A brief introduction to the notorious DDoS-for-hire services
 Photo by Markus Spiske ? https://unsplash.com/photos/FXFz-sW0uwo
Photo by Markus Spiske ? https://unsplash.com/photos/FXFz-sW0uwo
Introduction
Distributed denial of service (DDoS) attacks are not something new to the internet. However, the medium in which people can accomplish these attacks has progressively gotten more accessible as the internet has evolved. In this article, I want to shed some light on how easy it was to orchestrate your own attacks during a specific time frame, 2012?16.
I hope it goes without saying, but please do not try to go off on your own and attempt to do your own investigating on the internet for these services. It is against the law, and you put yourself at risk when browsing unknown websites.
Before going into the grit of the article, let?s get a few things clarified.
What Does Someone Need for a DDoS Attack?
There are several ways to go about conducting a DDoS attack, but they all end up boiling down to the same thing: you will need an IP address and infrastructure.
We can think of an IP address as a way the internet publicly identifies a network. When you are connected to your home Wi-Fi and browsing a website, that website is able to see the pages you are attempting to view, solely by scoping your IP address. An IP address is like your internet fingerprint.
The attacker also needs infrastructure to orchestrate these attacks. How attackers gain infrastructure makes for its own article. Let?s just assume that these attackers have their own dedicated computers with dedicated networks that are able to send traffic to any other IP address.
How Denial of Service Happens
Let?s think about your home internet connection as a coffee shop. Your coffee shop operates 24/7 and always has some people inside. As with any building, there is a limit to how many people can fit inside. This is where internet speed comes into play. Let?s assume a typical residential internet connection clocks in at 100 Mbits per second ? and for our example, let?s say 100 Mbit = 100 people.
