TubeMate is a most popular app used for downloading online-content which are posted on the hosting platforms like YouTube, Facebook, Instagram, Twitter, Dailymotion, Youku, Vimeo, MetaCafe, Google, Naver TV, Kakao TV, Mango TV etc?
TubeMate allow us to login to the various hosting platform to download the online contents mainly videos.
Though TubeMate has irresistible features yet it is not hosted in play store or apple store, Do you know Why?
Because TubeMate has lots of loopholes like,Bad Certification, Hardcoded key, Man In The Middle attack (MITM), SQL Injection, Incorrect Default permissions, Cross Frame Scripting (XFS) & UI Misrepresentation, developer?s email credentials has been breached already and hosted on darknet sites.
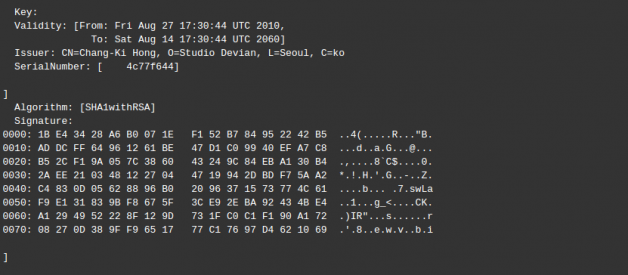
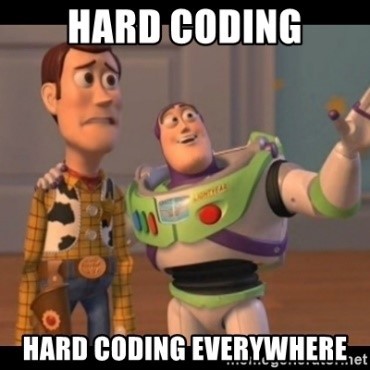
1.Bad certification: Tubemate does not have SSL certificate which is very much mandatory for the web app that includes login page. This application is signed with `SHA1withRSA`. SHA1 hash algorithm is known to have collision issues. RSA certification is officially depreciated.
2. Hardcoded key (CWE-312) : Hardcoded key means application stores sensitive information in cleartext within a resource that might be accessible to another control sphere(Like storing API key in the client side). Due to hard code key TubeMate send your credentials to the server and it has bad certificate i.e., SHA1withRSA which has collision issue. So if the hacker sniffs your packets then he can easily trace your credential details.
WHY IS THIS A SECURITY THREAT?
These hardcoded credentials pose a huge security risk cause as the company may assure the users about their security sophistication but the credentials are hardcoded and the attacker can decrypt these apps in order to get to know the hardcoded credentials and be able to sniff and decrypt all the encrypted traffic from the app
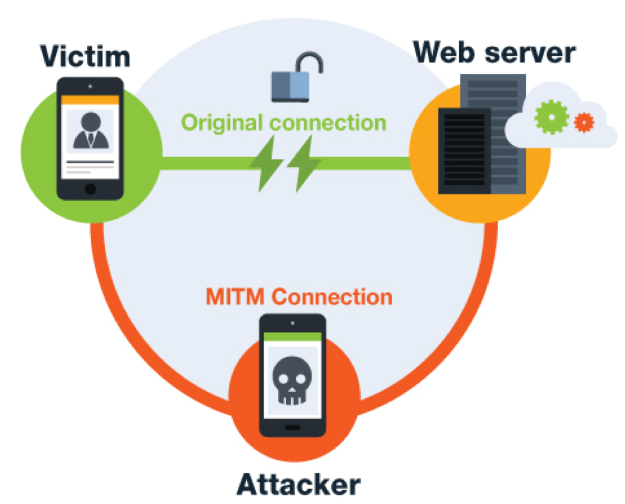
3. Man In The Middle Attack (CWE-295): Though it has week certification so Insecure WebView Implementation occurs and ignores SSL Certificate errors and accepts any SSL Certificate. Due to this loophole application is vulnerable to MITM attack. Using this the attacker may be able to sniff the plaintext data and if thats encoded he can decode that using the hard-coded keys.
4. SQL Injection ( CWE-89): TubeMate uses SqLite Database and executes the raw SQL query. Unvalidated user input in raw SQL queries can cause SQL Injection. Also, sensitive information should be encrypted and written to the database.

5. Incorrect Default permissions (CWE-276): TubeMate request for permission to access GPS and information about background task which may lead to discovering private information about other applications due to the vulnerability present in the application like Man In The Middle attack. And it is also a privacy breach since it is accessing the device GPS location.

6. Cross Frame Scripting(XFS) & UI Misrepresentation (CWE-79, CWE-451): Application lists domains that are known to generate spam, host botnets, create DDoS attacks, and generally contain malware. This application has 2 domain malwarea. URL: www.airbornehydrography.comIP: 194.9.95.65For more info: https://cymon.io/194.9.95.65
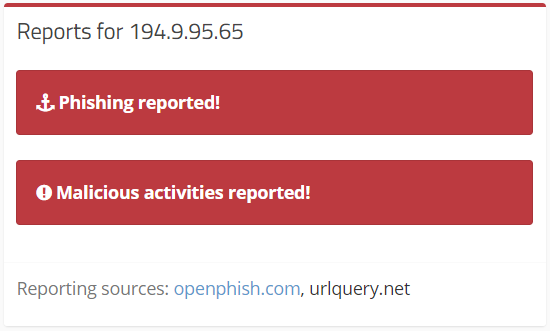 IP Found in Malware DB
IP Found in Malware DB
b. URL: www.ceisystems.itIP: 178.212.142.108For more info : https://cymon.io/178.212.142.108
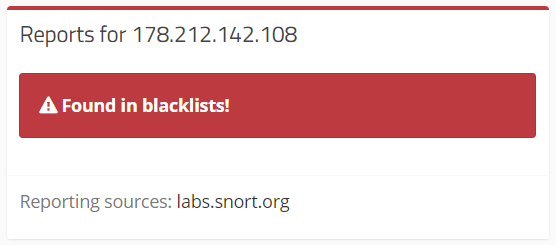 IP found in Malware DB
IP found in Malware DB
By these 2 IP addresses which has bad reputation of hosting a phishing pages, hence this TUBEMATE App is vulnerable to Cross Frame Scripting(XFS)
7. The Developer?s email i.e., [email protected] been breached already and hosted on darknet sites.
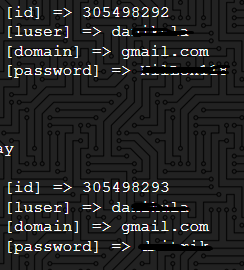
These vulnerabilities are found using Cybersafe Bangalore?s Proprietary tool.
TubeMate having these many vulnerabilities, use this with your own risk!!. My suggestion is to not use this application until developer release patches to those vulnerabilities.Would you like to still use TubeMate????? Let me know on @Janardhanas369
References:https://cymon.iohttps://www.apkmirror.com