Anyone can publish on Medium per our Policies, but we don?t fact-check every story. For more info about the coronavirus, see cdc.gov.
You gotta love teens. You tell them, ?don?t download sketchy stuff?, and they do it anyways. Why is it that they think someone would spend lots of time and money creating a nice-looking website for illegal movie downloads? Out of the goodness of their heart ? or to run a scam?
 Here sucker sucker?
Here sucker sucker?
So of course, my teen ignored my advice and got the SearchMine virus/malware embedded into his Google Chrome instance on his Mac. SearchMine is super dangerous because it insert search results to malicious websites that have you install more malware to steal data, encryption your hard drive for ransom, and more.
 The gateway to digital hell
The gateway to digital hell
SearchMine is also one check of a tough virus to remove.
Why is SearchMine hard to remove?
Here?s what I tried, to no avail:
- Removed Chrome completely, by doing into Terminal and running sudo rm -rf on everything I could find on Stackoverflow and SuperUser and Google Chrome and Chromium forums that was even vaguely related to Google Chrome, removing profiles, etc.
- Ran Malwarebytes and Bitdefender. Bitdefender found nothing, but Malwarebytes found the SearchMine virus pretty quickly. I removed it, ran all the above Terminal commands again to fully remove Chrome just to be sure, and rebooted.
- Reinstalled macOS Catalina.
But none of this worked. Crazy.
As I type this, I?ve given full disk access to Terminal, and am in the process of running:
sudo grep -i -r searchmine /sudo grep -i -r anysearch /sudo grep -i -r mycouponsmart /sudo grep -i -r profile.json /
? to see if there?s something that turns up that the virus checkers don?t find. For those not familiar, here?s that these commands are doing:
- sudo ? run as superuser, i.e., with extra privileges
- grep ? look within all files
- -i ? ignore case
- -r ? run recursively, that is, go through each directly
- searchmine ? the text to look for
- / ? start at the topmost directory
I?m also running the above grep pattern on the GUIDs that are in the Chrome profile.json that SearchMine is using.
I?ll update if something turns up. But don?t hold your breath.
Given how SearchMine keeps coming back, it feels like something that?s lodged into code that?s been covertly inserted into memory and/or firmware. It?s a tough little piece of sh@%.
But that said?
How to block SearchMine
Here?s a relatively simple hack to block this persistent little MF of a virus: edit your /etc/hosts file to map searchmine and its associated domains to your localhost. Here?s my complete /etc/hosts file:
### Host Database## localhost is used to configure the loopback interface# when the system is booting. Do not change this entry.##127.0.0.1 localhost127.0.0.1 searchmine.net127.0.0.1 searchmine.com127.0.0.1 searchmine.io127.0.0.1 anysearch.com127.0.0.1 mycouponsmart.com255.255.255.255 broadcasthost::1 localhost
If you?re not super technical, here are some simple steps to edit this:
- Go to google.com (this is important; remember, SearchMine is hijacking your search results)
- In Google?s search field, type in download vs code (assuming you don?t already have it, or some other code editor like vim)
- Install vs code per the instructions. (vs code is Microsoft?s code editor. I?m recommending it here since it?s relatively easy to use but you can still run it from the command line.)
- Go back to Google.com and search for run vs code command line
- Follow the instructions
- Run the Terminal program. (Not sure how? Go to google.com and type in how to run terminal in macos)
- Now type sudo code /etc/hosts
- Add the lines above that are missing (127.0.0.1 searchmine.net, etc.)
- Save, reboot
How the SearchMine block works
This won?t remove the SearchMine virus, but it will cripple it. Every time the SearchMine virus tries to redirect your browser to searchmine.net/.com/.io, or anysearch.com, or mycouponsmart.com, your browser will redirect that request to your laptop. (Every laptop?s Internet address is 127.0.0.1.)
Without being able to reach its server, SearchMine can?t deliver its malicious search results. You can still search with other search engines, like Google.
If SearchMine evolves ? and I?d count on it, these guys are smart ? then as they add new domains to redirect to, keep updating your /etc/hosts file.
How to get SearchMine to block itself
The makers of SearchMine really want you to access their site. So, let?s oblige them. (Note to any SearchMine folks reading this: careful what you wish for!)
On a machine where you have not changed /etc/hosts to block the SearchMine-related domains, open Terminal and paste this command in. A few dozen times. 🙂
while true; do curl -s -L –retry 1000 -H ‘Cache-Control: no-cache’ –user-agent Mozilla/5.0 –limit-rate 1k “https://www.searchmine.net/search/?asset=ds&wtguid=27232702344415973&wtmacid=f1e36c6706297c31241eed3bfb229073&wtsrc=4583&wtdt=011620&wtbr=1&wtpl=10.15.2.0&v=6.0&q=34523452389-8392380490485092348539840598234-09582340-958239-485-2390485928340-985239048539840598340-9582390-850239-852398509830958230-95830-9485023-98503909-85029348509385930-59230-59203945023952390-48504239850-23984502349859-850923-489523-9582-394582390-4852390-483995230-94582039850-3348509385930-59230-59203945023952390-48504239850-23984502349859-850923-489523-9582-394582390-4852390-483995230-94582039850-3348509385930-59230-59203945023952390-48504239850-23984502349859-850923-489523-9582-394582390-4852390-483995230-94582039850-3348509385930-59230-59203945023952390-48504239850-23984502349859-850923-489523-9582-394582390-4852390-483995230[1-10000] & ” > /dev/null ; done &
What this does is continually request search results from one of the URLs in SearchMine?s profile.json file. curl has the following flags set:
- -s : work silently, so our Terminal doesn?t have to display output, and we use less memory and CPU on our side.