So we are allowed, at any given time, to have up to 100 people inside our coffee shop. If we ever reach more than that 100-person limit, we are unable to accept this traffic, and thus a denial of service comes into action. Our coffee shop is busy handling the 100 people and cannot accept any more people. You may ask yourself how many people these attackers can simulate in a DDoS attack. Thousands, if not tens of thousands. From my time in this scene, I saw attacks that ranged anywhere from 500 Mbits per second all the way up to 60 Gbits per second.
IP Booters ? The Dangerous Area of the Internet
IP booters, also known as IP stressers, are services that were brought to life in the early 2010s and gained huge traction for the ease of accessibility. These services allowed for anyone to initiate DDoS attacks by renting someone else?s infrastructure for a cheap monthly rate ? some as cheap as $2.
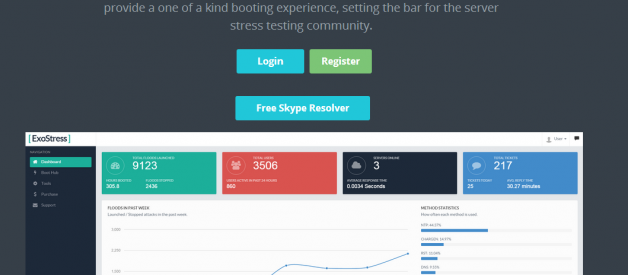
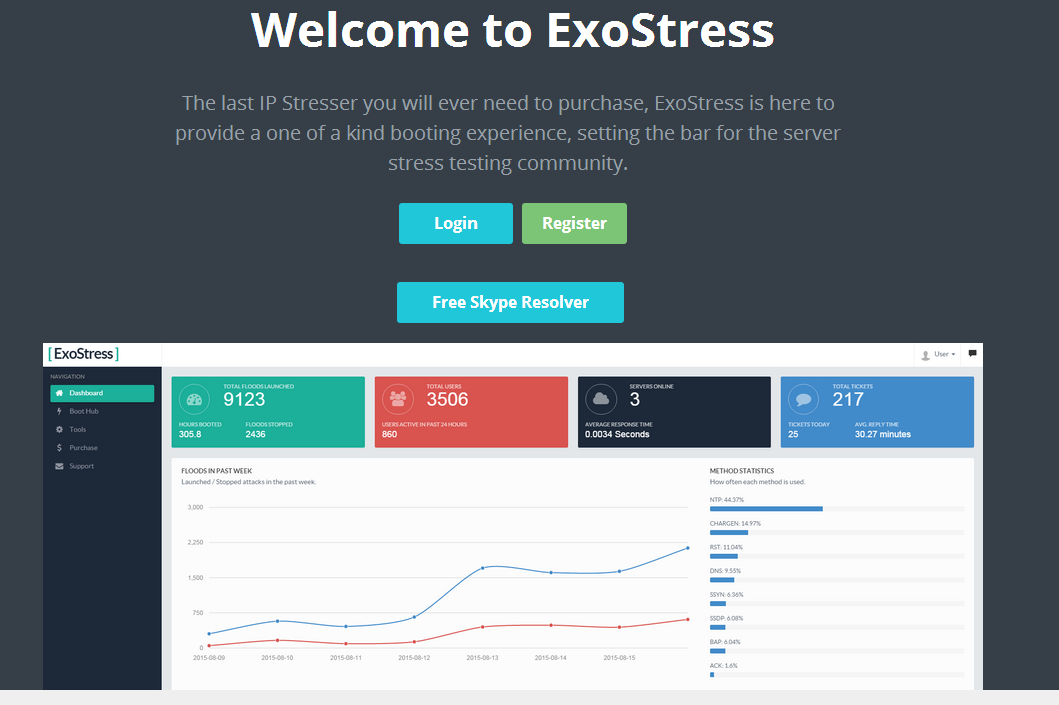 ExoStress ? A popular DDoS for hire service from 2015
ExoStress ? A popular DDoS for hire service from 2015
At the time, these services were publically accepting PayPal and credit card payments. It was not until early 2017 that PayPal was able to completely eliminate these transactions from happening. Booter owners would spoof their incoming PayPal transactions with a whitehat business. (This is another topic that I will end up talking about in its own dedicated article.)
Obtaining IP Addresses
The question of obtaining infrastructure is now answered, but how would people be able to gather IP addresses? The answer is quite simple. These IP stresser services provide not only infrastructure but also tools that can assist the customer in obtaining IP addresses, whether that be for a game server, website, or person. These services catered to all sorts of different audiences.
Simply enter the target?s IP address, the port, how long you wanted the attack to last, which network protocol you want to use for your attack, and press Start. It was really that easy.
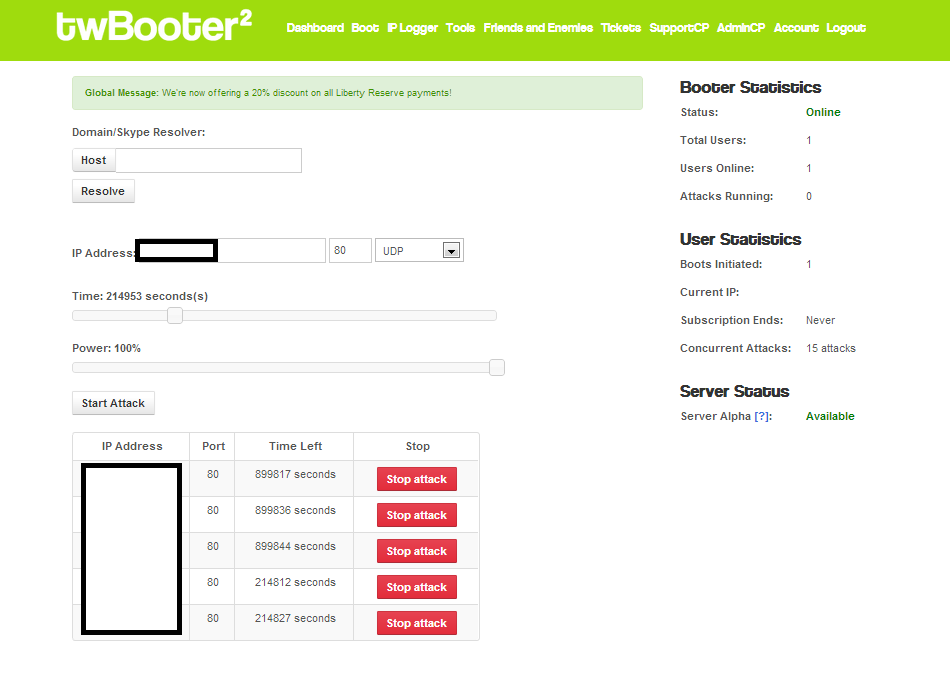
Skype resolvers
During this time on the internet, Skype was an extremely dominant chat service. And at the same time, there existed a security vulnerability that, due to the P2P nature of the application, allowed people to grab the IP address associated with a Skype account. This was originally discovered in 2012. People eventually ended up offering Skype resolver services, where users could enter a person?s Skype username and a back-end service would grab the victim?s IP address.
