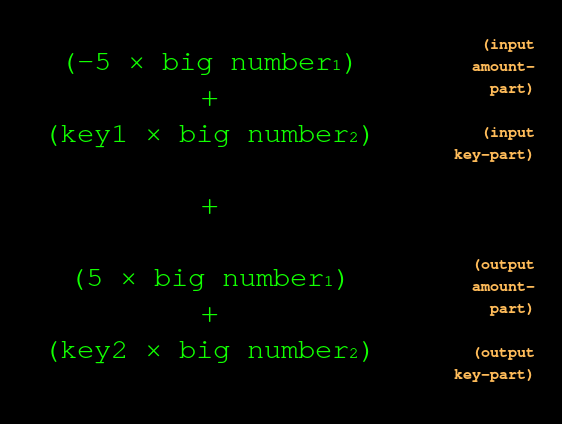
But instead of multiplying the input-amount by the big number, and then multiplying the output-amount by the big number separately, we?re entitled to smoosh ?em together like this:
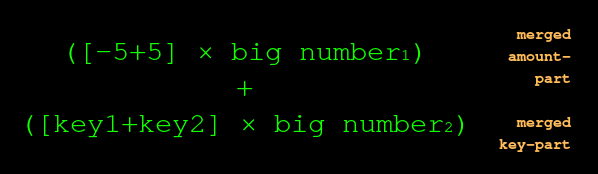
5 minus 5 is zero. Multiply it by a big number and it?s still zero. We?re left with:
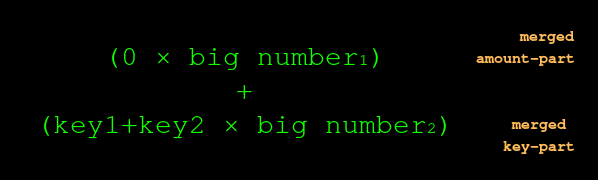
Or just:
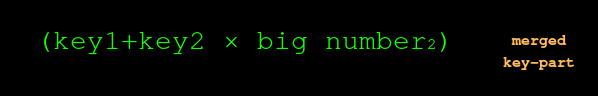
The amount-part vanished! Yet at every step, the amounts were always blinded by multiplying them by big unknowns. We verified they came to zero, without disclosing what they were.
The reason the amount-part vanished is because money-in and money-out were equal. If they were not equal, then they would not have come to zero, and so we?d be left with something more than just the key-part?
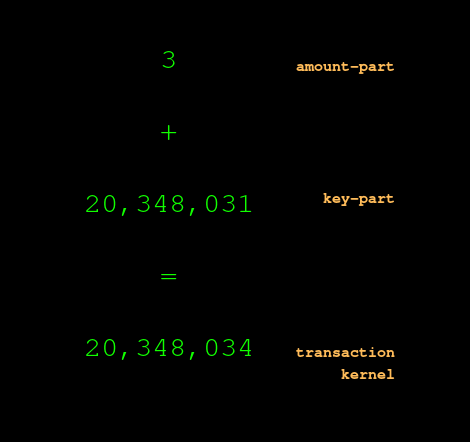
?and therefore the transaction kernel would not be divisible by the private keys 23 and 83. The Beam protocol would reject this transaction as malformed.
(You may notice in this example, if the amount-number was not zero, but was something itself divisible by 23 and 83, say 1909, then the kernel would still be divisible by 23 and 83. This coincidence is possible because of the small numbers I am using to illustrate the point; with the splendidly huge, multi-squillion numbers that computers use, the chances of this coincidence are as close to zero as makes no difference.)
What?s left is just the key-part.

This is a delightfully big number constructed by multiplying together private keys from the sender and the receiver, and another big number. The private keys will divide neatly into it, just like 83 and 23 were secret numbers that divided neatly into the big number here:
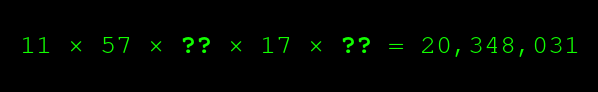
So there are two reasons that the transaction kernel is divisible by the private keys:
- Because the amount-part came to zero
- Because the key-part was formed by multiplying a bunch of numbers, including our private keys of 83 and 23.
These are the two requirements we had for any money-system!
- If the amount-part came to zero, that means that amounts-in minus amounts-out equal zero. In other words, that amounts-in and amounts-out are equal. In short, no money vanished and none was created. We have accomplished that, first by hiding them through multiplying them by a big unknown, and then smooshing them both together, letting them cancel to zero while under the cloak of the big blinding number.
- The second requirement was to prove that the transaction was generated by the holder of the private key. The sender proves that by showing that his private key divides into the transaction kernel, which means it was a factor that constructed the kernel.

Mimblewimble arguably achieves Bitcoin?s goals better than Bitcoin itself (certainly if privacy is a goal). Unlike some privacy coins, which add obfuscation on top of Bitcoin, Mimblewimble achieves it by cutting. We found it exciting enough that we started building a full implementation earlier this year, and expect BEAM will launch before the end of 2018, making Mimblewimble a reality.
Learn more about BEAM?s project on its website
Join BEAM?s developer community: Gitter ? https://gitter.im/beamprivacy/Lobby?
Telegram: t.me/BeamPrivacy
Reddit: reddit.com/r/beamprivacy/
Twitter: twitter.com/beamprivacy
Discord: discord.gg/BHZvAhg