- -L: follow redirects. This matters since the URL above initially yields a 302 redirect. We want SearchMine to burn up CPU, memory, and network resources to deliver an actual page.
- –retry 1000 : retry up to 1000 times if needed. Again, SearchMine really wants us to visit their page, we?ll make an honest effort.
- -H ?Cache-Control : no-cache?: ask the server not to send a cached version. Because we want to ensure we?re always seeing the latest, best content SearchMine has to offer.
- –user-agent Mozilla/5.0 : make curl look like a Google Chrome browser. Because that?s their main target browser.
- –limit-rate 1k : run really slowly, at 1kpbs, like a dial-up modem from 1989. This way we can fully savor the experience of downloading a page from SearchMine.
- > /dev/null : ignore all output so that we consume less memory on our side.
- &: run in the background, so you can paste this command into your terminal window a few dozen times
? plus it has a nice long search string that will fill up their log files nice and quick.
On the surface, this might look like a curl script. But what it really is is a persistent request for the folks at SearchMine to block your IP address from their website, thus deactivating their virus. It is also communicating that, if they don?t block you, you will be a very expensive user for them in terms of consuming server and network resources, and that it might be more economical for them to simply deactivate their virus by blocking your IP.
Because SearchMine doesn?t provide any contact information ? as evidenced by their screenshot above ? this is the only means we have of communicating with them. Of course, if SearchMine did provide contact information, where we could request that they deactivate their virus, and they complied, I would not be publishing the above script.
For these reasons, I believe these requests to SearchMine are, for United States residents, communications protected under the First Amendment.
It works!
And sure enough, after asking enough times, the good folks at SearchMine have now blocked one of my machines from accessing the malware on their website.
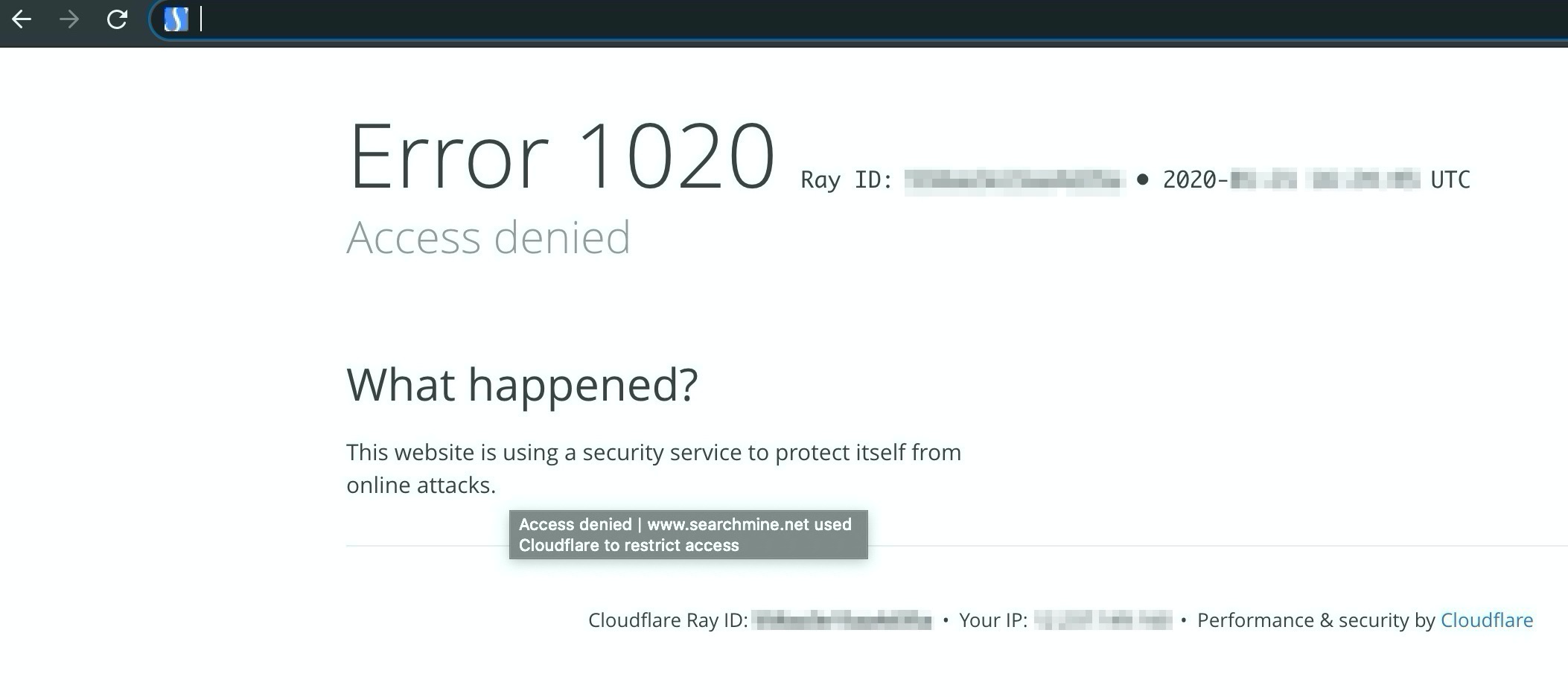 ?uncle!?
?uncle!?
How kind of them! (And thanks Cloudflare for doing business with known virus creators. Glad to see your commitment to free speech.)
Think like a virus creator
Notice I?m not giving any links in the guide above, but I?m directing you to go to Google to type in your searches. This is important! When you have a redirect virus, it?s important that you assume that the virus creators are creating fake virus removal guides that include links to sites that have you to download more malware.
You basically have to have this mindset:
 It?s from the 90s; Google it
It?s from the 90s; Google it
Think like a virus creator. And don?t be naive.
Hope this helps. And I hope that the browser makers find a way to fix this very dangerous piece of malware.