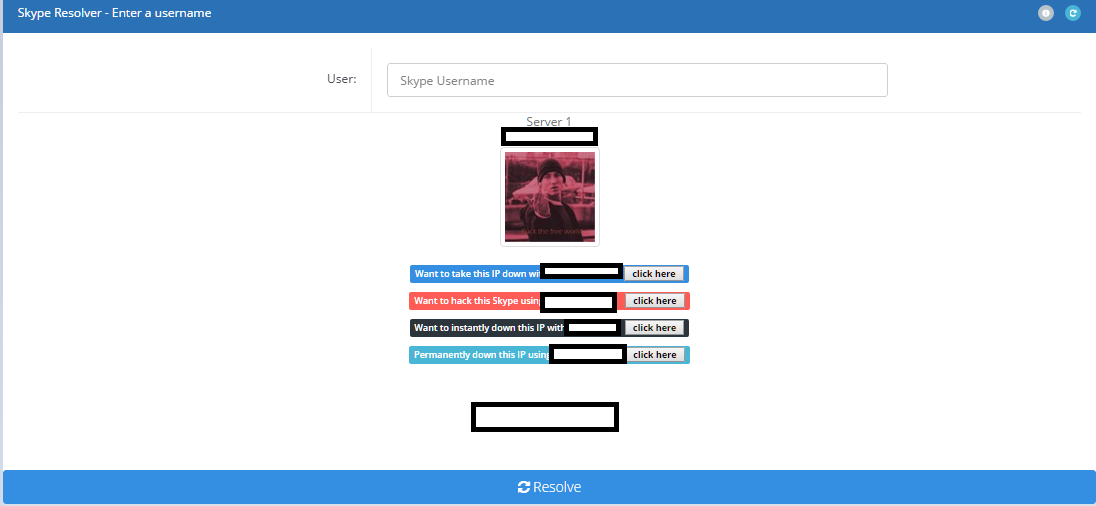 One of the many Skype resolvers that were publically available
One of the many Skype resolvers that were publically available
These Skype resolver services ended up offering paid API subscription services that were primarily sold to IP stresser owners so that they could create their own Skype resolver page on their booter. The end goal for these booter owners was to assist the customer in obtaining their target?s IP address. What the craziest part of this all to me was for how long this vulnerability actually existed. It was not until early 2016 when Microsoft?s Skype team released a blog addressing the issue.
IP grabbers
Another popular way of grabbing people?s IP addresses was to use something quite literally called an IP grabber. Booter owners would offer this service, which creates a URL that looks legitimate. When anyone clicks on the link, their IP address is logged so that the customer can use it however they want.
Typically, booter owners would utilize a redirect URL service such as TinyUrl to mask their IP grabber. Some, though, would go to the extent of buying similar domain names to popular websites, such as Imgur or Reddit, and let customers have access to IP grab through those domains. The primary purpose of these grabbers was to look like a normal URL so that users would click without thinking.
Conclusion
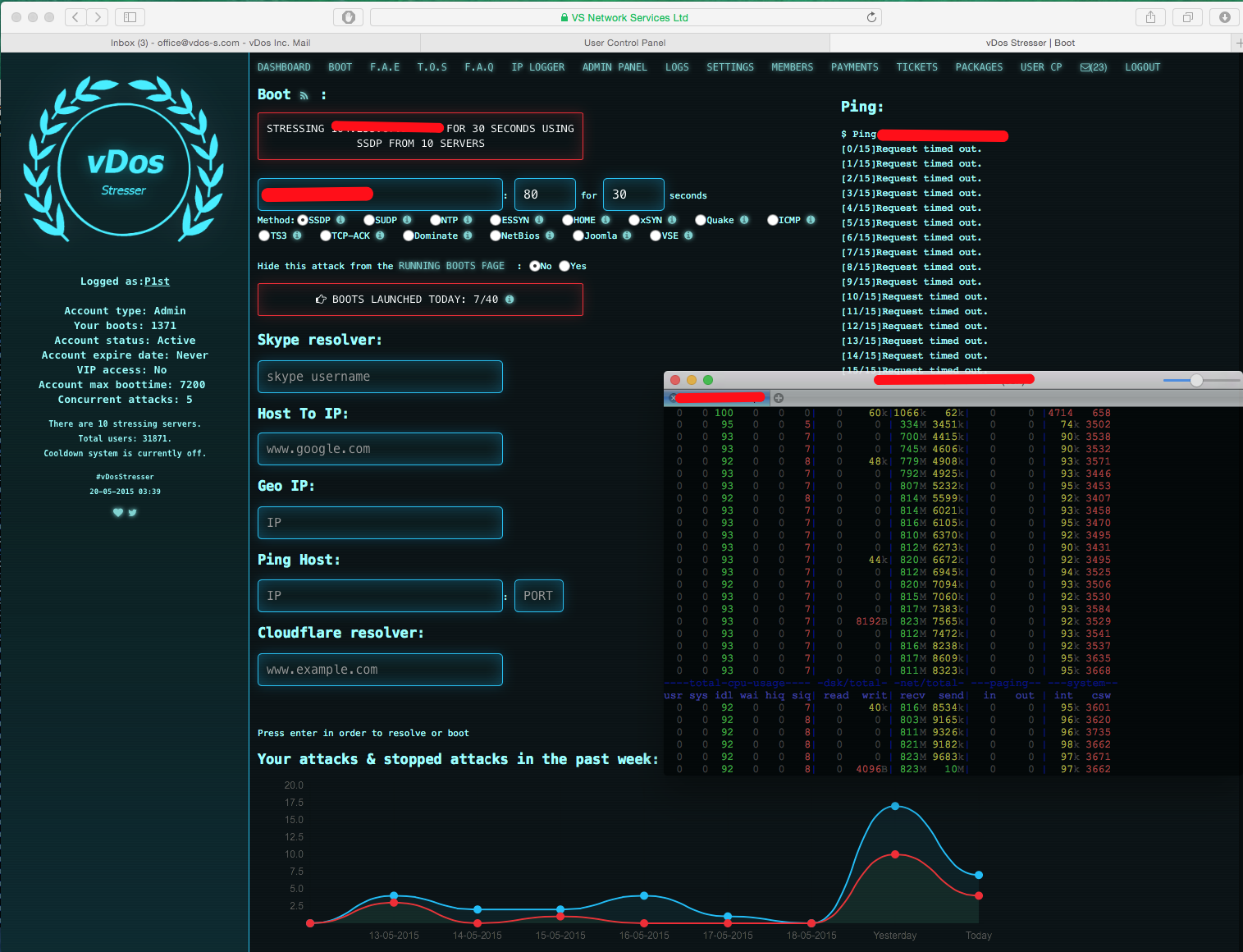 vDos Stresser ? A popular booter service that ran from 2012?2016
vDos Stresser ? A popular booter service that ran from 2012?2016
While booter services caused a lot of disruption and caused a lot of bad, they assisted in the progression of online security and created a demand for security protection from companies such as Cloudflare, OVH, Sucuri, and Akamai.
Even though the reign of booter services and Skype resolvers has now died, there still exists a small subset of DDoS services that actively run. Whenever on the internet, it never hurts to be connected to a VPN, but more importantly, always use common sense when browsing the internet.